🔍 Advanced static code analysis tool for comprehensive security vulnerability detection
🚀 Installation • 📱 Web Interface • 📖 Usage Guide • 🔧 API Reference • 🌐 Languages
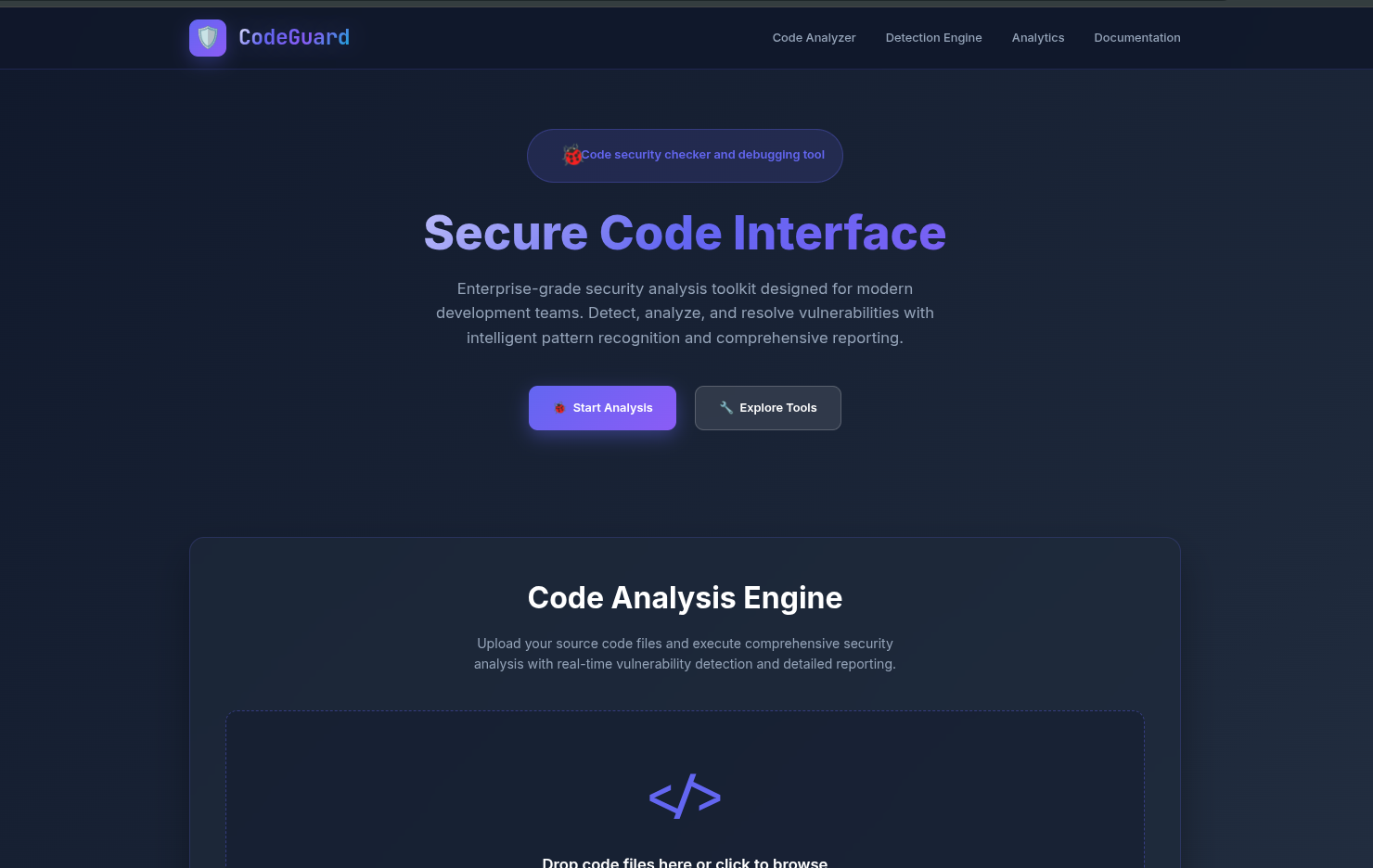
CodeGuard is a cutting-edge static code analyzer that identifies security vulnerabilities using advanced pattern matching and comprehensive code analysis across multiple programming languages.
|
|
# PowerShell
git clone https://github.com/ZeroHack01/CodeGuard.git
cd CodeGuard
# Virtual Environment
python -m venv venv
venv\Scripts\activate
# Dependencies
pip install -r requirements.txt
# Launch Scanner
python app.py💡 Access: |
# Terminal
git clone https://github.com/ZeroHack01/CodeGuard.git
cd CodeGuard
# Virtual Environment
python3 -m venv venv
source venv/bin/activate
# Dependencies
pip3 install -r requirements.txt
# Launch Scanner
python3 app.py💡 Access: |
# Ubuntu/Debian
sudo apt update && sudo apt install -y \
python3 python3-pip python3-venv git
# CentOS/RHEL/Fedora
sudo dnf install python3 python3-pip git
# Setup
git clone https://github.com/ZeroHack01/CodeGuard.git
cd CodeGuard
python3 -m venv venv
source venv/bin/activate
pip3 install -r requirements.txt
# Launch
python3 app.py💡 Access: |
# Option 1: Docker Hub
docker pull zerohack01/codeguard:latest
docker run -d -p 5000:5000 --name codeguard-scanner zerohack01/codeguard:latest
# Option 2: Build from Source
git clone https://github.com/ZeroHack01/CodeGuard.git && cd CodeGuard
docker build -t codeguard-scanner .
docker run -d -p 5000:5000 --name codeguard-scanner codeguard-scanner
# Container Management
docker stop codeguard-scanner # Stop container
docker start codeguard-scanner # Start container
docker rm codeguard-scanner # Remove container🌐 Web Interface: http://localhost:5000
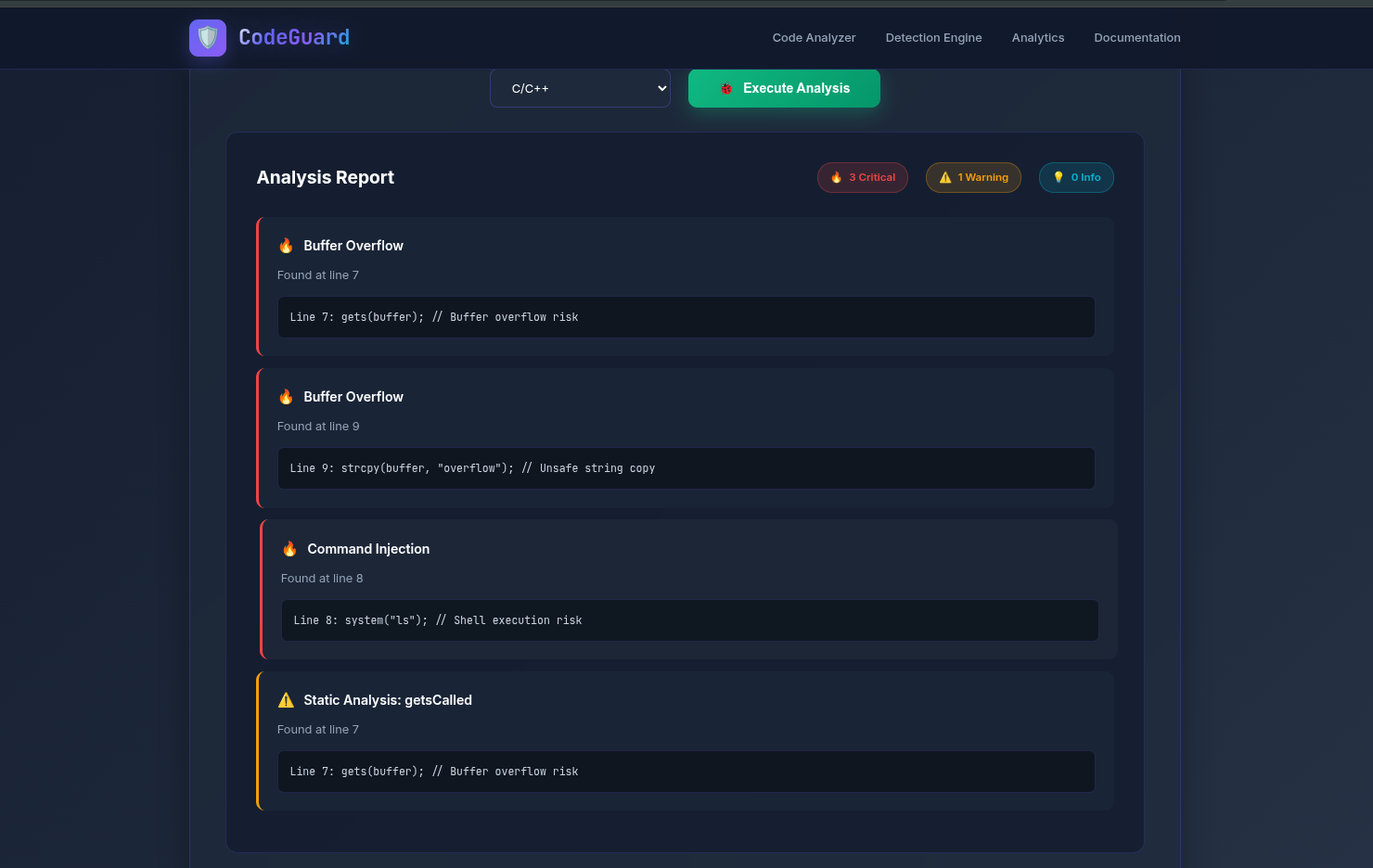
🔍 Detailed Analysis - Line-by-line vulnerability reporting with severity levels and fix recommendations
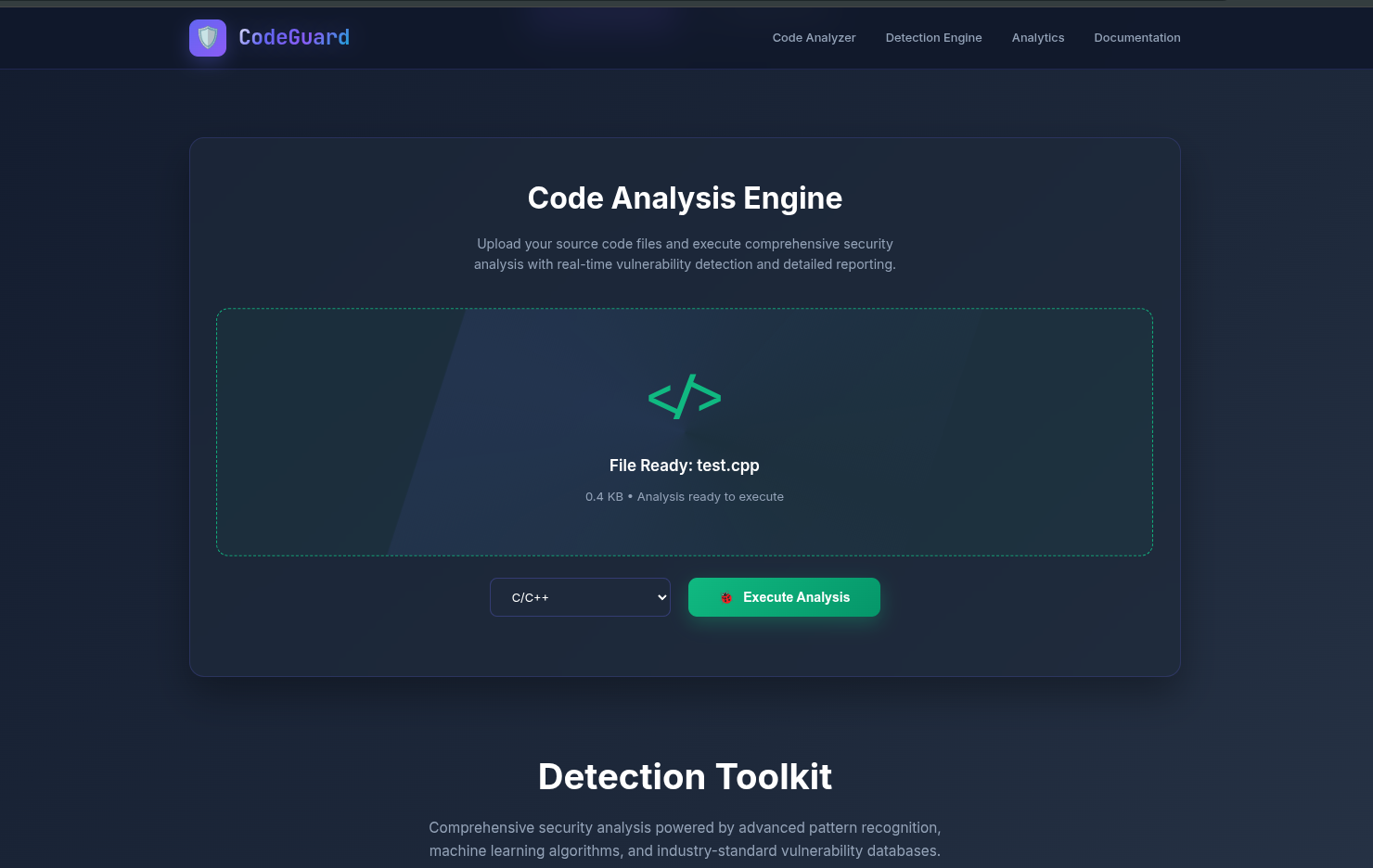
- Access via browser:
localhost:5000 - Select files for scanning
- Process vulnerability analysis
- Examine color-coded results
- Generate exportable reports
# Python Integration
from scanner import scan_file
# Single file analysis
results = scan_file('vulnerable_app.py')
for vulnerability in results:
print(f"🚨 Line {vulnerability['line']}: {vulnerability['issue']}")
print(f" Severity: {vulnerability['severity']}")# REST API Usage
curl -X POST -F "file=@security_test.py" \
-H "Content-Type: multipart/form-data" \
http://localhost:5000/api/scan| Language | Extensions | Security Patterns | Framework Support |
|---|---|---|---|
| 🐍 Python | .py .pyw .pyc |
eval(), exec(), os.system(), pickle.loads() | Django, Flask, FastAPI |
| 🟨 JavaScript | .js .jsx .mjs |
innerHTML, eval(), document.write() | React, Vue, Angular |
| ⚡ TypeScript | .ts .tsx .d.ts |
Type safety issues, XSS vulnerabilities | Angular, React TS |
| 🔵 C/C++ | .c .cpp .h .hpp |
gets(), strcpy(), malloc(), system() | Native, Qt, Boost |
| ☕ Java | .java .jar .class |
Runtime.exec(), reflection, deserialization | Spring, Struts, JSF |
| 🐘 PHP | .php .phtml .php3 |
eval(), shell_exec(), include(), mysqli | Laravel, Symfony, CodeIgniter |
| 💎 Ruby | .rb .rbw .rake |
eval(), system(), send(), constantize() | Rails, Sinatra, Hanami |
| 🐹 Go | .go .mod .sum |
exec.Command(), unsafe.Pointer, sql.Query | Gin, Echo, Fiber |
| 🌐 HTML/CSS | .html .htm .css |
Script injection, unsafe protocols | Bootstrap, Tailwind |
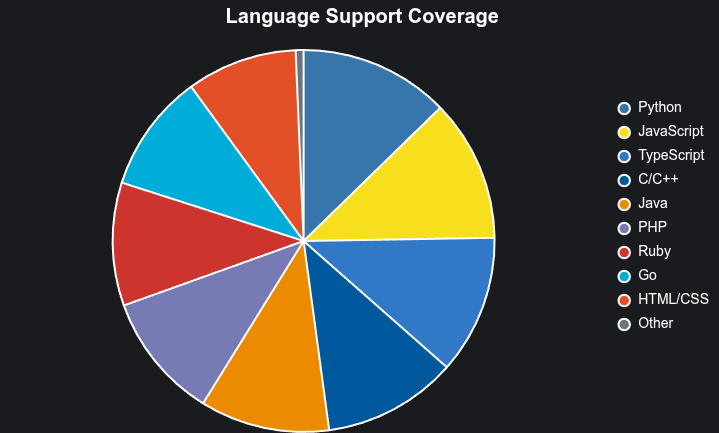
📊 Total: 9 Languages | 75+ Security Patterns | 83% Average Coverage
| Method | Endpoint | Description | Parameters |
|---|---|---|---|
POST |
/api/scan |
Upload and analyze file | file (multipart/form-data) |
GET |
/ |
Access web interface | None |
# Upload and scan a file
curl -X POST \
-F "file=@source_code.py" \
-H "Accept: application/json" \
http://localhost:5000/api/scan
# Test with vulnerable Python code
echo 'eval(user_input)' > test.py
curl -X POST -F "file=@test.py" http://localhost:5000/api/scan
# Test with hardcoded credentials
echo 'password = "admin123"' > config.py
curl -X POST -F "file=@config.py" http://localhost:5000/api/scan{
"success": true,
"filename": "source_code.py",
"language": "python",
"issues": [
{
"line": 15,
"code": "eval(data)",
"issue": "Code Injection",
"severity": "Critical"
}
],
"total_issues": 1
}🔍 Example scan results
{
"filename": "app.py",
"language": "python",
"scan_time": 0.8,
"issues": [
{
"line": 23,
"code": "eval(user_input)",
"issue": "Code Injection",
"severity": "Critical",
"description": "Dynamic code execution detected"
},
{
"line": 15,
"code": "password = 'admin123'",
"issue": "Hardcoded Password",
"severity": "High",
"description": "Credentials found in source code"
},
{
"line": 31,
"code": "os.system(command)",
"issue": "Command Injection",
"severity": "High",
"description": "System command execution risk"
}
],
"summary": {
"total_issues": 3,
"critical": 1,
"high": 2,
"medium": 0
}
}Create a test file with known vulnerabilities:
# test_vulnerable.py
api_key = "sk-1234567890abcdef" # Hardcoded credential
user_code = input("Enter code: ")
eval(user_code) # Code injection
os.system("ls " + user_path) # Command injectionExpected result: 3 security issues detected
🔧 Environment Settings
# Server Configuration
FLASK_HOST=0.0.0.0 # Bind address
FLASK_PORT=5000 # Port number
FLASK_DEBUG=false # Debug mode
# File Processing
MAX_FILE_SIZE=10485760 # 10MB limit
UPLOAD_TIMEOUT=30 # 30 seconds
# Scanner Options
SEVERITY_THRESHOLD=medium # Minimum severity to report
EXPORT_FORMATS=json,csv # Available export formats- Fork the repository
- Create feature branch:
git checkout -b feature/amazing-detection - Implement your security improvements
- Add comprehensive tests
- Commit changes:
git commit -m "Add new feature" - Push to branch:
git push origin feature/amazing-detection - Submit Pull Request
- 🐛 Bug Reports: Use GitHub Issues with detailed reproduction steps
- 💡 Feature Requests: Create GitHub Issues with enhancement label
- 🔒 Security Issues: Email mongwoiching2080@gmail.com for responsible disclosure
This project is licensed under the MIT License - see LICENSE file for complete terms.
- Flask - Web framework for the interface
- Werkzeug - WSGI web application library
- Other dependencies - See
requirements.txtfor complete list