|
| 1 | +# Browserpass - browser extension |
| 2 | + |
| 3 | +Browserpass is a browser extension for [zx2c4's pass](https://www.passwordstore.org/), a UNIX based password store manager. It allows you to auto-fill or copy to clipboard credentials for the current domain, protecting you from phishing attacks. |
| 4 | + |
| 5 | +In order to use Browserpass you must also install a [companion native messaging host](https://github.com/browserpass/browserpass-native), which provides an interface to your password store. |
| 6 | + |
| 7 | + |
| 8 | + |
| 9 | +## Table of Contents |
| 10 | + |
| 11 | +- [Requirements](#requirements) |
| 12 | +- [Installation](#installation) |
| 13 | + - [Verifying authenticity of the Github releases](#verifying-authenticity-of-the-github-releases) |
| 14 | +- [Updates](#updates) |
| 15 | +- [Usage](#usage) |
| 16 | + - [Organizing password store](#organizing-password-store) |
| 17 | + - [First steps in browser extension](#first-steps-in-browser-extension) |
| 18 | + - [Available keyboard shortcuts](#available-keyboard-shortcuts) |
| 19 | + - [Password matching and sorting](#password-matching-and-sorting) |
| 20 | + - [Basic HTTP authentication](#basic-http-authentication) |
| 21 | + - [Password store locations](password-store-locations) |
| 22 | +- [Options](#options) |
| 23 | +- [Security](#security) |
| 24 | +- [Privacy](#privacy) |
| 25 | +- [FAQ](#faq) |
| 26 | + - [Why OTP is not supported?](#why-otp-is-not-supported) |
| 27 | + - [How to use the same username and password pair on multiple domains](#how-to-use-the-same-username-and-password-pair-on-multiple-domains) |
| 28 | + - [Hints for macOS users](#hints-for-macos-users) |
| 29 | + - [Hints for NixOS / Nix users](#hints-for-nixos--nix-users) |
| 30 | +- [Contributing](#contributing) |
| 31 | + |
| 32 | +## Requirements |
| 33 | + |
| 34 | +- The latest stable version of Chromium or Firefox, or any of their derivatives. |
| 35 | +- The latest stable version of gpg (having `pass` or `gopass` is actually not required). |
| 36 | +- A password store that follows certain [naming conventions](#organizing-password-store) |
| 37 | + |
| 38 | +## Installation |
| 39 | + |
| 40 | +In order to install Browserpass correctly, you have to install two of its components: |
| 41 | + |
| 42 | +- [Native messaging host](https://github.com/browserpass/browserpass-native#installation) |
| 43 | +- Browser extension for Chromium-based browsers (choose one of the options): |
| 44 | + - Install the extension from [Chrome Web Store](https://chrome.google.com/webstore/detail/browserpass-ce/naepdomgkenhinolocfifgehidddafch) (which will provide auto-updates) |
| 45 | + - Download `browserpass.crx` from the latest release and drag'n'drop it into `chrome://extensions` (remember to watch for new releases!). |
| 46 | + - Download `chromium.zip`, unarchive and use `Load unpacked extension` in `chrome://extensions` in Developer mode. |
| 47 | +- Browser extension for Firefox-based browsers (choose one of the options): |
| 48 | + - Install the extension from [Firefox Add-ons](https://addons.mozilla.org/en-US/firefox/addon/browserpass-ce/) (which will provide auto-updates) |
| 49 | + - Download `firefox.zip` from the latest release, unarchive and use `Load Temporary Add-on` on `about:debugging#addons` (remember the extension will be removed after browser is closed!). |
| 50 | + |
| 51 | +### Verifying authenticity of the Github releases |
| 52 | + |
| 53 | +All Github release files are signed with [this PGP key](https://keybase.io/maximbaz). To verify the signature of a given file, use `$ gpg --verify <file>.sig`. |
| 54 | + |
| 55 | +It should report: |
| 56 | + |
| 57 | +``` |
| 58 | +gpg: Signature made ... |
| 59 | +gpg: using RSA key 8053EB88879A68CB4873D32B011FDC52DA839335 |
| 60 | +gpg: Good signature from "Maxim Baz <...>" |
| 61 | +gpg: aka ... |
| 62 | +Primary key fingerprint: EB4F 9E5A 60D3 2232 BB52 150C 12C8 7A28 FEAC 6B20 |
| 63 | + Subkey fingerprint: 8053 EB88 879A 68CB 4873 D32B 011F DC52 DA83 9335 |
| 64 | +``` |
| 65 | + |
| 66 | +## Updates |
| 67 | + |
| 68 | +If you installed the extension from a webstore, you will receive updates automatically. |
| 69 | + |
| 70 | +If not, repeat the installation instructions for the extension. |
| 71 | + |
| 72 | +**IMPORTANT:** Majority of the improvements require changing code in both browser extensions and the [host application](https://github.com/browserpass/browserpass-native#updates). It is expected that you will make sure to keep both components up to date. |
| 73 | + |
| 74 | +## Usage |
| 75 | + |
| 76 | +### Organizing password store |
| 77 | + |
| 78 | +Browserpass was designed with an assumption that certain conventions are being followed when organizing your password store. |
| 79 | + |
| 80 | +1. In order to benefit of phishing attack protection, a password entry file, or any of its parent folders, must contain a full domain name (including TLD like `.com`) in their name. |
| 81 | + |
| 82 | + Some good examples: |
| 83 | + |
| 84 | + ``` |
| 85 | + ~/.password-store/ |
| 86 | + accounts.google.com.gpg |
| 87 | + amazon.com.gpg |
| 88 | + github.com/ |
| 89 | + personal.gpg |
| 90 | + work.gpg |
| 91 | + ``` |
| 92 | +
|
| 93 | +1. Password must be defined on a line starting from `password:`, `pass:` or `secret:` (case-insensitive), and if all of these are absent, the first line in the password entry file is considered to be a password. |
| 94 | +
|
| 95 | +1. Username must be defined on a line starting from `login:`, `username:`, `user:` or `email:` (case-insensitive), and if all of these are absent, the file name is considered to be a username. |
| 96 | +
|
| 97 | +1. URL ([only](#password-matching-and-sorting) used for [basic HTTP auth](#basic-http-authentication)!) must be defined on a line starting from `url:`, `uri:`, `website:`, `site:`, `link:` or `launch:` (case-insensitive). |
| 98 | +
|
| 99 | +### First steps in browser extension |
| 100 | +
|
| 101 | +Click on the icon or use <kbd>Ctrl+Shift+L</kbd> to open Browserpass with the entries that match current domain. |
| 102 | +
|
| 103 | +How to change the shortcut: |
| 104 | +
|
| 105 | +- Chromium: `chrome://extensions/shortcuts` |
| 106 | +- Firefox: `about:addons` > Gear icon > `Manage Extension Shortcuts` |
| 107 | +
|
| 108 | +When Browserpass shows entries for a specific domain, you will see a badge with the domain name in the search input field: |
| 109 | +
|
| 110 | +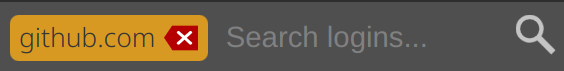 |
| 111 | +
|
| 112 | +If you want to intentionally disable phishing attacks protection and search credentials in the entire password store, you must press <kbd>Backspace</kbd> to confirm this decision (domain badge will disappear), then use Browserpass normally. |
| 113 | +
|
| 114 | +### Available keyboard shortcuts |
| 115 | +
|
| 116 | +Note: If the cursor is located in the search input field, every shortcut that works on the selected entry will be applied on the first entry in the popup list. |
| 117 | +
|
| 118 | +| Shortcult | Action | |
| 119 | +| ---------------------------------------------------- | --------------------------------------------- | |
| 120 | +| <kbd>Ctrl+Shift+L</kbd> | Open Browserpass popup | |
| 121 | +| <kbd>Enter</kbd> | Submit form with these credentials () | |
| 122 | +| Arrow keys and <kbd>Tab</kbd> / <kbd>Shift+Tab</kbd> | Navigate popup list | |
| 123 | +| <kbd>Ctrl+C</kbd> | Copy password to clipboard | |
| 124 | +| <kbd>Ctrl+Shift+C</kbd> | Copy username to clipboard | |
| 125 | +| <kbd>Ctrl+G</kbd> | Open URL in the current tab | |
| 126 | +| <kbd>Ctrl+Shift+G</kbd> | Open URL in the new tab | |
| 127 | +| <kbd>Backspace</kbd> | Search passwords in the entire password store | |
| 128 | +
|
| 129 | +### Password matching and sorting |
| 130 | +
|
| 131 | +When you first open Browserpass popup, you will see a badge with the current domain name in the search input field: |
| 132 | +
|
| 133 | + |
| 134 | +
|
| 135 | +This means that phishing attack prevention is enabled, and Browserpass is only showing you entries from your password store that match this domain. |
| 136 | +
|
| 137 | +In order for Browserpass to correctly determine matching entries, it is expected that your password store follows naming conventions (see [Organizing password store](#organizing-password-store)), in particular your file or folder name must contain TLD, i.e. not `github.gpg`, but `github.com.gpg`. If an attacker directed you to `https://github.co/login` (notice `.co`), Browserpass will **not** present `github.com` entry in the popup. However if you intentionally want to re-use the same credentials on multiple domains (e.g. `amazon.com` and `amazon.co.uk`), see [How to use the same username and password pair on multiple domains](#how-to-use-the-same-username-and-password-pair-on-multiple-domains). |
| 138 | +
|
| 139 | +Browserpass will display entries for the current domain, as well as all parent entries, but not entries from different subdomains. Suppose you are currently on `https://v3.app.example.com`, Browserpass will present all the following entries in popup (if they exist): `v3.app.example.com`, `app.example.com`, `example.com`; but it will not present entries like `v2.app.example.com` or `wiki.example.com`. |
| 140 | +
|
| 141 | +Finally Browserpass will also present entries that you have recently used on this domain, even if they don't belong to this domain. Suppose you have a password for `amazon.com`, but you open `https://amazon.co.uk`, at first Browserpass will present no entries (because nothing matches `amazon.co.uk`), but if you hit <kbd>Backspace</kbd>, find `amazon.com` and use it to login, next time you visit `https://amazon.co.uk` and open Browserpass, `amazon.com` entry will already be present. |
| 142 | +
|
| 143 | +The sorting algorithm implemented in Browserpass will use several intuitions to try to order results in the most expected way for a user: |
| 144 | +
|
| 145 | +1. If Browserpass was previously used on this domain, the first entry in the list will always be the most recently used one. |
| 146 | +1. The rest of the available password entries will be sorted by the frequency of their usage, the more times a password was used, the higher it will be in the list. |
| 147 | +1. Password entries with the identical usage counts are sorted by number of domain levels (specificity), i.e. `wiki.example.com` will be above `example.com`. |
| 148 | +1. If all the above is equal, password entries are sorted alphabetically. |
| 149 | +
|
| 150 | +### Basic HTTP authentication |
| 151 | +
|
| 152 | +Due to the way browsers are implemented, browser extensions are only able to fill basic HTTP auth credentials for a website if these websites were opened by the extension. For this reason alone Browserpass contains a functionality to open a URL associated with a password entry in the current or a new browser tab. |
| 153 | +
|
| 154 | +If you want Browserpass to fill out basic HTTP auth credentials, you must open these websites using Browserpass. |
| 155 | +
|
| 156 | +### Password store locations |
| 157 | +
|
| 158 | +Browserpass is able to automatically detect your password store location: it first checks `PASSWORD_STORE_DIR` environment variable, if it is not defined it falls back to `$HOME/.password-store`. |
| 159 | +
|
| 160 | +Using `Custom store locations` setting in the browser extension options you are able to define one or multiple locations for password stores: there are no restrictions, it can be subfolders in the password store, gopass mounts or any other folder that contains password entries. |
| 161 | +
|
| 162 | +## Options |
| 163 | +
|
| 164 | +The list of available options: |
| 165 | +
|
| 166 | +| Name | Description | |
| 167 | +| ----------------------------------------------------------- | ------------------------------------------------------------ | |
| 168 | +| Automatically submit forms after filling (aka `autoSubmit`) | Make Browserpass automatically submit the login form for you | |
| 169 | +| Custom gpg binary (aka `gpgPath`) | Path to a custom `gpg` binary to use | |
| 170 | +| Custom store locations | List of password stores to use | |
| 171 | +
|
| 172 | +Browserpass allows configuring certain settings in different places places using the following priority, highest first: |
| 173 | +
|
| 174 | +1. Options defined in specific `*.gpg` files, only apply to these password entries: |
| 175 | + - `autoSubmit` |
| 176 | +1. Options defined in browser extension options: |
| 177 | + - Automatically submit forms after filling (aka `autoSubmit`) |
| 178 | + - Custom gpg binary (aka `gpgPath`) |
| 179 | + - Custom store locations |
| 180 | +1. Options defined in `.browserpass.json` file located in the root of a password store: |
| 181 | + - `autoSubmit` |
| 182 | + - `gpgPath` |
| 183 | +
|
| 184 | +## Security |
| 185 | +
|
| 186 | +Browserpass aims to protect your passwords and computer from malicious or fraudulent websites. |
| 187 | +
|
| 188 | +- To protect against phishing, only passwords matching the origin hostname are suggested or selected without an explicit search term. |
| 189 | +- To minimize attack surface, the website is not allowed to trigger any extension action without user invocation. |
| 190 | +- Only data from the selected password is made available to the website. |
| 191 | +- Given full control of the non-native component of the extension, the attacker can extract passwords stored in the configured repository, but can not obtain files elsewhere on the filesystem or reach code execution. |
| 192 | +- Browserpass does not attempt to secure the data it stores in browser local storage, it is assumed that users take precautions to protect their local file system (e.g. by using disk encryption) |
| 193 | +
|
| 194 | +## Privacy |
| 195 | +
|
| 196 | +Browserpass does not send any telemetry data, all metadata it collects to perform its functionality is stored in local storage and never leaves your browser. |
| 197 | +
|
| 198 | +## FAQ |
| 199 | +
|
| 200 | +### How to use the same username and password pair on multiple domains |
| 201 | +
|
| 202 | +There are several ways to tell Browserpass to use the same pair of credentials on multiple domains, for example how to re-use an existing password entry `amazon.com.gpg` on a `https://amazon.co.uk` website without duplicating your credentials in multiple password files. |
| 203 | +
|
| 204 | +The first option is just to manually find the desired credentials and use them in Browserpass, in other words if you have credentials for `amazon.com`, but you are currently on `https://amazon.co.uk`, open Browserpass, hit <kbd>Backspace</kbd> to search the entire password store, find `amazon.com` and hit <kbd>Enter</kbd> to login. Next time you will open Browserpass on `https://amazon.co.uk`, the popup will already contain the `amazon.com` entry, because it was previously used on this website (for details see [Password matching and sorting](#password-matching-and-sorting) section). |
| 205 | +
|
| 206 | +The second option is to create a symlink file `amazon.co.uk.gpg` pointing to `amazon.com.gpg` in your password store, not only Browserpass, but `pass` itself will both recognize the symlink as an existing password entry. |
| 207 | +
|
| 208 | +If you simply want to re-use the same credentials on multiple subdomains of the same domain (e.g. `app.example.com` and `wiki.example.com`), you can also rename your password entry to a common denominator of the two subdomains, which in this example would be `example.com.gpg` (see [Password matching and sorting](#password-matching-and-sorting)). |
| 209 | +
|
| 210 | +### Why OTP is not supported? |
| 211 | +
|
| 212 | +Tools like `pass-otp` make it possible to use `pass` for generating OTP codes, however keeping both passwords and OTP URI in the same location diminishes the major benefit that OTP is supposed to provide: two factor authentication. The purpose of multi-factor authentication is to protect your account even when attackers gain access to your password store, but if your OTP is stored in the same place, all auth factors will be compromised at once. In particular, Browserpass has access to the entire contents of your password entries, so if it is ever compromised, all your accounts will be at risk, even though you signed up for 2FA. |
| 213 | +
|
| 214 | +Browserpass is opinionated, it does not promote `pass-otp` and intentionally does not support generating OTP codes from OTP URIs in password entiries, even though there are other password managers that provide such functionality. |
| 215 | +
|
| 216 | +There are valid scenarios for using `pass-otp` (e.g. it gives protection against intercepting your password during transmission), but users are strongly advised to very carefully consider if `pass-otp` fits their needs and come up with their own ways of accessing OTP codes that conforms to their security requirements (for example by using dmenu/rofi scripts). For the majority of people `pass-otp` is not recommended, using any phone app like Authy will be a much better and more secure alternative, because this way attackers would have to not only break into your password store, but they would _also_ have to break into your phone. |
| 217 | +
|
| 218 | +## Building the extension |
| 219 | +
|
| 220 | +### Build locally |
| 221 | +
|
| 222 | +Make sure you have the latest stable Yarn installed. |
| 223 | +
|
| 224 | +The following `make` goals are available (check Makefile for more details): |
| 225 | +
|
| 226 | +| Command | Description | |
| 227 | +| -------------------- | --------------------------------------------------------------------------------------- | |
| 228 | +| `make` or `make all` | Compile the extension source code, prepare unpacked extensions for Chromium and Firefox | |
| 229 | +| `make extension` | Compile the extension source code | |
| 230 | +| `make chromium` | Compile the extension source code, prepare unpacked extension for Chromium | |
| 231 | +| `make firefox` | Compile the extension source code, prepare unpacked extension for Firefox | |
| 232 | +| `make crx` | Compile the extension source code, prepare packed extension for Chromium | |
| 233 | +
|
| 234 | +### Load an unpacked extension |
| 235 | +
|
| 236 | +- For Chromium: |
| 237 | + - Go to `chrome://extensions` |
| 238 | + - Enable `Developer mode` |
| 239 | + - Click `Load unpacked extension` |
| 240 | + - Select `browserpass-extension/chromium` directory |
| 241 | +- For Firefox: |
| 242 | + - Go to `about:debugging#addons` |
| 243 | + - Click `Load temporary add-on` |
| 244 | + - Select `browserpass-extension/firefox` directory |
| 245 | +
|
| 246 | +## Contributing |
| 247 | +
|
| 248 | +1. Fork [the repo](https://github.com/browserpass/browserpass-extension) |
| 249 | +2. Create your feature branch |
| 250 | + - `git checkout -b my-new-feature` |
| 251 | +3. Commit your changes |
| 252 | + - `git commit -am 'Add some feature'` |
| 253 | +4. Push the branch |
| 254 | + - `git push origin my-new-feature` |
| 255 | +5. Create a new pull request |
0 commit comments