Recover files from ESET Online Scanner quarantine (*.NQF) on Windows, Linux, and macOS.
Decryption logic is implemented directly in Python. Inspired by HexAcorn DexRAY (https://hexacorn.com/d/DeXRAY.pl
|
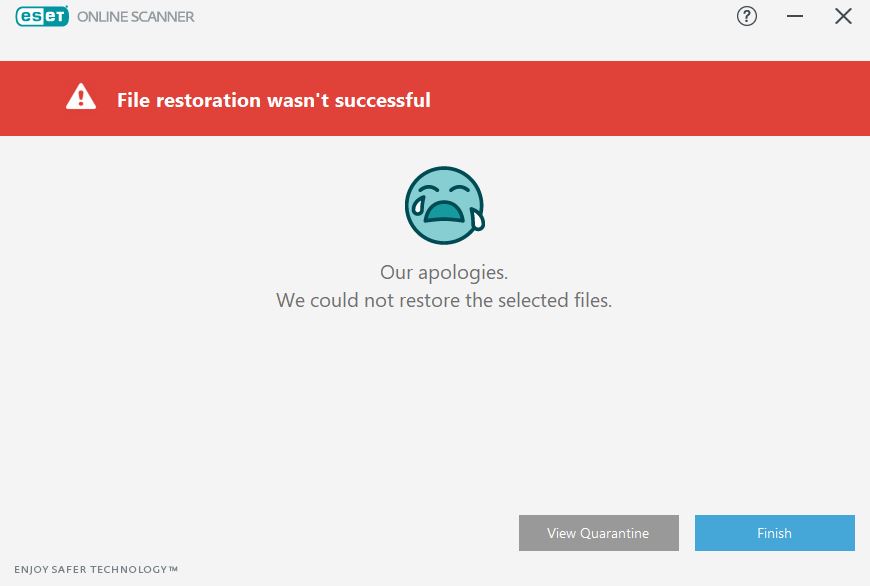
Because sometimes the AV just refuses to restore the quarantined files and, on the ESET forums, they ask people to send their files to manually decrypt them. (Example of ESET forum post Also, when you restore a file from the quarantine, the AV tries to "clean" it, therefore you can get an archive stripped down. |
- Native ESET
.NQFdecoder in Python - Cross-platform GUI (Tkinter) for ease of use
- OCR integration (optional) — auto-suggest filenames from quarantine screenshots
- Interactive file list, editable OCR names, labels for missing/duplicates, and per-file extraction toggles
- Extract output into structured folders named by quarantine hashes
I recommend using a virtual environment to keep dependencies clean.
git clone https://github.com/sorinbotirla/eset-quarantine-recovery.git
cd eset-quarantine-recoverysudo apt install python3-tk tesseract-ocr
pip install pillow pytesseract --break-system-packagesThe last version of the Tesseract OCR here or here
Add the tesseract path in User PATH environment variable. Open Settings > System > About > Advanced system settings > Environment Variables
The path you have to add in the PATH is C:\Program Files\Tesseract-OCR
Install python dependencies
pip install pillow tesseract pytesseract python eset_unquarantine_gui.py- Select in GUI: Choose your "Quarantined files folder" containing .NQF files.
- Click Scan Quarantine to populate the file list.

- Choose an "Extracted files folder".
- (Optional) Choose your OCR screenshot folder and Start OCR Scan to auto-suggest filenames.

- Edit any OCR name directly by double-clicking the cell. Press enter to accept the input value

- Click Extract Files to decrypt and extract. Outputs are organized by hash.

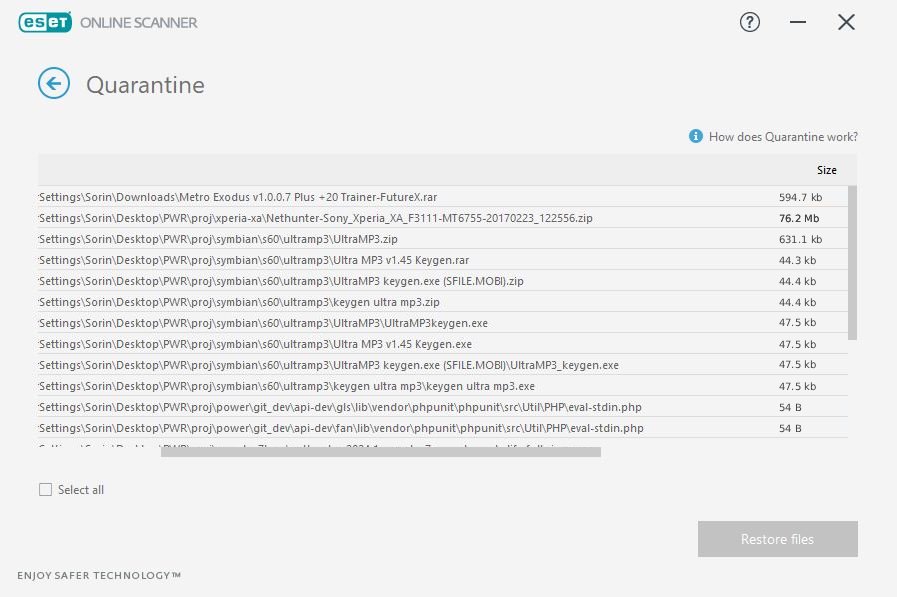
I have used OCR to read the file names and their size from the ESET quarantine screenshots. The quarantined files are stored without their original names, so the only almost-reliable way to keep tracking of the original file names was to check their size. To do that, simply screenshot the quarantine list but keep the screenshots cropped to the last part of the path (file names and their size).
You can find the ESET Online Scanner's quarantined files under
C:\Users\<YourUsername>\AppData\Local\ESET\ESETOnlineScanner\QuarantineCopy the files from the quarantine folder to another folder for convenience. You will use that folder as a source for extraction.

|

|
You can still extract them, however, the extracted file will have the extension .out
You need to check their MIME types and replace their extension with the original one eg. .zip .jpg .exe .pdf etc.
Be careful not to execute something wrong and trigger the real malware at this point. Double check what was the original file name. The .out extracted files are just the original files, but without the original names and extensions.
- OCR modules not detected: Ensure Pillow & pytesseract are installed in the same Python you run the GUI with.
- OCR binary missing: Confirm Tesseract is installed and accessible (tesseract --version).
- Tkinter errors: On Linux, you may need sudo apt install python3-tk.
- Permission issues: Select output folder where you have write access.
- OCR name truncations: Try to take clean screenshots, only capturing the file names and their size.
Distributed under the MIT License. See LICENSE.
There is a cli version which doesn't work as well as the GUI script, and also a dexray.sh bash script that downloads and uses DexRAY.pl from HexAcorn website.
Do not rely 100% on the OCR to match the file names. Check yourself if they are the right ones. Use this tool to carefully restore false positives and stay away from malware.