This solution uses a Terraform module to deploy SWIFT Client Connectivity in the Amazon Web Services (AWS) Cloud. It creates a standardized environment for organizations with backend payment applications that need to interface with the SWIFT financial-messaging network.
This module's default configuration follows the SWIFT Customer Security Programme (CSP) controls and the SWIFT Customer Security Controls Framework (CSCF), which comprises mandatory and advisory security controls for all SWIFT users. These templates do not replace the need for customer guidance when implementing SWIFT security controls in the cloud.
AWS is responsible for complying with certain SWIFT CSP requirements. A certificate of AWS compliance with SWIFT CSP controls is available through AWS Artifact. Certification is provided by Dixio.
AWS has also published a solution for deploying SWIFT Client Connectivity Using AWS Cloud Development Kit (AWS CDK).
Deploying this solution does not guarantee an organization’s compliance with any laws, certifications, policies, or other regulations.
This Partner Solution was developed by AWS.
This deployment requires a SWIFT account and software license. To register for a SWIFT account, refer to How to become a swift.com user?
There is no cost to use this solution, but you'll be billed for any AWS services or resources that this solution deploys. For more information, refer to the AWS Partner Solution General Information Guide.
This solution deploys into an existing virtual private cloud (VPC).
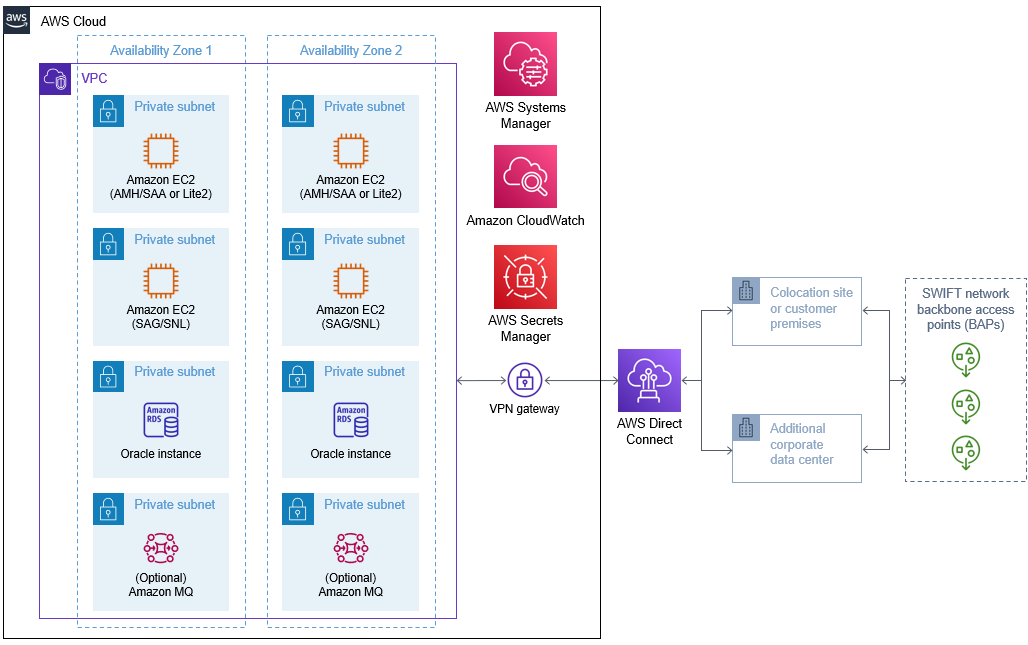
As shown in the diagram, this solution sets up the following:
- An architecture that spans two Availability Zones.
- A VPC configured with private subnets according to AWS best practices and following SWIFT CSP guidance.
- In the private subnets:
- An Amazon Elastic Compute Cloud (Amazon EC2) instance that runs Alliance Messaging Hub (AMH) and SWIFT Alliance Access (SAA) or Lite2.
- An EC2 instance that runs SWIFT Alliance Gateway (SAG) and SWIFTNet Link (SNL).
- An Amazon Relational Database Service (Amazon RDS) Oracle instance running in active or standby mode to store configuration and message data for AMH.
- (Optional) An Amazon MQ instance to handle communication for AMH.
- AWS Systems Manager, which removes the need for a jump server.
- Amazon CloudWatch, which provides the mechanism to store, access, and monitor SWIFT activities.
- AWS Secrets Manager, which encrypts, stores, and retrieves passwords.
- A virtual private network (VPN) gateway with load balancing, which connects the VPC to AWS Direct Connect.*
- AWS Direct Connect, which establishes private connectivity between AWS and data centers or colocation environments.*
*The Terraform module that deploys this solution does not include the components marked by asterisks because they require design decisions on how to connect to the SWIFT network.
- Install the latest version of Terraform. For instructions, refer to Install Terraform.
- Install the latest version of AWS Command Line Interface (AWS CLI). For instructions, refer to Installing or updating the latest version of the AWS CLI.
- Run
aws configureto configure AWS CLI with theACCESS_KEY_ID,SECRET_ACCESS_KEY, andREGIONcorresponding to your AWS Identity and Access Management (IAM) user. - Configure Terraform, and edit
variables.tfto fill in your information. - Review the resources in
main.tf, and edit as necessary with your details. - Provision the environment by running the following:
terraform initterraform apply
For more information, refer to the deployment guide for SWIFT Client Connectivity Using AWS CDK. That guide includes sections that pertain to both the AWS CDK version and the Terraform version of this solution, such as sections on connection options, specialized knowledge, security, troubleshooting, FAQ, customer responsibility, feedback, and notices.
| Name | Version |
|---|---|
| terraform | >= 1.1 |
| aws | >= 3.73.0 |
| awscc | >= 0.21.0 |
| tls | >= 3.3.0 |
| Name | Version |
|---|---|
| aws | >= 3.73.0 |
| tls | >= 3.3.0 |
| Name | Source | Version |
|---|---|---|
| amh | ./modules/ec2 | n/a |
| amh_functional_role | ./modules/iam/role | n/a |
| database | ./modules/database | n/a |
| sg_amh | ./modules/sg | n/a |
| sg_rds | ./modules/sg | n/a |
| Name | Type |
|---|---|
| aws_key_pair.generated_key | resource |
| aws_kms_key.amh | resource |
| aws_kms_key.database | resource |
| tls_private_key.example | resource |
| aws_ami.rhel | data source |
| aws_region.current | data source |
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| amh_subnet_ids | List of subnet IDs for the AMH EC2 instances. | map(object({ |
n/a | yes |
| database_subnet_ids | List of subnet IDs for the RDS database. | list(string) |
n/a | yes |
| amh_kms_key | Amazon Resource Name (ARN) to the key that's used for encrypting AMH instance volumes. | string |
null |
no |
| database_kms_key | ARN to the key that's used for encrypting the RDS database. | string |
null |
no |
| key_name | Name of the SSH (Secure Shell) key. | string |
"swift" |
no |
| secrets_key | ARN to the key that's used for Secrets Manager. | string |
null |
no |
| vpc_id | ID of the target VPC. | string |
"" |
no |
| workstation_ip_range | Range of IP addresses for administrator workstations. | string |
"10.1.0.0/16" |
no |
No outputs.