by Nikhil Raj A
In AWS (Amazon Web Services), Elastic Compute Cloud (EC2) instances are widely used for running applications, websites, and services. However, one common issue many users face is forgetting to shut down unused instances — leading to unnecessary billing.
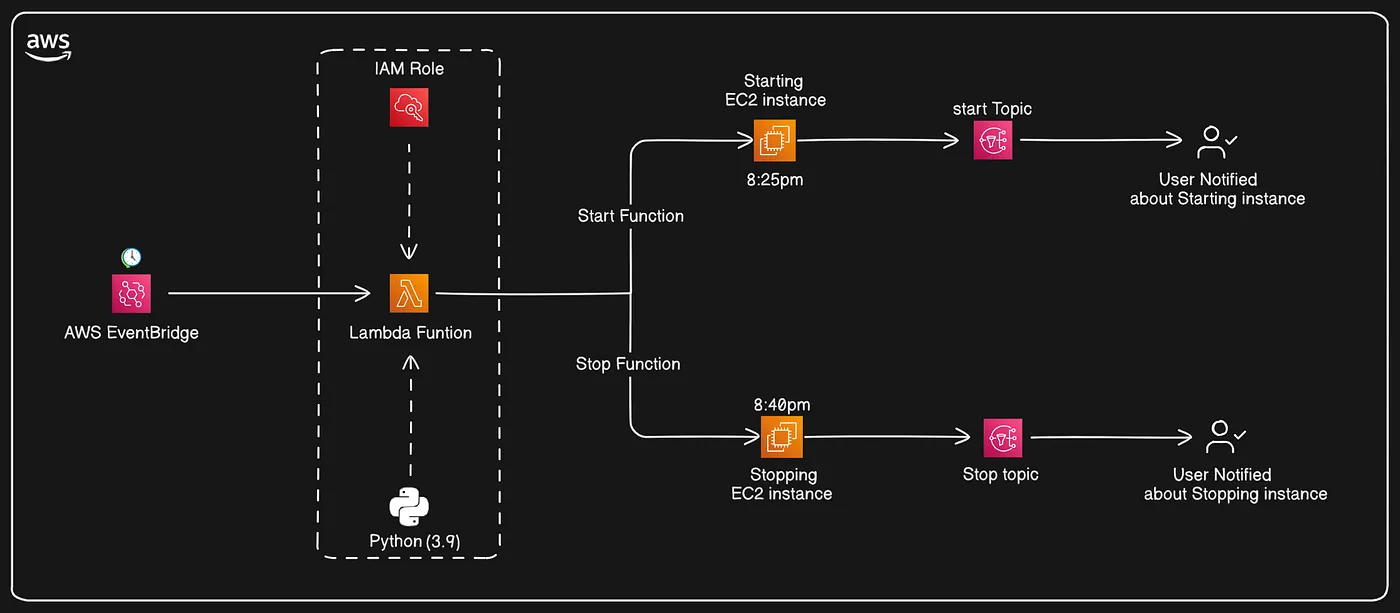
This project solves that problem by automatically shutting down idle EC2 instances if they remain inactive for more than 5 minutes and notifying the user instantly via email or SMS. By integrating AWS CloudWatch, Lambda, and SNS, we can build an intelligent, self-managing solution that minimizes costs and ensures no resource goes wasted.
Whether you’re a solo developer, startup, or enterprise team, this mini project is a simple but powerful way to automate your cloud operations and improve cost efficiency.
AWS Lambda is a serverless compute service that allows you to run code without provisioning or managing servers. You simply upload your code, set up a trigger (like an alarm or event), and AWS automatically runs the code for you when needed.
Amazon EC2 (Elastic Compute Cloud) is a web service that provides resizable computing capacity in the cloud. Think of EC2 as a virtual computer where you can run applications, host websites, or perform any tasks you would normally do on a physical server.
Amazon SNS (Simple Notification Service) is a fully managed messaging service that enables you to send notifications to users or other systems. It can send messages via email, SMS, or push notifications.
- AWS Account
- Gmail Account
- Go to AWS Management console .
- Create a IAM policy and provide EC2 , SNS and also Logs Permissions . Then click on “create policy”
{
"Version": "2012-10-17",
"Statement": [ {
"Effect": "Allow",
"Action": [ "logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents"
],
"Resource": "arn:aws:logs:*:*:*"
},
{
"Effect": "Allow",
"Action": [ "ec2:Start*",
"ec2:Stop*"
],
"Resource": "*"
}
]
}
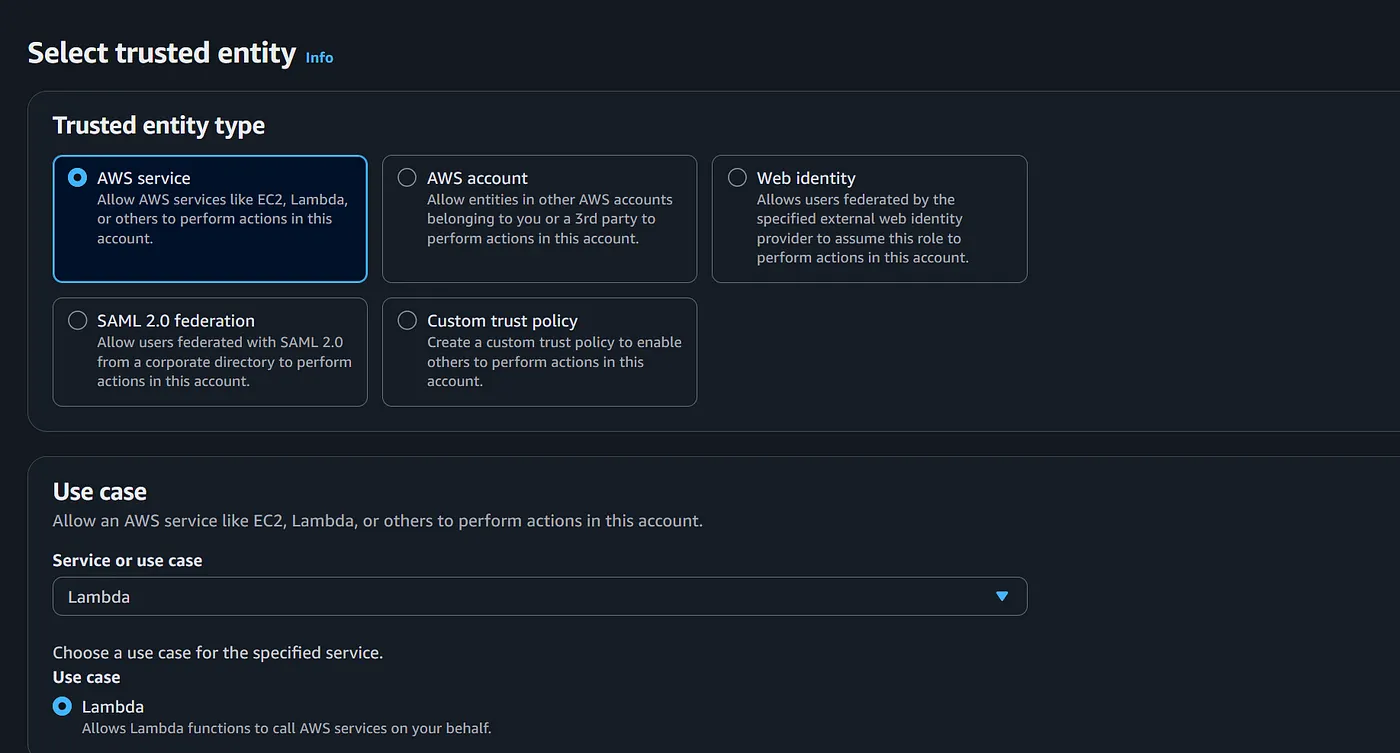
- Create a IAM Role by clicking on the “create role” and attach that policy to that newly created role. Select Trusted entity type as “AWS Service” and also Select use case as “Lambda”
- Select and attach the policy that you have created, then click on “create role” . A role would be created with the desired permissions required .
- Go to AWS Services → Lambda and click on ‘Create function’.
- Choose an Author from scratch
- Under Basic information, enter the following information: For Function name, enter a name that identifies it as the function that’s used to stop your EC2 instances. For example, “stopec2”.
- For Runtime, choose Python 3.9
- Under Permissions, expand Change default execution role
- Under the Execution role, choose to Use an existing role
- Under Existing role, choose the IAM role that you created
- Choose Create function
- After creating the Lambda Function, go to → Under Code, Code source, copy and paste the below Python code.
import boto3
from datetime import datetime
# Configuration
region = 'ap-south-1'
instances = ['i-036bb14d2a7a28941']
sns_topic_arn = 'arn:aws:sns:ap-south-1:530424100396:stopec2' # Replace with your actual SNS topic ARN
# Create clients
ec2 = boto3.client('ec2', region_name=region)
sns = boto3.client('sns', region_name=region)
def lambda_handler(event, context):
# Stop the instance
ec2.stop_instances(InstanceIds=instances)
print('Stopped your instance: ' + str(instances))
# Prepare and send SNS notification
timestamp = datetime.now().strftime('%Y-%m-%d %H:%M:%S')
message = f"EC2 instance {instances[0]} was stopped at {timestamp}."
sns.publish(
TopicArn=sns_topic_arn,
Subject="EC2 Instance Stopped",
Message=message
)
return {
'statusCode': 200,
'body': message
}
Replace instance — id with your instance id and provide the region which your instance is been running .
- Aftering altering the code , then click on “Deploy” for deploying the code .
- Repeat the steps from 1–9 , but in this function you need to change the code . Because this code used for starting the EC2 instance .
import boto3
from datetime import datetime
# Configuration
region = 'ap-south-1'
instances = ['i-036bb14d2a7a28941']
sns_topic_arn = 'arn:aws:sns:ap-south-1:530424100396:startec2' # replace with your actual SNS topic ARN
# Clients
ec2 = boto3.client('ec2', region_name=region)
sns = boto3.client('sns', region_name=region)
def lambda_handler(event, context):
ec2.start_instances(InstanceIds=instances)
print('Started your instance: ' + str(instances))
# Compose notification
timestamp = datetime.now().strftime('%Y-%m-%d %H:%M:%S')
message = f" EC2 instance {instances[0]} started at {timestamp}."
# Send notification via SNS
sns.publish(
TopicArn=sns_topic_arn,
Subject='EC2 Instance Started',
Message=message
)
return {
'statusCode': 200,
'body': message
}
- Click on “Deploy” for deploying the code . And you may also click on “test” for testing the code manually for checking the code performance .
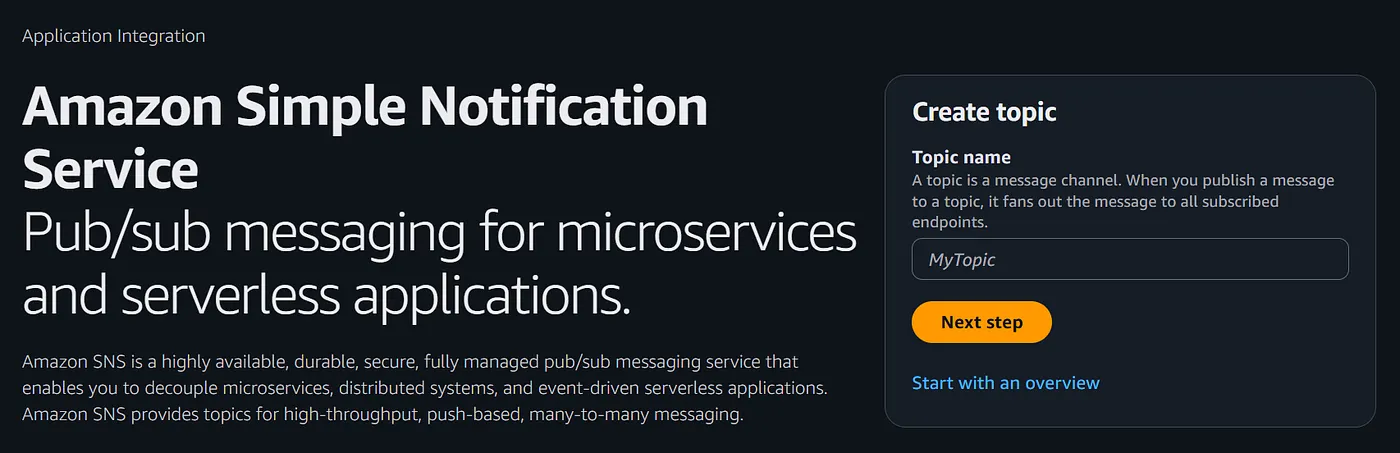
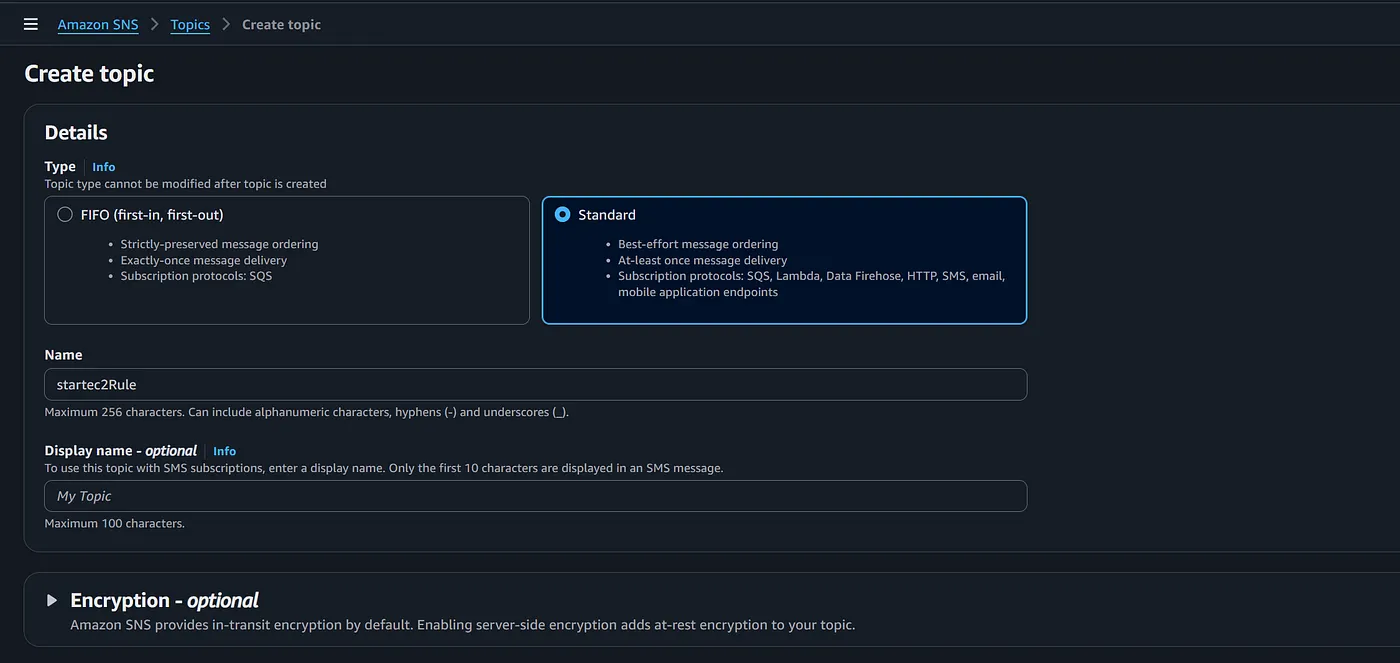
- Click on “Next Step” and provide the details like name and type of the SNS . Then click on “create topic”
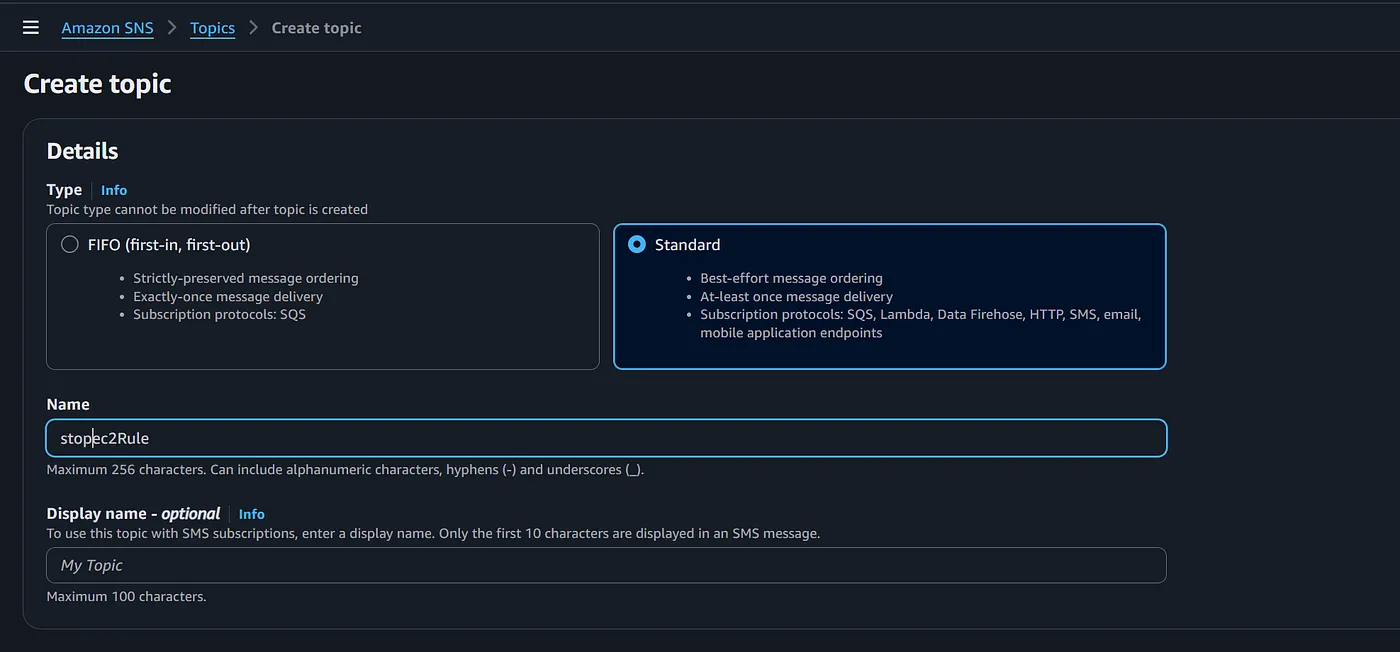
- Create another topic with “standard” as its type and also Provide the name as “stopec2rule” . Click on “create topic”
-
After creation of the topics , create subscription for both the topics . Where you need to provide the type of the notifications to be received like “Email , SMS or Email Json” etc . Provide your mail — id if you wanna be notified via mail .
-
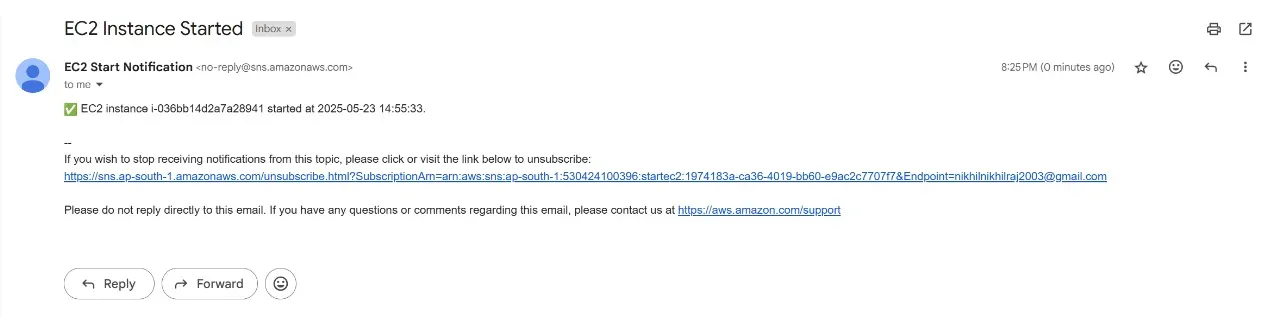
Later a Mail will be sent to your EMail for confirming the subscription, so that the notifications will be forwarded to the email which you have confirmed .
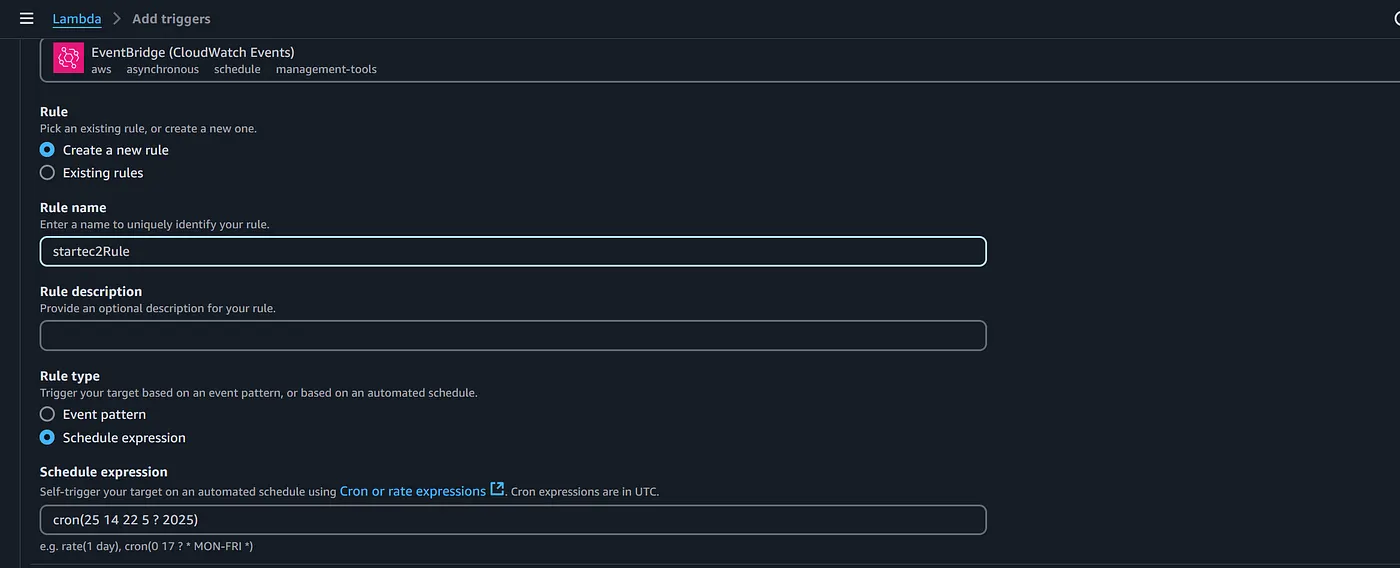
- Go to the Lambda Function(startec2) and click on “add Trigger” .
- Select “EventBridge(cloudwatch Events)” as the trigger and provide the details .
- create a new rule and provide a name(startec2rule) for the rule .
- Select “schedule expression” as rule type.
- Provide the schedule expression in the “cron” format . I have given a cron expression where the EC2 instance must start running at 8:25pm of 23 may 2025 . You can also the cron expression based on your comfort.
- click on “Add” for adding a trigger .
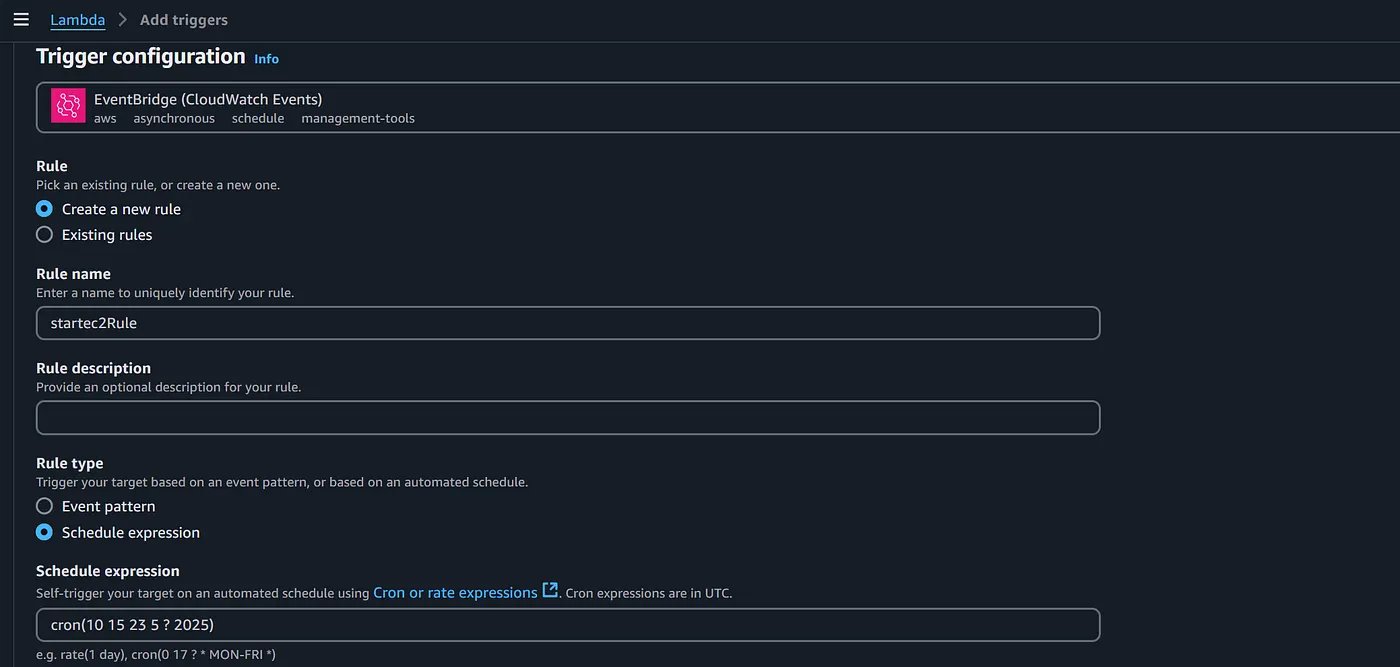
- Repeat the steps from 1–4 , in the 5th step you need to add a different cron expression for stopping the ec2 instance .
- Provide the schedule expression in the “cron” format . I have given a cron expression where the EC2 instance must stop running at 8:40 pm of 23 may 2025 . You can also the cron expression based on your comfort.
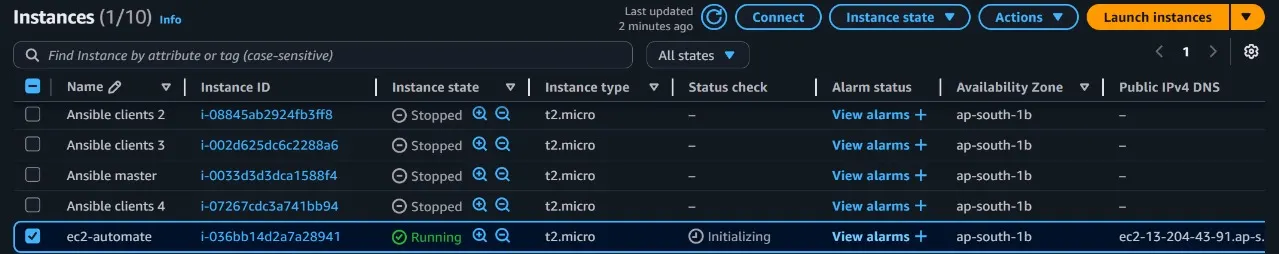
Starting of the EC2 instance and getting notified about the starting of the instance.
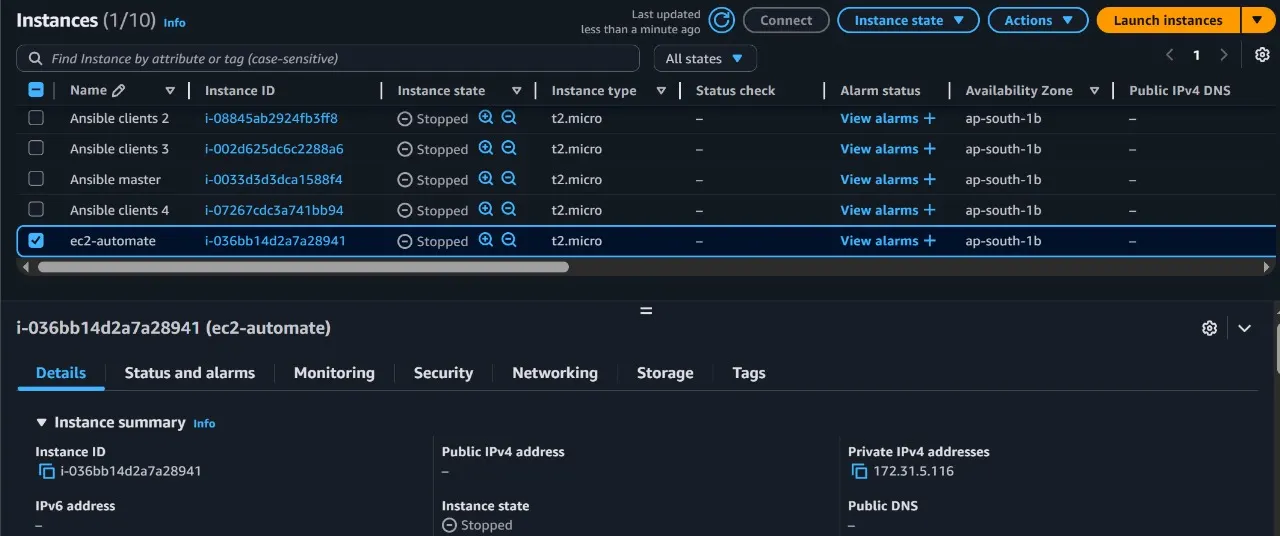
Stopping of the EC2 instance and getting notified about the Stopping of the instance.
By scheduling start and stop actions through cron expressions, the instance operates only when needed, optimizing cost and efficiency. SNS notifications ensure real-time alerts on each action. The project is simple, cost-effective, and a great example of using AWS services to automate cloud operations.