-
Notifications
You must be signed in to change notification settings - Fork 0
Description
This flow demonstrates what it looks like to a user from the perspective of an employee that is a member of a GitHub Organization + Team before an admin enables Okta SAML/SCIM.
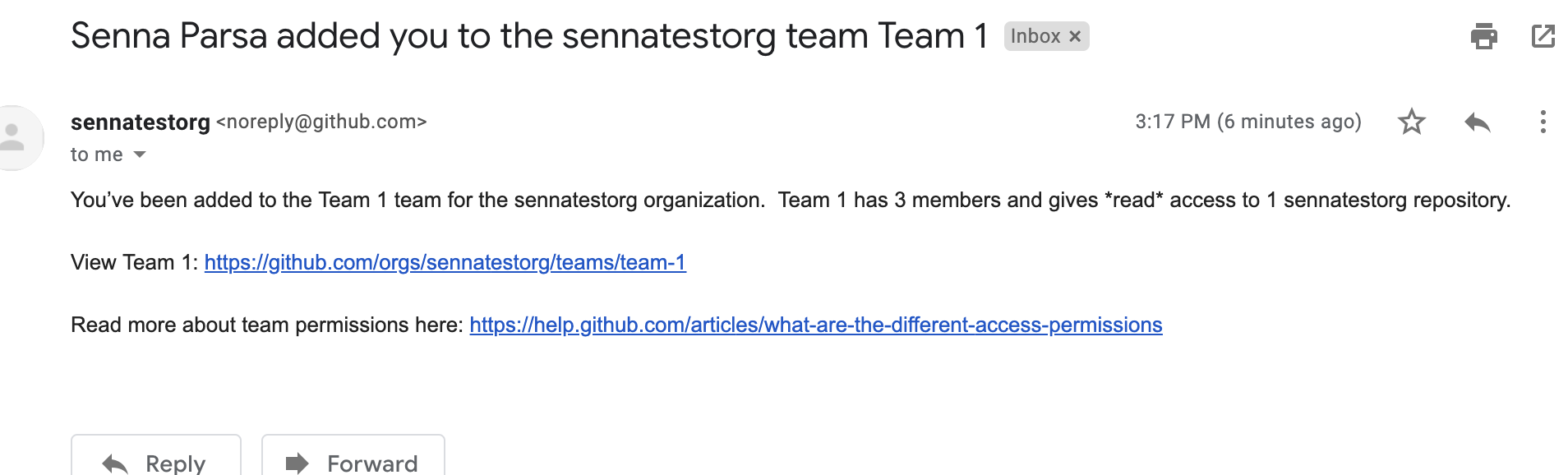
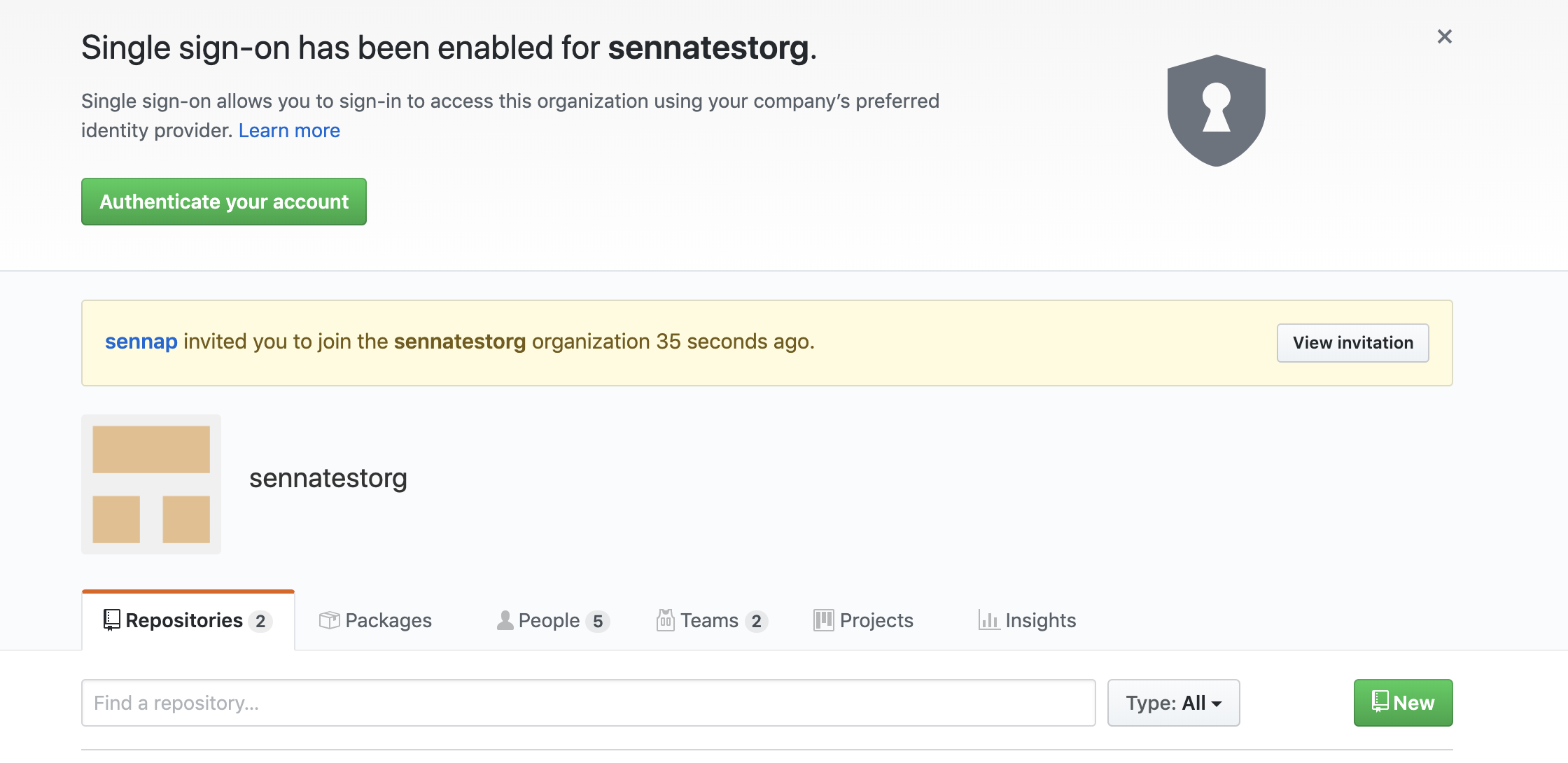
1. User joins a GitHub Organization
Organization admin sends invite to GitHub org/team using the GitHub UI
ORG invite:
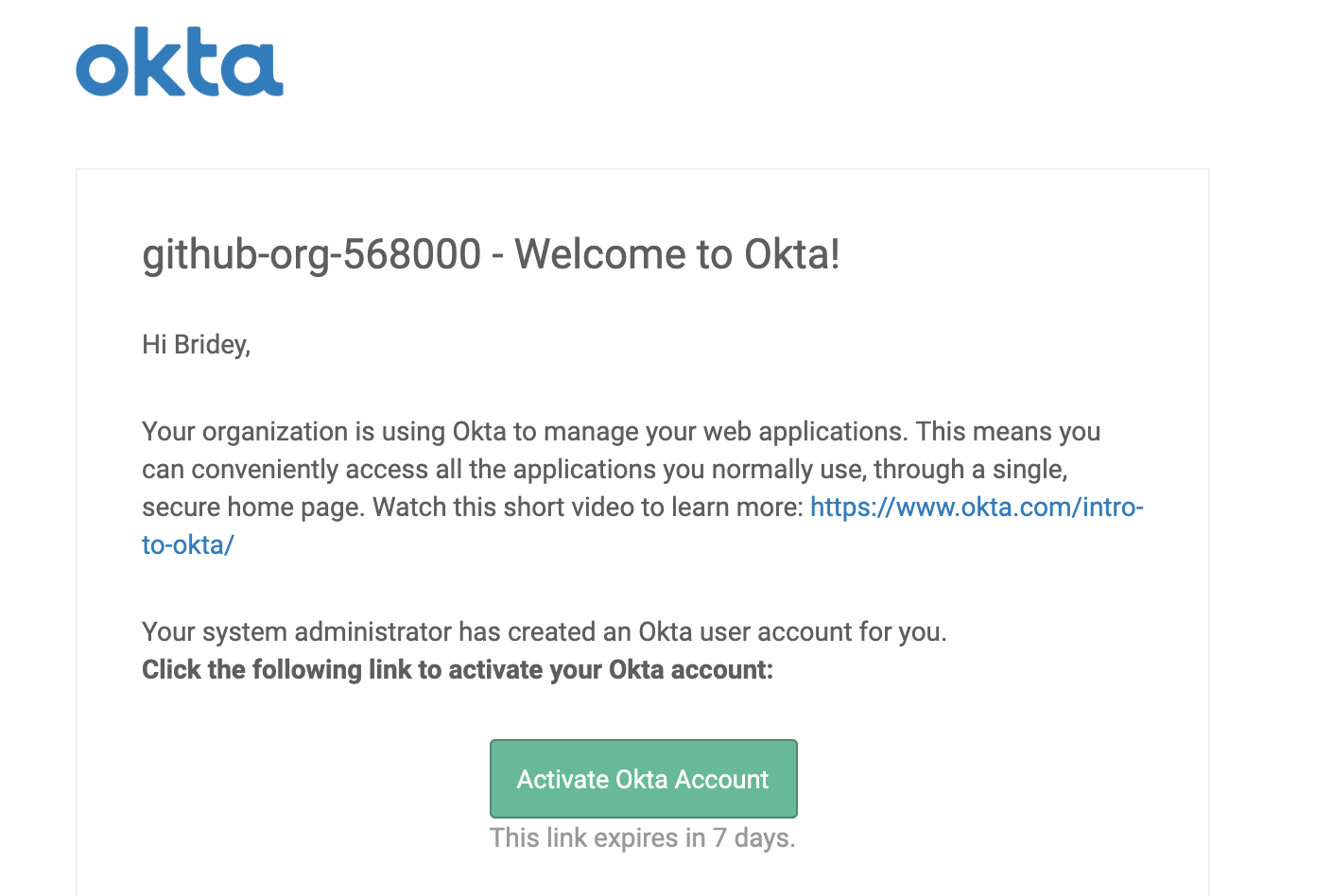
2. Adding users to iDP
Admin decides they want to enable SAML and SCIM in Okta. Admin logs in to Okta and assigns user (manually OR by uploading CSV)
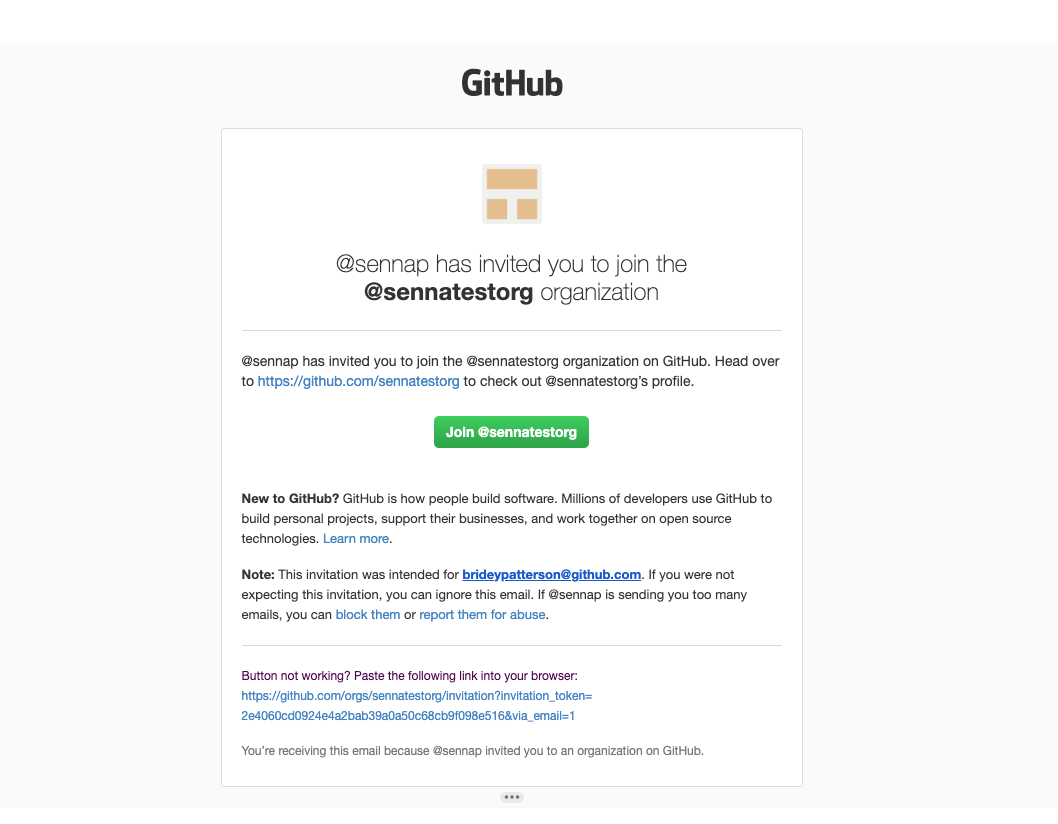
- Email will be sent from Okta inviting them to the Okta instance
3. Okta invite
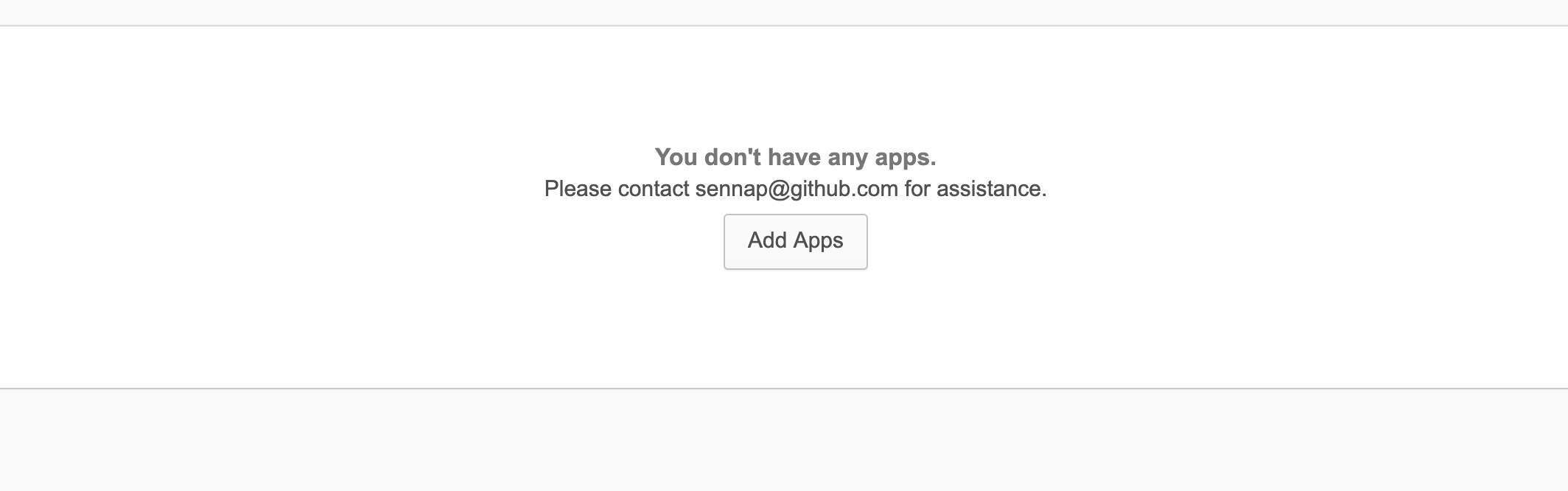
- If the Admin does not assign users to their GHEC app in Okta - the user at first will not see the GHEC app in Okta:
4. Assigning GHEC app in Okta
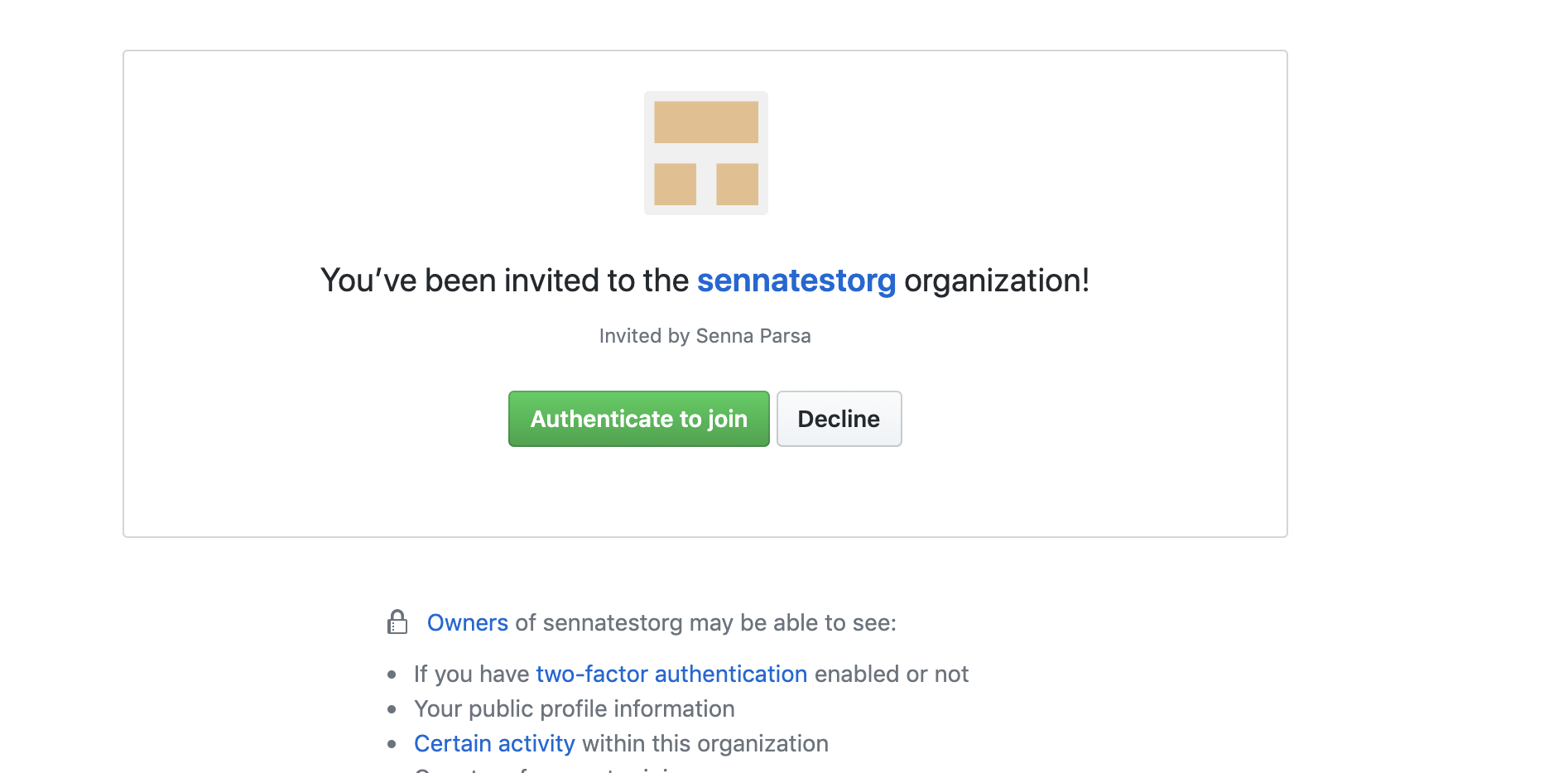
Once the Admin assigns a user to the GHEC app and enables SAML + SCIM (using these instructions - https://help.github.com/en/articles/enabling-and-testing-saml-single-sign-on-for-your-organization), the user will both:
A) Get an email inviting them to authenticate with SAML SSO
B) Get promoted by GitHub to authenticate via banner:
At this point the user will then be directed to the Okta login screen that they set a password for when logging in to Okta in step #3. If they successfully login, their external SAML identity (Okta) will be linked with their existing GitHub account 🎉
6. Enforcing SAML
Admin enforces SAML - (https://help.github.com/en/articles/enforcing-saml-single-sign-on-for-your-organization)
NOTE: If SAML is enforced but the user has not authenticated with SAML SSO, they will be removed from the organization, locked out, and receive email saying so.