A curated roadmap for aspiring bug bounty hunters to get started, learn effectively, and level up their skills.
Hi, I'm DARK, a Network and Information Security Engineer & Ethical Hacker. I’ve created this roadmap to help beginners navigate the complex but exciting world of bug bounty hunting. This is an open project — feel free to contribute!
⚠️ Note: The bug bounty landscape has evolved significantly. Easy vulnerabilities are now harder to find due to automation and high competition. Consistency, focus, and determination are key.
A bug is a flaw in software or hardware logic that can compromise confidentiality, integrity, or availability when exploited.
A bug bounty, or bug bounty program, is IT jargon for a reward program offered for finding and reporting bugs in a particular software product. Many IT companies offer bug bounties to drive product improvement and increase interaction from end users or clients. Companies with bug bounty programs may receive hundreds of bug reports, including security bugs and vulnerabilities, with many reporters standing to receive awards.
Rewards depend on severity and impact:
-
💵 Monetary: $50 – $50,000+
-
🎁 Swag: Apparel, badges, custom items
-
🎟️ Vouchers: Coupons, subscriptions (e.g. Netflix, Prime)
World class security researchers and bug bounty hunters are on Twitter. Where are you? Join Twitter (X) now and get daily updates on new issues, vulnerabilities, zero days, exploits, and join people sharing their methodologies, resources, notes and experiences in the cyber security world!
-
- Hacker 101
- PicoCTF
- TryHackMe (Free/Paid)
- HackTheBox (Paid)
- VulnHub
- HackThisSite
- CTFChallenge
- PentesterLab
- Flagyard
- CyberTalents
-
- PortSwigger Web Security Academy - Free, interactive web security training.
- OWASP Juice Shop - Intentionally vulnerable web app for learning.
- XSSGame by Google – XSS challenges in an interactive game format.
- BugBountyHunter (Premium) – Real-world bug bounty training platform.
- W3Challs – Security and hacking challenge platform.
-
- DVWA (Damn Vulnerable Web App) – PHP/MySQL app for testing vulnerabilities.
- bWAPP (Buggy Web Application) – Web app with over 100 web bugs.
- Metasploitable2 – Vulnerable Linux VM for pentesting
- BugBountyHunter (Premium) – Also includes downloadable labs.
- W3Challs – Some challenges can be run locally.
- NIST NVD
- MITRE CVE
- GitHub Advisory Database
- cloudvulndb.org
- osv.dev
- Vulners.com
- opencve.io
- security.snyk.io
- Mend Vulnerability Database
- Rapid7 - DB
- CVEDetails
- VulnIQ
- SynapsInt
- Aqua Vulnerability Database
- Vulmon
- VulDB
- ScanFactory
- Trend Micro Zero Day Initiative
- Google Project Zero
- Trickest CVE Repository
- cnvd.org.cn
- InTheWild.io
- Vulnerability Lab
- Red Hat Security Advisories
- Cisco Security Advisories
- Microsoft Security Response Center
- VARIoT
- Exploit-DB
- Sploitus
- Rapid7 - DB
- Vulmon
- packetstormsecurity.com
- 0day.today
- LOLBAS
- GTFOBins
- Payloads All The Things
- XSS Payloads
- exploitalert.com
- Reverse Shell generator
- HackerOne hacktivity
- Bugcrowd Crowdstream
- GTFOArgs
- shell-storm.org/shellcode
- Hacking the Cloud
- LOLDrivers
- PwnWiki
- CVExploits Search
- VARIoT
- LOOBins
- Coalition Exploit Scoring System
- WADComs
- LOLAPPS
- Living off the Hardware
- Living Off the Pipeline
-
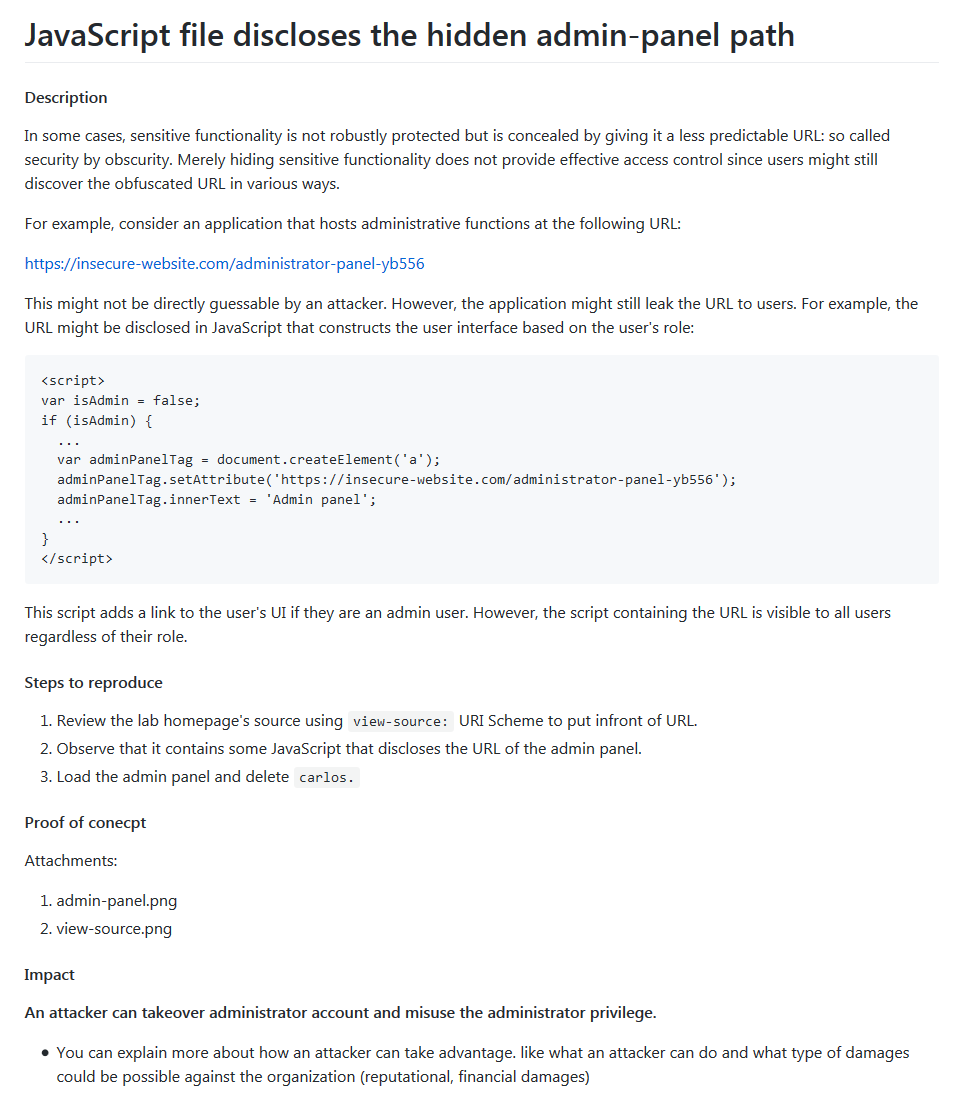
- The first impression is the last impression, the security engineer looks at the title first and he should be able to identify the issue.
- Write about what kind of functionality you can able to abuse or what kind of protection you can bypass. Write in just one line.
- Include the Impact of the issue in the title if possible.
-
- This component provides details of the vulnerability, you can explain the vulnerability here, write about the paths, endpoints, error messages you got while testing. You can also attach HTTP requests, vulnerable source code.
-
- Write the stepwise process to recreate the bug. It is important for an app owner to be able to verify what you've found and understand the scenario.
- You must write each step clearly in-order to demonstrate the issue. that helps security engineers to triage fast.
-
- This component is the visual of the whole work. You can record a demonstration video or attach screenshots.
-
- Write about the real-life impact, How an attacker can take advantage if he/she successfully exploits the vulnerability.
- What type of possible damages could be done? (avoid writing about the theoretical impact)
- Should align with the business objective of the organization
- Don’t go full-time early on. It's unstable as a primary income source.
- Keep learning. Follow experts on Twitter/X, read blogs, and watch talks.
- Focus on skill building first. Money will follow naturally.
- Avoid over-relying on tools. Develop a unique methodology.
- Try to escalate impact. Think beyond the obvious.
- Understand business risk. Not all vulnerabilities have equal value
- Engage with the community. Join forums, Discord servers, and conferences.
- Always be helpful Giving back improves your reputation.
Pull requests are welcome! Share your favorite writeups, tutorials, or tools to help grow this resource for all beginners. 👉 For more details on how to contribute, please check out our CONTRIBUTING.md guide.