Sprint 5 learning and devloping skill using SIEM Tool
Defining SIEM Security Information and Event Management are solutions that monitor an organization's IT environment, relaying actionable intelligence and enabling security teams to manage potential vulnerabilities proactively. SIEM software provides valuable insights into potential security threats through a centralized collection and analysis of normalized security data pulled from a variety of systems. Think of it as a lens that sharpens your view across the big picture to help you focus your team’s efforts on where they can have the most impact, protecting your business and your customers from devastating data breaches.
How does a SIEM work? A security event is any occurrence in a IT environment that has the possibility of becoming a vulnerability, or an indication that the environment has already been exploited. Such events include unauthorized access, configuration changes, and abnormal user activity. A SIEM helps interpret these events to determine what threats pose the most risk and how they should be prioritized.
Managing Security Events Without SIEM It’s no secret that security threats are increasing, and they can come from both internal and external sources. To address these issues, IT organizations have put various systems in place to protect against intrusion and a host of different threats. The downside of these safeguards is they generate so much monitoring data that IT teams are then faced with the problem of interpreting it all to pinpoint actual problems.
SIEM helps the system analysts in:
- Provision of data from various devices and networks to gain visibility of the system.
- Detection of threats received by the organization or network system
- Investigation of irregular and abnormal activity
- Generation of security alerts for rapid responses to clear out the system from those threats.

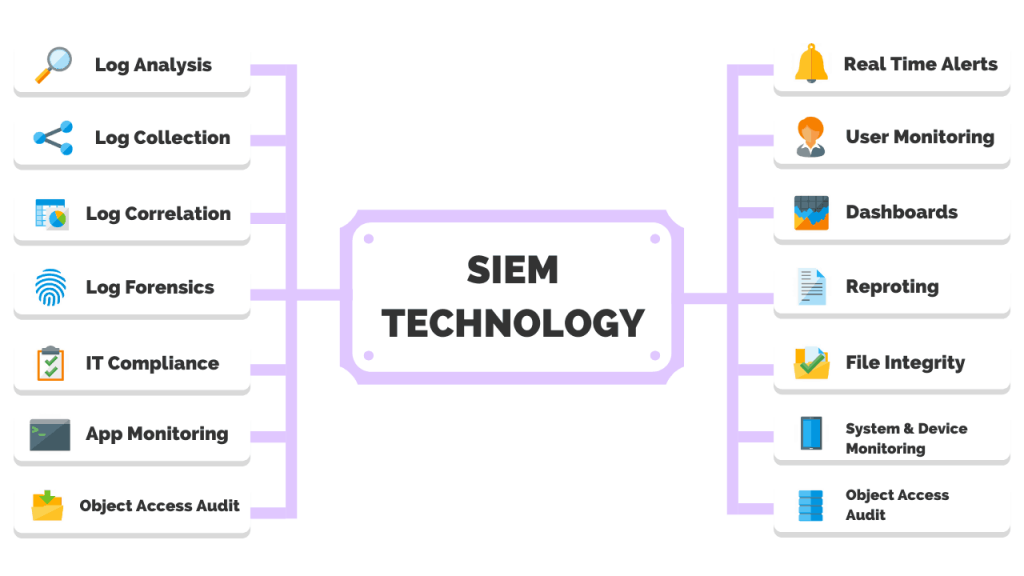
- Log Collection and Aggregation collects logs and security event data from various sources, such as network devices, servers, firewalls, intrusion detection systems (IDS), and antivirus software
- Real-Time Monitoring and Alerting monitors the collected data for security events and anomalies in real time. It applies correlation rules and analysis techniques to identify potential threats or security incidents
- Compliance and Reporting assist organizations in meeting regulatory compliance requirements by providing audit trails, logs, and reports on security events
- Threat Detection and Incident Response detect and respond to security incidents by analyzing patterns, trends, and known attack signatures. It enables security teams to identify potential threats, understand the extent of an incident, and take appropriate actions to mitigate the risk.
- Forensic Analysis and Threat Intelligence often integrate with threat intelligence feeds and databases, enhancing their ability to detect emerging threats and known attack patterns.
A SIEM (Security Information and Event Management) is a software solution that helps organizations monitor and manage their cybersecurity infrastructure. It provides a centralized platform for collecting, analyzing, and correlating security event data from various sources within an organization's network.
SIEM works by collecting logs, events, and alerts from different security systems, such as network devices, servers, firewalls, and intrusion detection systems. It aggregates this data in a centralized repository for analysis. SIEM tools employ advanced analytics, machine learning, and rule-based engines to detect patterns, anomalies, and potential security incidents.
The purpose of a SIEM is to enable real-time threat detection, incident response, and security event management. It helps organizations identify unauthorized access attempts, malware infections, data breaches, or policy violations. By correlating and analyzing events from multiple sources, SIEM tools provide a comprehensive view of an organization's security posture and help identify potential risks or vulnerabilities.
SIEM tools also provide real-time monitoring capabilities, generating alerts or notifications when they detect security events or policy violations that require immediate attention. They assist in incident response processes by providing workflow management, case management, and collaboration features. Additionally, SIEM tools often include features for compliance management, helping organizations meet regulatory requirements and providing reports and audit trails.
Overall, SIEM tools play a crucial role in enhancing an organization's cybersecurity posture by improving threat detection, incident response capabilities, and security management. They enable organizations to centralize and streamline their security operations, providing a more proactive and efficient approach to cybersecurity.
Software_Documentation/Powerpoint
- Anna @annitamaria
- Francisco @killbay