Replies: 2 comments 1 reply
-
|
For this case, where the active prefix uses the whole address space, I think you don't need a container: in Netbox its only purpose is to reserve space for other prefixes to be allocated from and grouped together. If you want to allocate the whole prefix, you just flip it from container to active. I do see where you're coming from though. It's not wrong in principle to allow an entire container pool to be carved out by a single prefix which uses all the space. However it would add a lot of complexity to both the uniqueness checking and the GUI. Consider that if you have two prefixes 10.150.36.0/24 - which one should be shown first? Is one a "child" of the other? I suspect you would like to consider the container as "parent" and the active as "child", but since the two prefixes are identical, no such relationship is currently inferred. |
Beta Was this translation helpful? Give feedback.
-
|
Have you found a solution? I have the same issue with Azure vnet and subnet. Michael |
Beta Was this translation helpful? Give feedback.
Uh oh!
There was an error while loading. Please reload this page.
Uh oh!
There was an error while loading. Please reload this page.
-
We're automating our documentation of Azure/AWS used subnets in netbox.
So far it all went fine, when we worked in the Global vrf.
I'm moving some things to a 'vrf' in netbox, and I want to keep the checkbox 'Enforce Unique Space' on that VRF.
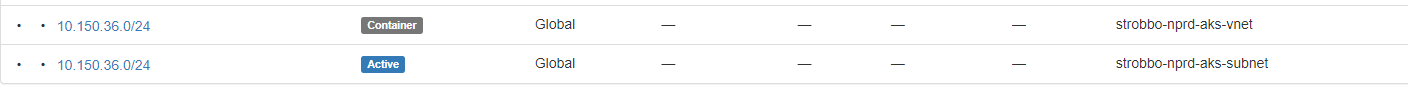
What I notice now, is that for some setups, the 'vnet' and the 'subnets' are the same.
So we make a container per VNETand then assign subnets to it using 'active' prefixes.
But in the above case, the subnet in the VNET takes the entire container, thus creating a 'duplicate' prefix in the vrf.
Would it be an option to create a second checkbox in the vrf that ignores containers for duplicate checks with 'active' prefixes ?
Maybe that containers are only check with containers, and active with active/reserved/deprecated ?
Pieter
Beta Was this translation helpful? Give feedback.
All reactions