You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
Copy file name to clipboardExpand all lines: README.md
+9-75Lines changed: 9 additions & 75 deletions
Original file line number
Diff line number
Diff line change
@@ -56,81 +56,15 @@ For other Cloud providers check: [GCP](https://github.com/sysdiglabs/terraform-g
56
56
If you're unsure about what/how to use this module, please fill the [questionnaire](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/blob/master/use-cases/_questionnaire.md) report as an issue and let us know your context, we will be happy to help and improve our module.
57
57
58
58
- There are several ways to deploy this in you AWS infrastructure, gathered under **[`/examples`](./examples)**
59
-
-[Single Account on ECS](#--single-account-on-ecs)
60
-
-[Single Account on AppRunner](#--single-account-on-apprunner)
61
-
-[Single-Account with a pre-existing Kubernetes Cluster](#--single-account-with-a-pre-existing-kubernetes-cluster)
62
-
-[Organizational](#--organizational)
63
-
- Many module,examples and use-cases provide ways to **re-use existing resources (as optionals)** in your infrastructure (cloudtrail, ecs, vpc, k8s cluster,...)
64
-
- Find some real self-baked **use-case scenarios** under [`/use-cases`](./use-cases)
59
+
-[Single Account on ECS](./examples/single-account-ecs/README.md)
60
+
-[Single Account on AppRunner](./examples/single-account-apprunner/README.md)
61
+
-[Single-Account with a pre-existing Kubernetes Cluster](./examples/single-account-k8s/README.md)
Sysdig workload will be deployed using AppRunner in the same account where user's resources will be watched.<br/>
77
-
More info in [`./examples/single-account-apprunner`](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/tree/master/examples/single-account-apprunner)
78
-
79
-
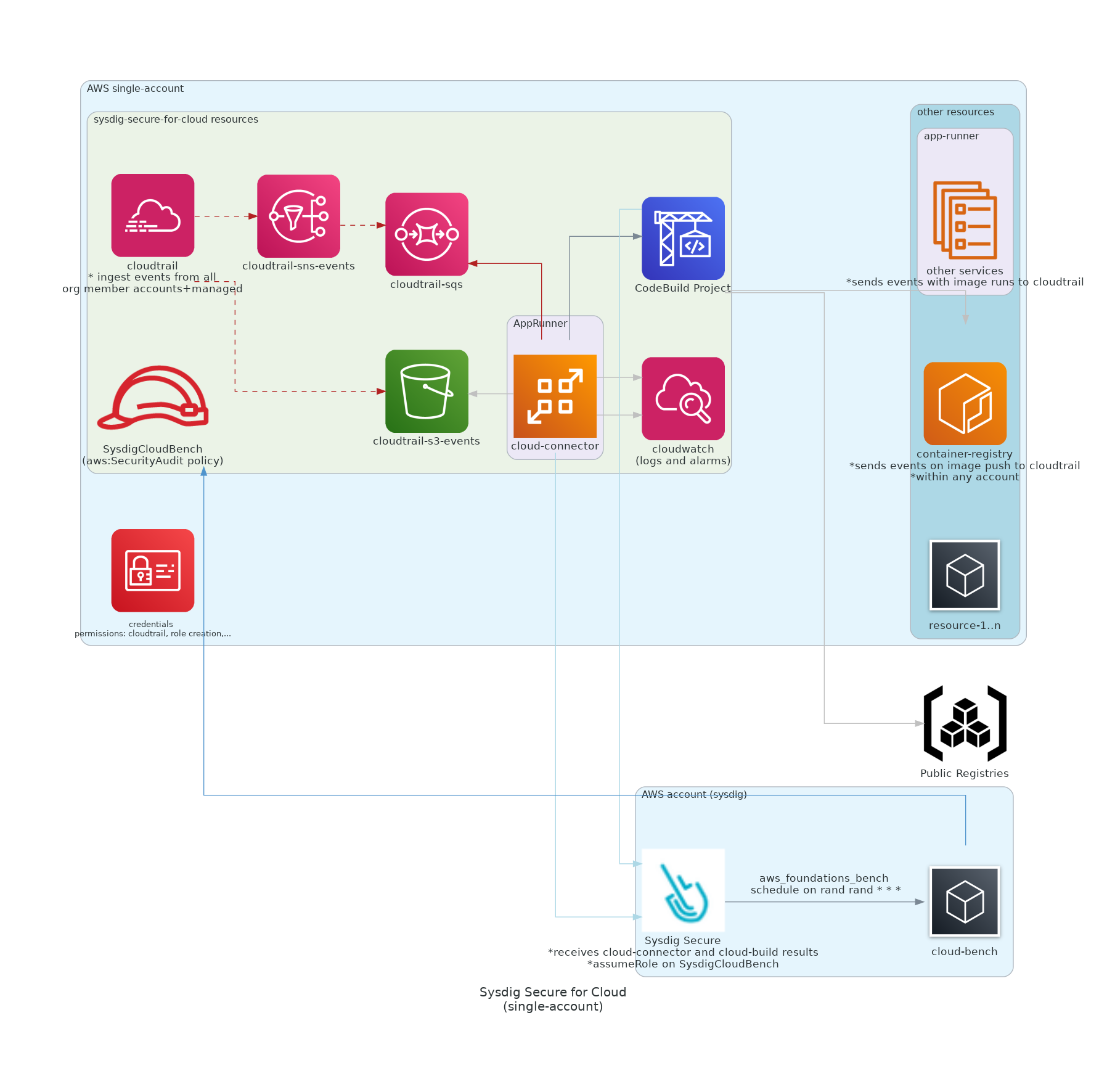
80
-
81
-
### - Single-Account with a pre-existing Kubernetes Cluster
82
-
83
-
If you already own a Kubernetes Cluster on AWS, you can use it to deploy Sysdig Secure for Cloud, instead of default ECS cluster.<br/>
84
-
More info in [`./examples/single-account-k8s`](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/tree/master/examples/single-account-k8s)
85
-
86
-

87
-
88
-
### - Organizational
89
-
90
-
Secure all the accounts from your organization<br/>
91
-
More info in [`./examples/organizational`](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/tree/master/examples/organizational)
If no [examples](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/tree/master/examples) fit your use-case, be free to call desired modules directly.
98
-
99
-
In this use-case we will ONLY deploy cloud-bench, into the target account, calling modules directly.
See [inputs summary](#inputs) or main [module `variables.tf`](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/tree/master/variables.tf) file for more optional configuration.
126
-
127
-
To run this example you need have your [aws master-account profile configured in CLI](https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-profiles.html) and to execute:
128
-
```terraform
129
-
$ terraform init
130
-
$ terraform plan
131
-
$ terraform apply
132
-
```
133
-
134
68
## Required Permissions
135
69
136
70
### Provisioning Permissions
@@ -234,7 +168,7 @@ and a CodeBuild project being launched successfully
234
168
235
169
## Troubleshooting
236
170
237
-
## Q-General: Need to modify cloud-connector config (to troubleshoot with `debug` loglevel, modify ingestors for testing, ...)
171
+
###Q-General: Need to modify cloud-connector config (to troubleshoot with `debug` loglevel, modify ingestors for testing, ...)
238
172
A: both in ECS and AppRunner workload types, cloud-connector configuration is passed as a base64-encoded string through the env var `CONFIG`
239
173
<br/>S: Get current value, decode it, edit the desired (ex.:`logging: debug` value), encode it again, and spin it again with this new definition.
240
174
<br/>For information on all the modifyable configuration see [Cloud-Connector Chart](https://charts.sysdig.com/charts/cloud-connector/#configuration-detail) reference
@@ -248,7 +182,7 @@ with the correct values. Check [Sysdig SaaS per-region URLs if required](https:/
248
182
A: Make sure you installed both [cloud-bench](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/tree/master/modules/services/cloud-bench) and [cloud-connector](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/tree/master/modules/services/cloud-connector) modules
249
183
250
184
251
-
## Q-General-Networking: What's the requirements for the inbound/outbound connection?
185
+
###Q-General-Networking: What's the requirements for the inbound/outbound connection?
252
186
A: Refer to [Sysdig SASS Region and IP Ranges Documentation](https://docs.sysdig.com/en/docs/administration/saas-regions-and-ip-ranges/) to get Sysdig SaaS endpoint and allow both outbound (for compute vulnerability report) and inbound (for scheduled compliance checkups)
253
187
<br/>ECS type deployment will create following [security-group setup](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/blob/master/modules/services/cloud-connector-ecs/sec-group.tf)
0 commit comments