You can filter on the following indicator attributes: + * `actors` + * `confidence` + * `id` + * `indicator` + * `killChain` + * `source` + * `threatType` + * `type` + * `validFrom` + * `validUntil` +* `
}) * **Collection**. [Collection](/docs/send-data/collection/), [OpenTelemetry Collection](/docs/send-data/opentelemetry-collector/), [Source Template](/docs/send-data), [Status](/docs/manage/ingestion-volume/collection-status-page/), [Ingest Budget](/docs/manage/ingestion-volume/ingest-budgets/), [Health Events](/docs/manage/health-events/), [Archive](/docs/manage/data-archiving/archive), [Data Archiving](/docs/manage/data-archiving/).
-* **Logs**. [Fields](/docs/manage/fields/), [Field Extraction Rules](/docs/manage/field-extractions/), [Partitions](/docs/manage/partitions/), [Scheduled Views](/docs/manage/scheduled-views/), [Data Forwarding](/docs/manage/data-forwarding/), [Threat Intelligence](/docs/platform-services/threat-intelligence-indicators/).
+* **Logs**. [Fields](/docs/manage/fields/), [Field Extraction Rules](/docs/manage/field-extractions/), [Partitions](/docs/manage/partitions/), [Scheduled Views](/docs/manage/scheduled-views/), [Data Forwarding](/docs/manage/data-forwarding/), [Threat Intelligence](/docs/security/threat-intelligence/).
* **Metrics**. [Metrics Rules](/docs/metrics/metric-rules-editor/), [Logs-to-Metrics](/docs/metrics/logs-to-metrics/), [Metrics Transformation Rules](/docs/metrics/metrics-transformation-rules/).
* **Monitoring**. [Connections](/docs/alerts/webhook-connections).
diff --git a/docs/integrations/amazon-aws/api-gateway.md b/docs/integrations/amazon-aws/api-gateway.md
index 65ffba46e5..cf7ea3b448 100644
--- a/docs/integrations/amazon-aws/api-gateway.md
+++ b/docs/integrations/amazon-aws/api-gateway.md
@@ -640,7 +640,7 @@ Use these dashboards to:
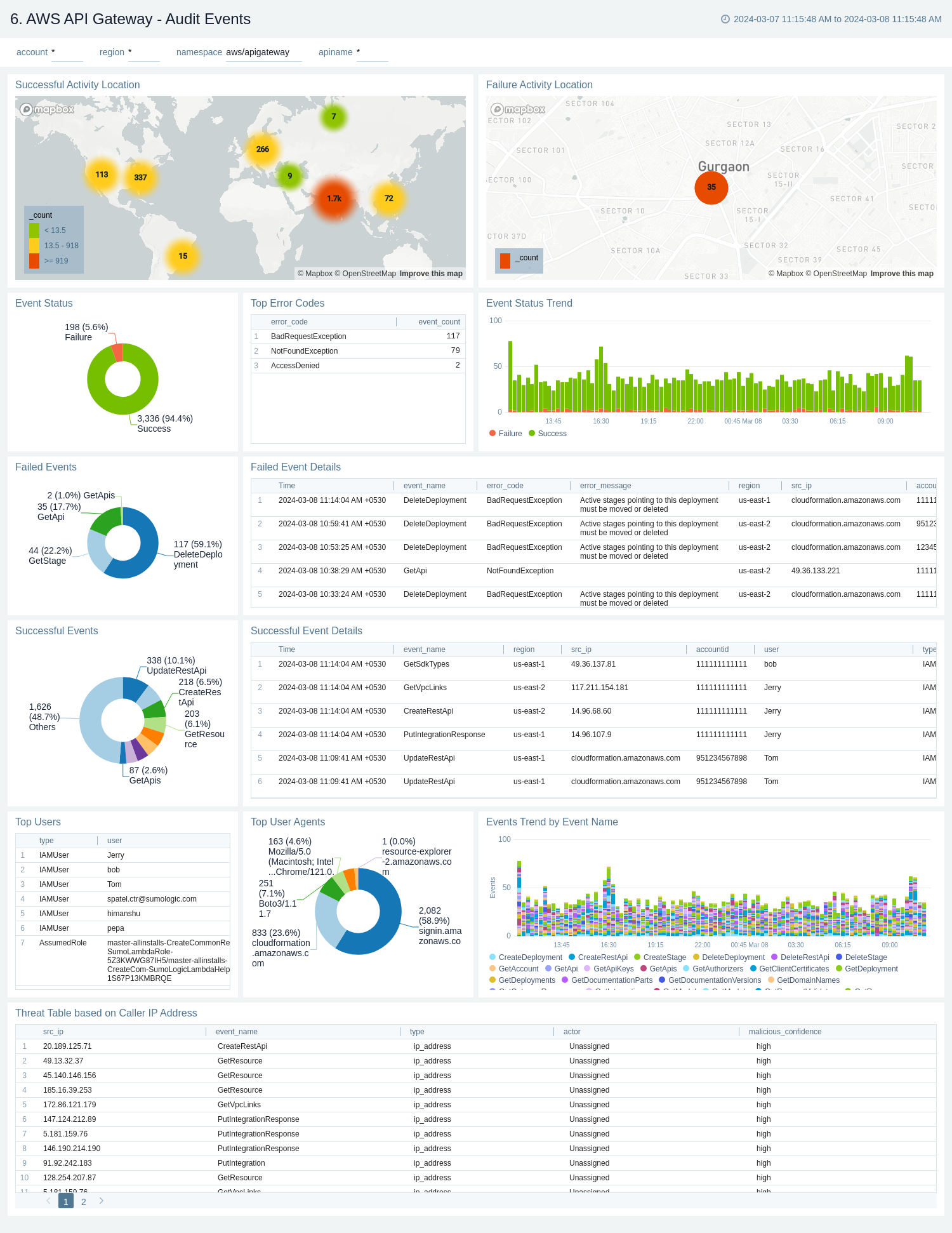
* Monitor all API Gateway-related audit logs available via CloudTrail events
* Monitor incoming user activity locations for both successful and failed events to ensure the activity matches with expectations
* Monitor successful and failed API Gateway events, users and user agents / fail activities, and failure reasons
-* Monitor requests coming in from known malicious IP addresses detected via [Sumo Logic Threat Intel](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq)
+* Monitor requests coming in from known malicious IP addresses detected via Sumo Logic [threat intelligence](/docs/security/threat-intelligence/)
* **Collection**. [Collection](/docs/send-data/collection/), [OpenTelemetry Collection](/docs/send-data/opentelemetry-collector/), [Source Template](/docs/send-data), [Status](/docs/manage/ingestion-volume/collection-status-page/), [Ingest Budget](/docs/manage/ingestion-volume/ingest-budgets/), [Health Events](/docs/manage/health-events/), [Archive](/docs/manage/data-archiving/archive), [Data Archiving](/docs/manage/data-archiving/).
-* **Logs**. [Fields](/docs/manage/fields/), [Field Extraction Rules](/docs/manage/field-extractions/), [Partitions](/docs/manage/partitions/), [Scheduled Views](/docs/manage/scheduled-views/), [Data Forwarding](/docs/manage/data-forwarding/), [Threat Intelligence](/docs/platform-services/threat-intelligence-indicators/).
+* **Logs**. [Fields](/docs/manage/fields/), [Field Extraction Rules](/docs/manage/field-extractions/), [Partitions](/docs/manage/partitions/), [Scheduled Views](/docs/manage/scheduled-views/), [Data Forwarding](/docs/manage/data-forwarding/), [Threat Intelligence](/docs/security/threat-intelligence/).
* **Metrics**. [Metrics Rules](/docs/metrics/metric-rules-editor/), [Logs-to-Metrics](/docs/metrics/logs-to-metrics/), [Metrics Transformation Rules](/docs/metrics/metrics-transformation-rules/).
* **Monitoring**. [Connections](/docs/alerts/webhook-connections).
diff --git a/docs/integrations/amazon-aws/api-gateway.md b/docs/integrations/amazon-aws/api-gateway.md
index 65ffba46e5..cf7ea3b448 100644
--- a/docs/integrations/amazon-aws/api-gateway.md
+++ b/docs/integrations/amazon-aws/api-gateway.md
@@ -640,7 +640,7 @@ Use these dashboards to:
* Monitor all API Gateway-related audit logs available via CloudTrail events
* Monitor incoming user activity locations for both successful and failed events to ensure the activity matches with expectations
* Monitor successful and failed API Gateway events, users and user agents / fail activities, and failure reasons
-* Monitor requests coming in from known malicious IP addresses detected via [Sumo Logic Threat Intel](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq)
+* Monitor requests coming in from known malicious IP addresses detected via Sumo Logic [threat intelligence](/docs/security/threat-intelligence/)
 diff --git a/docs/integrations/amazon-aws/application-load-balancer.md b/docs/integrations/amazon-aws/application-load-balancer.md
index 7289111c03..0fbdce0640 100644
--- a/docs/integrations/amazon-aws/application-load-balancer.md
+++ b/docs/integrations/amazon-aws/application-load-balancer.md
@@ -234,7 +234,7 @@ Use this dashboard to:
### Threat Intel
-The **AWS Application Load Balancer - Threat Intel** dashboard provides insights into incoming requests from malicious sources determined through [Sumo Logic’s Threat Intel feature](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq). Panels show detailed information on malicious IPs and the malicious confidence of each threat.
+The **AWS Application Load Balancer - Threat Intel** dashboard provides insights into incoming requests from malicious sources determined through Sumo Logic [threat intelligence](/docs/security/threat-intelligence/). Panels show detailed information on malicious IPs and the malicious confidence of each threat.
Use this dashboard to:
* Identify known malicious IPs that access your load-balancers and use firewall access control lists to prevent them from sending you traffic going forward.
diff --git a/docs/integrations/amazon-aws/classic-load-balancer.md b/docs/integrations/amazon-aws/classic-load-balancer.md
index 20c706bd9e..09f5d83098 100644
--- a/docs/integrations/amazon-aws/classic-load-balancer.md
+++ b/docs/integrations/amazon-aws/classic-load-balancer.md
@@ -237,7 +237,7 @@ Use this dashboard to:
### Threat Intel
-The **AWS Classic Load Balancer - Threat Intel** dashboard provides insights into incoming requests from malicious sources determined via [Sumo Logic’s Threat Intel feature](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq). Dashboard panels show detailed information on malicious IPs and the malicious confidence of each threat.
+The **AWS Classic Load Balancer - Threat Intel** dashboard provides insights into incoming requests from malicious sources determined via Sumo Logic [threat intelligence](/docs/security/threat-intelligence/). Dashboard panels show detailed information on malicious IPs and the malicious confidence of each threat.
Use this dashboard to:
* Identify known malicious IPs that are accessing your load-balancers and use firewall access control lists to prevent them from sending you traffic going forward.
diff --git a/docs/integrations/amazon-aws/lambda.md b/docs/integrations/amazon-aws/lambda.md
index 9607dc1931..34bd4c0d95 100644
--- a/docs/integrations/amazon-aws/lambda.md
+++ b/docs/integrations/amazon-aws/lambda.md
@@ -383,7 +383,7 @@ Use this dashboard to:
### Threat Intel
-**AWS Lambda - Threat Intel** dashboard provides insights into incoming requests to your AWS Lambda functions from malicious sources determined via [Sumo Logic’s Threat Intel feature](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq). Panels show detailed information on malicious IPs and the malicious confidence of each threat.
+**AWS Lambda - Threat Intel** dashboard provides insights into incoming requests to your AWS Lambda functions from malicious sources determined via Sumo Logic [threat intelligence](/docs/security/threat-intelligence/). Panels show detailed information on malicious IPs and the malicious confidence of each threat.
Use this dashboard to:
* Identify known malicious IPs that are access your load-balancers and use firewall access control lists to prevent them from sending you traffic going forward
diff --git a/docs/integrations/amazon-aws/network-firewall.md b/docs/integrations/amazon-aws/network-firewall.md
index d976e83cf8..7d0317245e 100644
--- a/docs/integrations/amazon-aws/network-firewall.md
+++ b/docs/integrations/amazon-aws/network-firewall.md
@@ -150,10 +150,10 @@ Use this dashboard to:
### IDS Overview
-The **AWS Network Firewall - IDS Overview** provides visibility into alerts generated by the firewall rules. This includes geolocation information on top destinations, alerts over time, correlation with CrowdStrike threat intelligence data, and top systems blocked.
+The **AWS Network Firewall - IDS Overview** provides visibility into alerts generated by the firewall rules. This includes geolocation information on top destinations, alerts over time, correlation with Sumo Logic [threat intelligence](/docs/security/threat-intelligence/) data, and top systems blocked.
Use this dashboard to:
* Gain visibility into alerts generated by the AWS Network Firewall including location information from top destinations.
-* Gain visibility into traffic from malicious IPs determined by correlating AWS Network Firewall data with Crowdstrike Threat Intelligence data.
+* Gain visibility into traffic from malicious IPs determined by correlating AWS Network Firewall data with Sumo Logic [threat intelligence](/docs/security/threat-intelligence/) data.
diff --git a/docs/integrations/amazon-aws/application-load-balancer.md b/docs/integrations/amazon-aws/application-load-balancer.md
index 7289111c03..0fbdce0640 100644
--- a/docs/integrations/amazon-aws/application-load-balancer.md
+++ b/docs/integrations/amazon-aws/application-load-balancer.md
@@ -234,7 +234,7 @@ Use this dashboard to:
### Threat Intel
-The **AWS Application Load Balancer - Threat Intel** dashboard provides insights into incoming requests from malicious sources determined through [Sumo Logic’s Threat Intel feature](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq). Panels show detailed information on malicious IPs and the malicious confidence of each threat.
+The **AWS Application Load Balancer - Threat Intel** dashboard provides insights into incoming requests from malicious sources determined through Sumo Logic [threat intelligence](/docs/security/threat-intelligence/). Panels show detailed information on malicious IPs and the malicious confidence of each threat.
Use this dashboard to:
* Identify known malicious IPs that access your load-balancers and use firewall access control lists to prevent them from sending you traffic going forward.
diff --git a/docs/integrations/amazon-aws/classic-load-balancer.md b/docs/integrations/amazon-aws/classic-load-balancer.md
index 20c706bd9e..09f5d83098 100644
--- a/docs/integrations/amazon-aws/classic-load-balancer.md
+++ b/docs/integrations/amazon-aws/classic-load-balancer.md
@@ -237,7 +237,7 @@ Use this dashboard to:
### Threat Intel
-The **AWS Classic Load Balancer - Threat Intel** dashboard provides insights into incoming requests from malicious sources determined via [Sumo Logic’s Threat Intel feature](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq). Dashboard panels show detailed information on malicious IPs and the malicious confidence of each threat.
+The **AWS Classic Load Balancer - Threat Intel** dashboard provides insights into incoming requests from malicious sources determined via Sumo Logic [threat intelligence](/docs/security/threat-intelligence/). Dashboard panels show detailed information on malicious IPs and the malicious confidence of each threat.
Use this dashboard to:
* Identify known malicious IPs that are accessing your load-balancers and use firewall access control lists to prevent them from sending you traffic going forward.
diff --git a/docs/integrations/amazon-aws/lambda.md b/docs/integrations/amazon-aws/lambda.md
index 9607dc1931..34bd4c0d95 100644
--- a/docs/integrations/amazon-aws/lambda.md
+++ b/docs/integrations/amazon-aws/lambda.md
@@ -383,7 +383,7 @@ Use this dashboard to:
### Threat Intel
-**AWS Lambda - Threat Intel** dashboard provides insights into incoming requests to your AWS Lambda functions from malicious sources determined via [Sumo Logic’s Threat Intel feature](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq). Panels show detailed information on malicious IPs and the malicious confidence of each threat.
+**AWS Lambda - Threat Intel** dashboard provides insights into incoming requests to your AWS Lambda functions from malicious sources determined via Sumo Logic [threat intelligence](/docs/security/threat-intelligence/). Panels show detailed information on malicious IPs and the malicious confidence of each threat.
Use this dashboard to:
* Identify known malicious IPs that are access your load-balancers and use firewall access control lists to prevent them from sending you traffic going forward
diff --git a/docs/integrations/amazon-aws/network-firewall.md b/docs/integrations/amazon-aws/network-firewall.md
index d976e83cf8..7d0317245e 100644
--- a/docs/integrations/amazon-aws/network-firewall.md
+++ b/docs/integrations/amazon-aws/network-firewall.md
@@ -150,10 +150,10 @@ Use this dashboard to:
### IDS Overview
-The **AWS Network Firewall - IDS Overview** provides visibility into alerts generated by the firewall rules. This includes geolocation information on top destinations, alerts over time, correlation with CrowdStrike threat intelligence data, and top systems blocked.
+The **AWS Network Firewall - IDS Overview** provides visibility into alerts generated by the firewall rules. This includes geolocation information on top destinations, alerts over time, correlation with Sumo Logic [threat intelligence](/docs/security/threat-intelligence/) data, and top systems blocked.
Use this dashboard to:
* Gain visibility into alerts generated by the AWS Network Firewall including location information from top destinations.
-* Gain visibility into traffic from malicious IPs determined by correlating AWS Network Firewall data with Crowdstrike Threat Intelligence data.
+* Gain visibility into traffic from malicious IPs determined by correlating AWS Network Firewall data with Sumo Logic [threat intelligence](/docs/security/threat-intelligence/) data.
}) diff --git a/docs/integrations/amazon-aws/route-53-resolver-security.md b/docs/integrations/amazon-aws/route-53-resolver-security.md
index 72e85cf277..f14eb6f738 100644
--- a/docs/integrations/amazon-aws/route-53-resolver-security.md
+++ b/docs/integrations/amazon-aws/route-53-resolver-security.md
@@ -61,7 +61,7 @@ import ViewDashboards from '../../reuse/apps/view-dashboards.md';
### Query Logging Overview
-The Query Logging Overview Dashboard provides insights into DNS activities such as DNS queries by location, VPC and instance ID. Additional security information is provided, including blocked and alerted DNS queries from the Route 53 DNS Resolver Firewall, and Threat Intel matches from Sumo Logic's CrowdStrike integration.
+The Query Logging Overview Dashboard provides insights into DNS activities such as DNS queries by location, VPC and instance ID. Additional security information is provided, including blocked and alerted DNS queries from the Route 53 DNS Resolver Firewall, and threat intel matches from Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
diff --git a/docs/integrations/amazon-aws/route-53-resolver-security.md b/docs/integrations/amazon-aws/route-53-resolver-security.md
index 72e85cf277..f14eb6f738 100644
--- a/docs/integrations/amazon-aws/route-53-resolver-security.md
+++ b/docs/integrations/amazon-aws/route-53-resolver-security.md
@@ -61,7 +61,7 @@ import ViewDashboards from '../../reuse/apps/view-dashboards.md';
### Query Logging Overview
-The Query Logging Overview Dashboard provides insights into DNS activities such as DNS queries by location, VPC and instance ID. Additional security information is provided, including blocked and alerted DNS queries from the Route 53 DNS Resolver Firewall, and Threat Intel matches from Sumo Logic's CrowdStrike integration.
+The Query Logging Overview Dashboard provides insights into DNS activities such as DNS queries by location, VPC and instance ID. Additional security information is provided, including blocked and alerted DNS queries from the Route 53 DNS Resolver Firewall, and threat intel matches from Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
}) @@ -152,7 +152,7 @@ Panels include:
### Threat Intel
-The Threat Intel Dashboard provides details of AWS DNS Resolver Queries that matches the built-in CrowdStrike threat intelligence data with known malicious IP addresses and Domains, allowing for real-time security analytics to help detect threats in your environment and protect against cyber attacks.
+The Threat Intel Dashboard provides details of AWS DNS Resolver Queries that matches the Sumo Logic [threat intelligence](/docs/security/threat-intelligence/) data with known malicious IP addresses and Domains, allowing for real-time security analytics to help detect threats in your environment and protect against cyber attacks.
@@ -152,7 +152,7 @@ Panels include:
### Threat Intel
-The Threat Intel Dashboard provides details of AWS DNS Resolver Queries that matches the built-in CrowdStrike threat intelligence data with known malicious IP addresses and Domains, allowing for real-time security analytics to help detect threats in your environment and protect against cyber attacks.
+The Threat Intel Dashboard provides details of AWS DNS Resolver Queries that matches the Sumo Logic [threat intelligence](/docs/security/threat-intelligence/) data with known malicious IP addresses and Domains, allowing for real-time security analytics to help detect threats in your environment and protect against cyber attacks.
}) diff --git a/docs/integrations/amazon-aws/threat-intel.md b/docs/integrations/amazon-aws/threat-intel.md
index 75c1d84fcb..5c4e0d739c 100644
--- a/docs/integrations/amazon-aws/threat-intel.md
+++ b/docs/integrations/amazon-aws/threat-intel.md
@@ -1,14 +1,14 @@
---
id: threat-intel
title: AWS Threat Intel
-description: The Threat Intel for AWS App correlates CrowdStrike threat intelligence data with your AWS log data, allowing for real-time security analytics to help detect threats in your environment and protect against cyber-attacks.
+description: The Threat Intel for AWS App correlates Sumo Logic threat intelligence data with your AWS log data, allowing for real-time security analytics to help detect threats in your environment and protect against cyber-attacks.
---
import useBaseUrl from '@docusaurus/useBaseUrl';
diff --git a/docs/integrations/amazon-aws/threat-intel.md b/docs/integrations/amazon-aws/threat-intel.md
index 75c1d84fcb..5c4e0d739c 100644
--- a/docs/integrations/amazon-aws/threat-intel.md
+++ b/docs/integrations/amazon-aws/threat-intel.md
@@ -1,14 +1,14 @@
---
id: threat-intel
title: AWS Threat Intel
-description: The Threat Intel for AWS App correlates CrowdStrike threat intelligence data with your AWS log data, allowing for real-time security analytics to help detect threats in your environment and protect against cyber-attacks.
+description: The Threat Intel for AWS App correlates Sumo Logic threat intelligence data with your AWS log data, allowing for real-time security analytics to help detect threats in your environment and protect against cyber-attacks.
---
import useBaseUrl from '@docusaurus/useBaseUrl';
}) -The Threat Intel for AWS App correlates CrowdStrike threat intelligence data with your AWS log data, allowing for real-time security analytics to help detect threats in your environment and protect against cyber-attacks. The Threat Intel for AWS App scans your AWS CloudTrail, AWS ELB and AWS VPC Flow logs for threats based on IP address.
+The Threat Intel for AWS App correlates Sumo Logic [threat intelligence](/docs/security/threat-intelligence/) data with your AWS log data, allowing for real-time security analytics to help detect threats in your environment and protect against cyber-attacks. The Threat Intel for AWS App scans your AWS CloudTrail, AWS ELB and AWS VPC Flow logs for threats based on IP address.
The Sumo Logic Threat Intel lookup database is only available with Sumo Logic Enterprise and Professions accounts, or during a 30-day trial period. The Threat Intel lookup database is not available for Sumo Logic Free accounts.
@@ -71,7 +71,7 @@ Use this dashboard for details on potential threats and IOCs for AWS CloudTrail.
-The Threat Intel for AWS App correlates CrowdStrike threat intelligence data with your AWS log data, allowing for real-time security analytics to help detect threats in your environment and protect against cyber-attacks. The Threat Intel for AWS App scans your AWS CloudTrail, AWS ELB and AWS VPC Flow logs for threats based on IP address.
+The Threat Intel for AWS App correlates Sumo Logic [threat intelligence](/docs/security/threat-intelligence/) data with your AWS log data, allowing for real-time security analytics to help detect threats in your environment and protect against cyber-attacks. The Threat Intel for AWS App scans your AWS CloudTrail, AWS ELB and AWS VPC Flow logs for threats based on IP address.
The Sumo Logic Threat Intel lookup database is only available with Sumo Logic Enterprise and Professions accounts, or during a 30-day trial period. The Threat Intel lookup database is not available for Sumo Logic Free accounts.
@@ -71,7 +71,7 @@ Use this dashboard for details on potential threats and IOCs for AWS CloudTrail.
}) -* **Threats by Geo Location.** View the geo location of threats by IP address that have been identified by Crowdstrike with a malicious confidence of High over the last 24 hours.
+* **Threats by Geo Location.** View the geo location of threats by IP address that have been identified by Sumo Logic [threat intelligence](/docs/security/threat-intelligence/) with a malicious confidence of High over the last 24 hours.
* **Threats Associated with CloudTrail Events.** Track events in CloudTrail by event time where the malicious confidence is High by source user, source IP address, event name, AWS region, result, malicious confidence, label name, threat malware families, threat last updated, and count for the last 24 hours.
* **Threats by Events and I.P.** Compare events where the malicious confidence is High by source IP address over the last 24 hours.
* **Threats Over Time by Result.** Compare successful versus access denied threats with a High malicious confidence for the last 24 hours, timesliced by hour.
diff --git a/docs/integrations/amazon-aws/waf.md b/docs/integrations/amazon-aws/waf.md
index 617a6f3f0d..b49ac50e8f 100644
--- a/docs/integrations/amazon-aws/waf.md
+++ b/docs/integrations/amazon-aws/waf.md
@@ -54,13 +54,20 @@ The Sumo Logic app for AWS WAF analyzes traffic flowing through AWS WAF and auto
}
```
-## Sample queries
-
+## Sample queries
```sql title="Client IP Threat Info"
_sourceCategory=AWS/WAF {{client_ip}}
| parse "\"httpMethod\":\"*\"," as httpMethod,"\"httpVersion\":\"*\"," as httpVersion,"\"uri\":\"*\"," as uri, "{\"clientIp\":\"*\",\"country\":\"*\"" as clientIp,country, "\"action\":\"*\"" as action, "\"matchingNonTerminatingRules\":[*]" as matchingNonTerminatingRules, "\"rateBasedRuleList\":[*]" as rateBasedRuleList, "\"ruleGroupList\":[*]" as ruleGroupList, "\"httpSourceId\":\"*\"" as httpSourceId, "\"httpSourceName\":\"*\"" as httpSourceName, "\"terminatingRuleType\":\"*\"" as terminatingRuleType, "\"terminatingRuleId\":\"*\"" as terminatingRuleId, "\"webaclId\":\"*\"" as webaclId nodrop
| lookup type, actor, raw, threatlevel as malicious_confidence from sumo://threat/cs on threat=clientip
```
+
## Collecting logs for the AWS WAF app
diff --git a/docs/integrations/microsoft-azure/teams.md b/docs/integrations/microsoft-azure/teams.md
index 87239e9722..b1677da67b 100644
--- a/docs/integrations/microsoft-azure/teams.md
+++ b/docs/integrations/microsoft-azure/teams.md
@@ -87,7 +87,7 @@ The Teams - User Sessions dashboard provides an in depth view of the user logins
Use this dashboard to:
* Identify user sessions relative to their locations and compare login statistics over time.
* Understand the client platforms and versions that are being used.
-* Report on login IP addresses correlated to potential threats via Crowdstrike.
+* Report on login IP addresses correlated to potential threats via Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
-* **Threats by Geo Location.** View the geo location of threats by IP address that have been identified by Crowdstrike with a malicious confidence of High over the last 24 hours.
+* **Threats by Geo Location.** View the geo location of threats by IP address that have been identified by Sumo Logic [threat intelligence](/docs/security/threat-intelligence/) with a malicious confidence of High over the last 24 hours.
* **Threats Associated with CloudTrail Events.** Track events in CloudTrail by event time where the malicious confidence is High by source user, source IP address, event name, AWS region, result, malicious confidence, label name, threat malware families, threat last updated, and count for the last 24 hours.
* **Threats by Events and I.P.** Compare events where the malicious confidence is High by source IP address over the last 24 hours.
* **Threats Over Time by Result.** Compare successful versus access denied threats with a High malicious confidence for the last 24 hours, timesliced by hour.
diff --git a/docs/integrations/amazon-aws/waf.md b/docs/integrations/amazon-aws/waf.md
index 617a6f3f0d..b49ac50e8f 100644
--- a/docs/integrations/amazon-aws/waf.md
+++ b/docs/integrations/amazon-aws/waf.md
@@ -54,13 +54,20 @@ The Sumo Logic app for AWS WAF analyzes traffic flowing through AWS WAF and auto
}
```
-## Sample queries
-
+## Sample queries
```sql title="Client IP Threat Info"
_sourceCategory=AWS/WAF {{client_ip}}
| parse "\"httpMethod\":\"*\"," as httpMethod,"\"httpVersion\":\"*\"," as httpVersion,"\"uri\":\"*\"," as uri, "{\"clientIp\":\"*\",\"country\":\"*\"" as clientIp,country, "\"action\":\"*\"" as action, "\"matchingNonTerminatingRules\":[*]" as matchingNonTerminatingRules, "\"rateBasedRuleList\":[*]" as rateBasedRuleList, "\"ruleGroupList\":[*]" as ruleGroupList, "\"httpSourceId\":\"*\"" as httpSourceId, "\"httpSourceName\":\"*\"" as httpSourceName, "\"terminatingRuleType\":\"*\"" as terminatingRuleType, "\"terminatingRuleId\":\"*\"" as terminatingRuleId, "\"webaclId\":\"*\"" as webaclId nodrop
| lookup type, actor, raw, threatlevel as malicious_confidence from sumo://threat/cs on threat=clientip
```
+
## Collecting logs for the AWS WAF app
diff --git a/docs/integrations/microsoft-azure/teams.md b/docs/integrations/microsoft-azure/teams.md
index 87239e9722..b1677da67b 100644
--- a/docs/integrations/microsoft-azure/teams.md
+++ b/docs/integrations/microsoft-azure/teams.md
@@ -87,7 +87,7 @@ The Teams - User Sessions dashboard provides an in depth view of the user logins
Use this dashboard to:
* Identify user sessions relative to their locations and compare login statistics over time.
* Understand the client platforms and versions that are being used.
-* Report on login IP addresses correlated to potential threats via Crowdstrike.
+* Report on login IP addresses correlated to potential threats via Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
}) diff --git a/docs/integrations/product-list/product-list-a-l.md b/docs/integrations/product-list/product-list-a-l.md
index 52ea74b3af..042d03c2cf 100644
--- a/docs/integrations/product-list/product-list-a-l.md
+++ b/docs/integrations/product-list/product-list-a-l.md
@@ -169,7 +169,7 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
|
diff --git a/docs/integrations/product-list/product-list-a-l.md b/docs/integrations/product-list/product-list-a-l.md
index 52ea74b3af..042d03c2cf 100644
--- a/docs/integrations/product-list/product-list-a-l.md
+++ b/docs/integrations/product-list/product-list-a-l.md
@@ -169,7 +169,7 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
| }) | [Couchbase](https://www.couchbase.com/) | Apps:
| [Couchbase](https://www.couchbase.com/) | Apps:- [Couchbase](/docs/integrations/databases/couchbase/)
- [Couchbase - OpenTelemetry](/docs/integrations/databases/opentelemetry/couchbase-opentelemetry/) | |
}) | [Cribl](https://cribl.io/) | Automation integration: [Cribl](/docs/platform-services/automation-service/app-central/integrations/cribl/)
| [Cribl](https://cribl.io/) | Automation integration: [Cribl](/docs/platform-services/automation-service/app-central/integrations/cribl/) Partner integration: [Cribl](https://docs.cribl.io/stream/destinations-sumo-logic/) | |
}) | [Criminal IP](https://www.criminalip.io/) | Automation integration: [Criminal IP](/docs/platform-services/automation-service/app-central/integrations/criminal-ip) |
-|
| [Criminal IP](https://www.criminalip.io/) | Automation integration: [Criminal IP](/docs/platform-services/automation-service/app-central/integrations/criminal-ip) |
-| }) | [CrowdStrike](https://www.crowdstrike.com/) | Apps:
| [CrowdStrike](https://www.crowdstrike.com/) | Apps: - [CrowdStrike Falcon Endpoint Protection](/docs/integrations/security-threat-detection/crowdstrike-falcon-endpoint-protection/)
- [CrowdStrike Falcon FileVantage](/docs/integrations/saas-cloud/crowdstrike-falcon-filevantage/)
- [Threat Intel Quick Analysis](/docs/integrations/security-threat-detection/threat-intel-quick-analysis/)
- [CrowdStrike FDR Host Inventory](/docs/integrations/saas-cloud/crowdstrike-fdr-host-inventory)
- [CrowdStrike Spotlight](/docs/integrations/saas-cloud/crowdstrike-spotlight)
Automation integrations:
- [CrowdStrike Falcon](/docs/platform-services/automation-service/app-central/integrations/crowdstrike-falcon/)
- [CrowdStrike Falcon Discover](/docs/platform-services/automation-service/app-central/integrations/crowdstrike-falcon-discover/)
- [CrowdStrike Falcon Intelligence](/docs/platform-services/automation-service/app-central/integrations/crowdstrike-falcon-intelligence/)
- [CrowdStrike Falcon Sandbox](/docs/platform-services/automation-service/app-central/integrations/crowdstrike-falcon-sandbox/)
Cloud SIEM integrations:
- [CrowdStrike](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/79ade329-b6d4-43ae-8db1-2a9cc45c0fb0.md)
- [PreemptSecurity](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/15c77a62-0fbb-4a60-9fae-ead49ec423f9.md)
Collectors:
- [CrowdStrike Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-source/)
- [Crowdstrike FDR Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-fdr-source/)
- [CrowdStrike FDR Host Inventory Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-fdr-host-inventory-source/)
- [CrowdStrike FileVantage Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-filevantage-source/)
- [CrowdStrike Spotlight Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-spotlight-source/) | +|
}) | [CrowdStrike](https://www.crowdstrike.com/) | Apps:
| [CrowdStrike](https://www.crowdstrike.com/) | Apps: - [CrowdStrike Falcon Endpoint Protection](/docs/integrations/security-threat-detection/crowdstrike-falcon-endpoint-protection/)
- [CrowdStrike Falcon FileVantage](/docs/integrations/saas-cloud/crowdstrike-falcon-filevantage/)
- [Threat Intel Quick Analysis](/docs/integrations/security-threat-detection/threat-intel-quick-analysis/)
- [CrowdStrike FDR Host Inventory](/docs/integrations/saas-cloud/crowdstrike-fdr-host-inventory)
- [CrowdStrike Spotlight](/docs/integrations/saas-cloud/crowdstrike-spotlight)
Automation integrations:
- [CrowdStrike Falcon](/docs/platform-services/automation-service/app-central/integrations/crowdstrike-falcon/)
- [CrowdStrike Falcon Discover](/docs/platform-services/automation-service/app-central/integrations/crowdstrike-falcon-discover/)
- [CrowdStrike Falcon Intelligence](/docs/platform-services/automation-service/app-central/integrations/crowdstrike-falcon-intelligence/)
- [CrowdStrike Falcon Sandbox](/docs/platform-services/automation-service/app-central/integrations/crowdstrike-falcon-sandbox/)
Cloud SIEM integrations:
- [CrowdStrike](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/79ade329-b6d4-43ae-8db1-2a9cc45c0fb0.md)
- [PreemptSecurity](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/15c77a62-0fbb-4a60-9fae-ead49ec423f9.md)
Collectors:
- [CrowdStrike Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-source/)
- [Crowdstrike FDR Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-fdr-source/)
- [CrowdStrike FDR Host Inventory Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-fdr-host-inventory-source/)
- [CrowdStrike FileVantage Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-filevantage-source/)
- [CrowdStrike Spotlight Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-spotlight-source/)
- [CrowdStrike Threat Intel Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-threat-intel-source/) | |
}) | [Cuckoo](https://cuckoo.readthedocs.io/en/latest/#) | Automation integration: [Cuckoo](/docs/platform-services/automation-service/app-central/integrations/cuckoo/) |
|
| [Cuckoo](https://cuckoo.readthedocs.io/en/latest/#) | Automation integration: [Cuckoo](/docs/platform-services/automation-service/app-central/integrations/cuckoo/) |
| }) | [CyberArk](https://www.cyberark.com/) | Automation integrations:
| [CyberArk](https://www.cyberark.com/) | Automation integrations: - [CyberArk AAM](/docs/platform-services/automation-service/app-central/integrations/cyberark-aam/)
- [CyberArk PAM](/docs/platform-services/automation-service/app-central/integrations/cyberark-pam)
Cloud SIEM integration: [CyberArk](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/8a3d333e-ffad-49ed-9edd-0cf1c797b24f.md)
Collector:
- [CyberArk EPM Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/cyberark-source/)
- [CyberArk Audit Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/cyberark-audit-source/) | |
}) | [CyberInt](https://cyberint.com/) | Automation integration: [Cyberint](/docs/platform-services/automation-service/app-central/integrations/cyberint) |
@@ -251,8 +251,8 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
|
| [CyberInt](https://cyberint.com/) | Automation integration: [Cyberint](/docs/platform-services/automation-service/app-central/integrations/cyberint) |
@@ -251,8 +251,8 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
| }) | [GitHub](https://github.com/) | App: [GitHub](/docs/integrations/app-development/github/)
| [GitHub](https://github.com/) | App: [GitHub](/docs/integrations/app-development/github/) Automation integration: [GitHub](/docs/platform-services/automation-service/app-central/integrations/github/)
Cloud SIEM integration: [Github](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/193c791a-bb10-4742-a429-1256535f888b.md#vendors-github)
Community app: [Sumo Logic for GitHub Actions](https://github.com/SumoLogic/sumologic-content/tree/master/GitHub/GitHub_Actions) | |
}) | [GitLab](https://about.gitlab.com/) | App: [GitLab](/docs/integrations/app-development/gitlab/)
| [GitLab](https://about.gitlab.com/) | App: [GitLab](/docs/integrations/app-development/gitlab/) Automation integration: [GitLab](/docs/platform-services/automation-service/app-central/integrations/gitlab/) | |
Automation integrations:
- [Gmail](/docs/platform-services/automation-service/app-central/integrations/gmail/)
- [Gmail Multiple Mailbox](/docs/platform-services/automation-service/app-central/integrations/gmail-multiple-mailbox/)
Collector: [Gmail Trace Logs Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/gmail-tracelogs-source) | -|
}) | [Google](https://about.google/) | Apps:
| [Google](https://about.google/) | Apps: - [Google App Engine](/docs/integrations/google/app-engine/)
- [Google BigQuery](/docs/integrations/google/bigquery/)
- [Google Cloud AlloyDB for PostgreSQL](/docs/integrations/google/cloud-alloydb-for-postgresql/)
- [Google Cloud API Gateway](/docs/integrations/google/cloud-api-gateway/)
- [Google Cloud APIs](/docs/integrations/google/cloud-apis/)
- [Google Cloud Armor](/docs/integrations/google/cloud-armor/)
- [Google Cloud Audit](/docs/integrations/google/cloud-audit)
- [Google Cloud Auto Scaler](/docs/integrations/google/cloud-auto-scaler)
- [Google Cloud Backup for GKE](/docs/integrations/google/cloud-backup-for-gke/)
- [Google Cloud BigQuery BI Engine](/docs/integrations/google/cloud-bigquery-bi-engine/)
- [Google Cloud Bigtable](/docs/integrations/google/cloud-bigtable/)
- [Google Cloud Certificate Authority Service](/docs/integrations/google/cloud-certificate-authority-service/)
- [Google Cloud Certificate Manager](/docs/integrations/google/cloud-certificate-manager/)
- [Google Cloud Composer](/docs/integrations/google/cloud-composer/)
- [Google Compute Engine](/docs/integrations/google/compute-engine/)
- [Google Cloud Dataflow](/docs/integrations/google/cloud-dataflow/)
- [Google Cloud Dataproc](/docs/integrations/google/cloud-dataproc/)
- [Google Cloud Dataproc Metastore](/docs/integrations/google/cloud-dataproc-metastore/)
- [Google Cloud Datastore](/docs/integrations/google/cloud-datastore/)
- [Google Cloud Datastream](/docs/integrations/google/cloud-datastream/)
- [Google Cloud Deploy](/docs/integrations/google/cloud-deploy/)
- [Google Cloud Filestore](/docs/integrations/google/cloud-filestore/)
- [Google Cloud Firebase](/docs/integrations/google/cloud-firebase/)
- [Google Cloud Firestore](/docs/integrations/google/cloud-firestore/)
- [Google Cloud Firewall](/docs/integrations/google/cloud-firewall/)
- [Google Cloud Fleet Engine](/docs/integrations/google/cloud-fleet-engine/)
- [Google Cloud Functions](/docs/integrations/google/cloud-functions/)
- [Google Cloud Interconnect](/docs/integrations/google/cloud-interconnect/)
- [Google Cloud Load Balancing](/docs/integrations/google/cloud-load-balancing/)
- [Google Cloud Logging](/docs/integrations/google/cloud-logging/)
- [Google Cloud Memorystore for Redis](/docs/integrations/google/cloud-memorystore-for-redis/)
- [Google Cloud Net App Cloud Volumes Service](/docs/integrations/google/cloud-net-app-cloud-volumes-service/)
- [Google Cloud Network Topology](/docs/integrations/google/cloud-network-topology/)
- [Google Cloud Pub Sub](/docs/integrations/google/cloud-pub-sub/)
- [Google Cloud Router](/docs/integrations/google/cloud-router/)
- [Google Cloud Run](/docs/integrations/google/cloud-run/)
- [Google Cloud Spanner](/docs/integrations/google/cloud-spanner/)
- [Google Cloud SQL](/docs/integrations/google/cloud-sql/)
- [Google Cloud Storage](/docs/integrations/google/cloud-storage/)
- [Google Cloud Tasks](/docs/integrations/google/cloud-tasks/)
- [Google Cloud TPU](/docs/integrations/google/cloud-tpu/)
- [Google Cloud Trace](/docs/integrations/google/cloud-trace/)
- [Google Cloud Traffic Director](/docs/integrations/google/cloud-traffic-director/)
- [Google Cloud Vertex AI](/docs/integrations/google/cloud-vertex-ai/)
- [Google Cloud VPC](/docs/integrations/google/cloud-vpc/)
- [Google Cloud VPN](/docs/integrations/google/cloud-vpn/)
- [Google Kubernetes Engine (GKE)](/docs/integrations/google/kubernetes-engine/)
Automation integrations:
- [Chronicle](/docs/platform-services/automation-service/app-central/integrations/chronicle/)
- [Google Chat](/docs/platform-services/automation-service/app-central/integrations/google-chat/)
- [Google Safe Browsing](/docs/platform-services/automation-service/app-central/integrations/google-safe-browsing/)
- [Mandiant Advantage Threat intelligence](/docs/platform-services/automation-service/app-central/integrations/mandiant-advantage-threat-intelligence/)
Cloud SIEM integration: [Google](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/45601247-66a5-4c9c-b3af-c422f5b4cbeb.md)
Collectors:
- [Google BigQuery Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/google-bigquery-source/)
- [GCP Metrics Source](/docs/send-data/hosted-collectors/google-source/gcp-metrics-source/)
- [Google Cloud Platform (GCP) Source](/docs/send-data/hosted-collectors/google-source/google-cloud-platform-source/)
Community app: [Sumo Logic for GCP Balancer Metrics](https://github.com/SumoLogic/sumologic-content/tree/master/GCP/Load_Balancer_Metrics) | -|
Automation integrations:
- [Google Alert Center](/docs/platform-services/automation-service/app-central/integrations/google-alert-center/)
- [Google Admin](/docs/platform-services/automation-service/app-central/integrations/google-admin/)
- [Google Drive](/docs/platform-services/automation-service/app-central/integrations/google-drive/)
Collectors: [Google Workspace AlertCenter Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/google-workspace-alertcenter/)
- [Google Workspace Apps Audit Source](/docs/send-data/hosted-collectors/google-source/google-workspace-apps-audit-source/)
- [Google Workspace User Inventory Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/google-workspace-source/) | +|
}) | [Google](https://about.google/) | Apps:
| [Google](https://about.google/) | Apps: - [Google App Engine](/docs/integrations/google/app-engine/)
- [Google BigQuery](/docs/integrations/google/bigquery/)
- [Google Cloud AlloyDB for PostgreSQL](/docs/integrations/google/cloud-alloydb-for-postgresql/)
- [Google Cloud API Gateway](/docs/integrations/google/cloud-api-gateway/)
- [Google Cloud APIs](/docs/integrations/google/cloud-apis/)
- [Google Cloud Armor](/docs/integrations/google/cloud-armor/)
- [Google Cloud Audit](/docs/integrations/google/cloud-audit)
- [Google Cloud Auto Scaler](/docs/integrations/google/cloud-auto-scaler)
- [Google Cloud Backup for GKE](/docs/integrations/google/cloud-backup-for-gke/)
- [Google Cloud BigQuery BI Engine](/docs/integrations/google/cloud-bigquery-bi-engine/)
- [Google Cloud Bigtable](/docs/integrations/google/cloud-bigtable/)
- [Google Cloud Certificate Authority Service](/docs/integrations/google/cloud-certificate-authority-service/)
- [Google Cloud Certificate Manager](/docs/integrations/google/cloud-certificate-manager/)
- [Google Cloud Composer](/docs/integrations/google/cloud-composer/)
- [Google Compute Engine](/docs/integrations/google/compute-engine/)
- [Google Cloud Dataflow](/docs/integrations/google/cloud-dataflow/)
- [Google Cloud Dataproc](/docs/integrations/google/cloud-dataproc/)
- [Google Cloud Dataproc Metastore](/docs/integrations/google/cloud-dataproc-metastore/)
- [Google Cloud Datastore](/docs/integrations/google/cloud-datastore/)
- [Google Cloud Datastream](/docs/integrations/google/cloud-datastream/)
- [Google Cloud Deploy](/docs/integrations/google/cloud-deploy/)
- [Google Cloud Filestore](/docs/integrations/google/cloud-filestore/)
- [Google Cloud Firebase](/docs/integrations/google/cloud-firebase/)
- [Google Cloud Firestore](/docs/integrations/google/cloud-firestore/)
- [Google Cloud Firewall](/docs/integrations/google/cloud-firewall/)
- [Google Cloud Fleet Engine](/docs/integrations/google/cloud-fleet-engine/)
- [Google Cloud Functions](/docs/integrations/google/cloud-functions/)
- [Google Cloud Interconnect](/docs/integrations/google/cloud-interconnect/)
- [Google Cloud Load Balancing](/docs/integrations/google/cloud-load-balancing/)
- [Google Cloud Logging](/docs/integrations/google/cloud-logging/)
- [Google Cloud Memorystore for Redis](/docs/integrations/google/cloud-memorystore-for-redis/)
- [Google Cloud Net App Cloud Volumes Service](/docs/integrations/google/cloud-net-app-cloud-volumes-service/)
- [Google Cloud Network Topology](/docs/integrations/google/cloud-network-topology/)
- [Google Cloud Pub Sub](/docs/integrations/google/cloud-pub-sub/)
- [Google Cloud Router](/docs/integrations/google/cloud-router/)
- [Google Cloud Run](/docs/integrations/google/cloud-run/)
- [Google Cloud Spanner](/docs/integrations/google/cloud-spanner/)
- [Google Cloud SQL](/docs/integrations/google/cloud-sql/)
- [Google Cloud Storage](/docs/integrations/google/cloud-storage/)
- [Google Cloud Tasks](/docs/integrations/google/cloud-tasks/)
- [Google Cloud TPU](/docs/integrations/google/cloud-tpu/)
- [Google Cloud Trace](/docs/integrations/google/cloud-trace/)
- [Google Cloud Traffic Director](/docs/integrations/google/cloud-traffic-director/)
- [Google Cloud Vertex AI](/docs/integrations/google/cloud-vertex-ai/)
- [Google Cloud VPC](/docs/integrations/google/cloud-vpc/)
- [Google Cloud VPN](/docs/integrations/google/cloud-vpn/)
- [Google Kubernetes Engine (GKE)](/docs/integrations/google/kubernetes-engine/)
Automation integrations:
- [Chronicle](/docs/platform-services/automation-service/app-central/integrations/chronicle/)
- [Google Chat](/docs/platform-services/automation-service/app-central/integrations/google-chat/)
- [Google Safe Browsing](/docs/platform-services/automation-service/app-central/integrations/google-safe-browsing/)
- [Mandiant Advantage Threat intelligence](/docs/platform-services/automation-service/app-central/integrations/mandiant-advantage-threat-intelligence/)
Cloud SIEM integration: [Google](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/45601247-66a5-4c9c-b3af-c422f5b4cbeb.md)
Collectors:
- [Google BigQuery Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/google-bigquery-source/)
- [GCP Metrics Source](/docs/send-data/hosted-collectors/google-source/gcp-metrics-source/)
- [Google Cloud Platform (GCP) Source](/docs/send-data/hosted-collectors/google-source/google-cloud-platform-source/)
- [Mandiant Threat Intel Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/mandiant-threat-intel-source/)
Community app: [Sumo Logic for GCP Balancer Metrics](https://github.com/SumoLogic/sumologic-content/tree/master/GCP/Load_Balancer_Metrics) | +|
Automation integrations:
- [Google Alert Center](/docs/platform-services/automation-service/app-central/integrations/google-alert-center/)
- [Google Admin](/docs/platform-services/automation-service/app-central/integrations/google-admin/)
- [Google Drive](/docs/platform-services/automation-service/app-central/integrations/google-drive/)
Collector: [Google Workspace AlertCenter Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/google-workspace-alertcenter/)
- [Google Workspace Apps Audit Source](/docs/send-data/hosted-collectors/google-source/google-workspace-apps-audit-source/)
- [Google Workspace User Inventory Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/google-workspace-source/)
- [G Suite Alert Center - Cloud SIEM](/docs/cse/ingestion/ingestion-sources-for-cloud-siem/g-suite-alert-center/) | |
}) | [Grafana](https://grafana.com/) | Webhook: [Grafana OnCall](/docs/integrations/webhooks/grafana-oncall/) |
|
| [Grafana](https://grafana.com/) | Webhook: [Grafana OnCall](/docs/integrations/webhooks/grafana-oncall/) |
| }) | [Gremlin](https://www.gremlin.com/) | Webhook: [Gremlin](/docs/integrations/webhooks/gremlin/) |
|
| [Gremlin](https://www.gremlin.com/) | Webhook: [Gremlin](/docs/integrations/webhooks/gremlin/) |
| }) | [GreyNoise](https://www.greynoise.io/) | Automation integration: [GreyNoise](/docs/platform-services/automation-service/app-central/integrations/greynoise/) |
@@ -286,7 +286,7 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
|
| [GreyNoise](https://www.greynoise.io/) | Automation integration: [GreyNoise](/docs/platform-services/automation-service/app-central/integrations/greynoise/) |
@@ -286,7 +286,7 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
| }) | [ISC](https://www.isc.org/) | Cloud SIEM integration: [ISC](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/1583cfd2-7ece-4060-991b-06dcf8567943.md) |
|
| [ISC](https://www.isc.org/) | Cloud SIEM integration: [ISC](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/1583cfd2-7ece-4060-991b-06dcf8567943.md) |
| }) | [Istio](https://istio.io/) | App: [Istio](/docs/integrations/saas-cloud/istio/) |
-|
| [Istio](https://istio.io/) | App: [Istio](/docs/integrations/saas-cloud/istio/) |
-| }) | [Intel471](https://intel471.com/) | Automation integration: [Intel471](/docs/platform-services/automation-service/app-central/integrations/intel-471/) |
+|
| [Intel471](https://intel471.com/) | Automation integration: [Intel471](/docs/platform-services/automation-service/app-central/integrations/intel-471/) |
+| }) | [Intel471](https://intel471.com/) | Automation integration: [Intel471](/docs/platform-services/automation-service/app-central/integrations/intel-471/)
| [Intel471](https://intel471.com/) | Automation integration: [Intel471](/docs/platform-services/automation-service/app-central/integrations/intel-471/) Collector: [Intel471 Threat Intel Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/intel471-threat-intel-source) | |
}) | [Intelligence X](https://intelx.io/) | Automation integration: [Intelligence X](/docs/platform-services/automation-service/app-central/integrations/intelligence-x/) |
|
| [Intelligence X](https://intelx.io/) | Automation integration: [Intelligence X](/docs/platform-services/automation-service/app-central/integrations/intelligence-x/) |
| }) | [Intezer](https://intezer.com/) | Automation integration: [Intezer](/docs/platform-services/automation-service/app-central/integrations/intezer/) |
|
| [Intezer](https://intezer.com/) | Automation integration: [Intezer](/docs/platform-services/automation-service/app-central/integrations/intezer/) |
| }) | [Intsights TIP](https://intsights.com/) | Automation integration: [Intsights TIP](/docs/platform-services/automation-service/app-central/integrations/intsights-tip/) |
diff --git a/docs/integrations/product-list/product-list-m-z.md b/docs/integrations/product-list/product-list-m-z.md
index 4e2628b762..6377604462 100644
--- a/docs/integrations/product-list/product-list-m-z.md
+++ b/docs/integrations/product-list/product-list-m-z.md
@@ -157,6 +157,7 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
|
| [Intsights TIP](https://intsights.com/) | Automation integration: [Intsights TIP](/docs/platform-services/automation-service/app-central/integrations/intsights-tip/) |
diff --git a/docs/integrations/product-list/product-list-m-z.md b/docs/integrations/product-list/product-list-m-z.md
index 4e2628b762..6377604462 100644
--- a/docs/integrations/product-list/product-list-m-z.md
+++ b/docs/integrations/product-list/product-list-m-z.md
@@ -157,6 +157,7 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
| }) | [StackRox](https://www.stackrox.io/) | Collector: [StackRox](https://cdn.stackrox.io/integrations/sumologic-stackrox-app.pdf)
| [StackRox](https://www.stackrox.io/) | Collector: [StackRox](https://cdn.stackrox.io/integrations/sumologic-stackrox-app.pdf) Partner integration: [StackRox app](https://cdn.stackrox.io/integrations/sumologic-stackrox-app.pdf) | |
}) | [StatsD](https://www.datadoghq.com/blog/statsd/) | Collector: [Collect StatsD Metrics](/docs/send-data/collect-from-other-data-sources/collect-statsd-metrics/) |
|
| [StatsD](https://www.datadoghq.com/blog/statsd/) | Collector: [Collect StatsD Metrics](/docs/send-data/collect-from-other-data-sources/collect-statsd-metrics/) |
| }) | [Stellar Cyber](https://stellarcyber.ai/) | Automation integration: [Stellar Cyber Starlight](/docs/platform-services/automation-service/app-central/integrations/stellar-cyber-starlight/) |
+|
| [Stellar Cyber](https://stellarcyber.ai/) | Automation integration: [Stellar Cyber Starlight](/docs/platform-services/automation-service/app-central/integrations/stellar-cyber-starlight/) |
+| }) | [STIX](https://oasis-open.github.io/cti-documentation/) | Collectors:
| [STIX](https://oasis-open.github.io/cti-documentation/) | Collectors: - [STIX/TAXII 1 Client Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-1-client-source/)
- [STIX/TAXI 2 Client Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-2-client-source/) | |
}) | [Strimzi](https://strimzi.io/) | App: [Strimzi Kafka](/docs/integrations/containers-orchestration/strimzi-kafka/) |
|
| [Strimzi](https://strimzi.io/) | App: [Strimzi Kafka](/docs/integrations/containers-orchestration/strimzi-kafka/) |
| }) | [Stripe](https://stripe.com/) | Webhook: [Stripe](/docs/integrations/webhooks/stripe/) |
|
| [Stripe](https://stripe.com/) | Webhook: [Stripe](/docs/integrations/webhooks/stripe/) |
| }) | [Sucuri](https://sucuri.net/) | Cloud SIEM integration: [Sucuri](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/cdfd2ba0-77eb-4e11-b071-6f4d01fda607.md) |
@@ -226,6 +227,6 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
|
| [Sucuri](https://sucuri.net/) | Cloud SIEM integration: [Sucuri](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/cdfd2ba0-77eb-4e11-b071-6f4d01fda607.md) |
@@ -226,6 +227,6 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
| }) | [Zendesk](https://www.zendesk.com/) | App: [Zendesk](/docs/integrations/saas-cloud/zendesk/)
| [Zendesk](https://www.zendesk.com/) | App: [Zendesk](/docs/integrations/saas-cloud/zendesk/) Automation integration: [Zendesk](/docs/platform-services/automation-service/app-central/integrations/zendesk/)
Collector: [Zendesk Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/zendesk-source/) | |
}) | [Zenduty](https://www.zenduty.com/) | Webhook: [Zenduty](/docs/integrations/webhooks/zenduty/) |
|
| [Zenduty](https://www.zenduty.com/) | Webhook: [Zenduty](/docs/integrations/webhooks/zenduty/) |
| Collector: [Zero Networks Segment Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/zero-networks-segment-source/) | -|
}) | [ZeroFox](https://www.zerofox.com/) | Automation integration: [ZeroFOX](/docs/platform-services/automation-service/app-central/integrations/zerofox/)
| [ZeroFox](https://www.zerofox.com/) | Automation integration: [ZeroFOX](/docs/platform-services/automation-service/app-central/integrations/zerofox/) Partner integration: ZeroFox integration | +|
}) | [ZeroFox](https://www.zerofox.com/) | Automation integration: [ZeroFox](/docs/platform-services/automation-service/app-central/integrations/zerofox/)
| [ZeroFox](https://www.zerofox.com/) | Automation integration: [ZeroFox](/docs/platform-services/automation-service/app-central/integrations/zerofox/) Collector: [ZeroFox Threat Intel Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/zerofox-intel-source/)
Partner integration: ZeroFox integration | |
}) | [Zoom](https://zoom.us/) | App: [Zoom](/docs/integrations/saas-cloud/zoom/)
| [Zoom](https://zoom.us/) | App: [Zoom](/docs/integrations/saas-cloud/zoom/) Automation integration: [Zoom](/docs/platform-services/automation-service/app-central/integrations/zoom/)
Cloud SIEM integration: [Zoom](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/bda720cd-399c-4dcc-9289-19ad0c9cb221.md)
Collector: [Zoom Source](/docs/send-data/hosted-collectors/webhook-sources/zoom/) | |
}) | [Zscaler](https://www.zscaler.com/) | Apps:
| [Zscaler](https://www.zscaler.com/) | Apps: - [Zscaler Internet Access](/docs/integrations/security-threat-detection/zscaler-internet-access/)
- [Zscaler Private Access](/docs/integrations/security-threat-detection/zscaler-private-access/)
Automation integration: [Zscaler](/docs/platform-services/automation-service/app-central/integrations/zscaler/)
Cloud SIEM integration: [Zscaler](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/9dfd2223-1656-4faf-a38a-5a91978fa15e.md) | diff --git a/docs/integrations/saas-cloud/microsoft-exchange-trace-logs.md b/docs/integrations/saas-cloud/microsoft-exchange-trace-logs.md index 3727e69080..7a3563a00e 100644 --- a/docs/integrations/saas-cloud/microsoft-exchange-trace-logs.md +++ b/docs/integrations/saas-cloud/microsoft-exchange-trace-logs.md @@ -8,7 +8,7 @@ description: This Sumo Logic App for Microsoft Exchange Trace logs provides visi import useBaseUrl from '@docusaurus/useBaseUrl'; -The MessageTrace API offers insight into the handling of emails that have gone through Office 365 for an organization. The Sumo Logic Microsoft Exchange Trace Logs App provides information on the delivery status of messages including Delivered, Failed, Quarantined, Pending, and Spam. The app dashboard analyzes message size, sender and receiver locations, and provides threat analysis by utilizing the CrowdStrike threat detection feed. +The MessageTrace API offers insight into the handling of emails that have gone through Office 365 for an organization. The Sumo Logic Microsoft Exchange Trace Logs App provides information on the delivery status of messages including Delivered, Failed, Quarantined, Pending, and Spam. The app dashboard analyzes message size, sender and receiver locations, and provides threat analysis by utilizing Sumo Logic [threat intelligence](/docs/security/threat-intelligence/). ## Log types diff --git a/docs/integrations/security-threat-detection/akamai-security-events.md b/docs/integrations/security-threat-detection/akamai-security-events.md index 4ebb453529..bf7c5cc3d1 100644 --- a/docs/integrations/security-threat-detection/akamai-security-events.md +++ b/docs/integrations/security-threat-detection/akamai-security-events.md @@ -150,7 +150,7 @@ Use this dashboard to: ### Threat Intel -The **Akamai Security Events - Threat Intel** dashboard provides an at-a-glance view of threats analyzed using Crowdstrike Threat Feed. Dashboard panels display threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats. +The **Akamai Security Events - Threat Intel** dashboard provides an at-a-glance view of threats analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/). Dashboard panels display threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats.
}) diff --git a/docs/integrations/security-threat-detection/threat-intel-quick-analysis.md b/docs/integrations/security-threat-detection/threat-intel-quick-analysis.md
index 821d7d0c76..ba4e461ee7 100644
--- a/docs/integrations/security-threat-detection/threat-intel-quick-analysis.md
+++ b/docs/integrations/security-threat-detection/threat-intel-quick-analysis.md
@@ -2,43 +2,40 @@
id: threat-intel-quick-analysis
title: Threat Intel Quick Analysis
sidebar_label: Threat Intel Quick Analysis
-description: The Threat Intel Quick Analysis App correlates CrowdStrike's threat intelligence data with your own log data, providing security analytics that helps you to detect threats in your environment, while also protecting against sophisticated and persistent cyber-attacks.
+description: The Threat Intel Quick Analysis app correlates threat intelligence data with your own log data, providing security analytics that helps you to detect threats in your environment, while also protecting against sophisticated and persistent cyber-attacks.
---
import useBaseUrl from '@docusaurus/useBaseUrl';
diff --git a/docs/integrations/security-threat-detection/threat-intel-quick-analysis.md b/docs/integrations/security-threat-detection/threat-intel-quick-analysis.md
index 821d7d0c76..ba4e461ee7 100644
--- a/docs/integrations/security-threat-detection/threat-intel-quick-analysis.md
+++ b/docs/integrations/security-threat-detection/threat-intel-quick-analysis.md
@@ -2,43 +2,40 @@
id: threat-intel-quick-analysis
title: Threat Intel Quick Analysis
sidebar_label: Threat Intel Quick Analysis
-description: The Threat Intel Quick Analysis App correlates CrowdStrike's threat intelligence data with your own log data, providing security analytics that helps you to detect threats in your environment, while also protecting against sophisticated and persistent cyber-attacks.
+description: The Threat Intel Quick Analysis app correlates threat intelligence data with your own log data, providing security analytics that helps you to detect threats in your environment, while also protecting against sophisticated and persistent cyber-attacks.
---
import useBaseUrl from '@docusaurus/useBaseUrl';
}) -The Threat Intel Quick Analysis App correlates [CrowdStrike's](https://www.crowdstrike.com/sumologic/) threat intelligence data with your own log data, providing security analytics that helps you to detect threats in your environment, while also protecting against sophisticated and persistent cyber-attacks. The Threat Intel Quick Analysis App scans selected logs for threats based on **IP**, **URL**, **domain, Hash 256,** and **email**.
-
+The Threat Intel Quick Analysis app correlates [threat intelligence](/docs/security/threat-intelligence/) data with your own log data, providing security analytics that helps you to detect threats in your environment, while also protecting against sophisticated and persistent cyber-attacks. The Threat Intel Quick Analysis app scans selected logs for threats based on IP, URL, domain, SHA-256 hashes, and email.
## Log types
-The Threat Intel Quick Analysis App can be used for any type of logs, regardless of format. Ideal log sources should include **IP**, **URL**, **domain**, **Hash 256**, and/or **email** information.
-
+The Threat Intel Quick Analysis app can be used for any type of logs, regardless of format. Ideal log sources should include IP, URL, domain, SHA-256 hashes, and/or email information.
-## Installing the Threat Intel Quick Analysis App
+## Installing the Threat Intel Quick Analysis app
-This app contains generic regex expressions and thus may not perform well at very large scale. Once you are familiar with Sumo Logic, you can apply performance optimization techniques as described in [Threat Intel Optimization](#threat-intel-optimization). Alternatively, you can run this app on smaller and more specific data streams.
+This app contains generic regex expressions and thus may not perform well at very large scale. Once you are familiar with Sumo Logic, you can apply performance optimization techniques as described in [Threat Intel optimization](#threat-intel-optimization). Alternatively, you can run this app on smaller and more specific data streams.
-This section provides instructions on how to install the Threat Intel Quick Analysis App, and examples of each of dashboards. The preconfigured searches and dashboards provide easy-to-access visual insights into your data.
+This section provides instructions on how to install the Threat Intel Quick Analysis app, and examples of each of dashboards. The preconfigured searches and dashboards provide easy-to-access visual insights into your data.
import AppInstall from '../../reuse/apps/app-install.md';
-The Threat Intel Quick Analysis App correlates [CrowdStrike's](https://www.crowdstrike.com/sumologic/) threat intelligence data with your own log data, providing security analytics that helps you to detect threats in your environment, while also protecting against sophisticated and persistent cyber-attacks. The Threat Intel Quick Analysis App scans selected logs for threats based on **IP**, **URL**, **domain, Hash 256,** and **email**.
-
+The Threat Intel Quick Analysis app correlates [threat intelligence](/docs/security/threat-intelligence/) data with your own log data, providing security analytics that helps you to detect threats in your environment, while also protecting against sophisticated and persistent cyber-attacks. The Threat Intel Quick Analysis app scans selected logs for threats based on IP, URL, domain, SHA-256 hashes, and email.
## Log types
-The Threat Intel Quick Analysis App can be used for any type of logs, regardless of format. Ideal log sources should include **IP**, **URL**, **domain**, **Hash 256**, and/or **email** information.
-
+The Threat Intel Quick Analysis app can be used for any type of logs, regardless of format. Ideal log sources should include IP, URL, domain, SHA-256 hashes, and/or email information.
-## Installing the Threat Intel Quick Analysis App
+## Installing the Threat Intel Quick Analysis app
-This app contains generic regex expressions and thus may not perform well at very large scale. Once you are familiar with Sumo Logic, you can apply performance optimization techniques as described in [Threat Intel Optimization](#threat-intel-optimization). Alternatively, you can run this app on smaller and more specific data streams.
+This app contains generic regex expressions and thus may not perform well at very large scale. Once you are familiar with Sumo Logic, you can apply performance optimization techniques as described in [Threat Intel optimization](#threat-intel-optimization). Alternatively, you can run this app on smaller and more specific data streams.
-This section provides instructions on how to install the Threat Intel Quick Analysis App, and examples of each of dashboards. The preconfigured searches and dashboards provide easy-to-access visual insights into your data.
+This section provides instructions on how to install the Threat Intel Quick Analysis app, and examples of each of dashboards. The preconfigured searches and dashboards provide easy-to-access visual insights into your data.
import AppInstall from '../../reuse/apps/app-install.md';
-**Description:** The indicator that was queried. - ---- -#### `Type` -**Data Type:** string
-**Description:** The type of the indicator
-**Values:** - -* binary_string -* compile_time -* device_name -* domain -* email_address -* email_subject -* event_name -* file_mapping -* file_name -* file_path -* hash_ion -* hash_md5 -* hash_sha1 -* hash_sha256 -* ip_address -* ip_address_block -* mutex_name -* password -* persona_name -* phone_number -* port -* registry -* semaphore_name -* service_name -* url -* user_agent -* username -* x509_serial -* x509_subject - ---- -#### `report` -**Data Type:** string
-**Description:** The report ID that the indicator is associated with (e.g., CSIT-XXXX, CSIR-XXXX, etc). The report list is also represented under the labels list in the JSON data structure. - ---- -#### `actor` -**Data Type:** string
-**Description:** The named Actor that the indicator is associated with (e.g. panda, bear, spider, etc). The actor list is also represented under the labels list in the JSON data structure. - ---- -#### `malicious_confidence` - -**Data Type:** string
-**Description:** Indicates a confidence level by which an indicator is considered to be malicious. For example, a malicious file hash may always have a value of high while domains and IP addresses will very likely change over time. The malicious confidence level is also represented under the labels list in the JSON data structure.
-Once an indicator has been marked with a malicious confidence level, it continues to have that confidence level value until updated by CrowdStrike. If you think there is a false positive, please file a Support ticket, and we'll work with CrowdStrike to investigate the IOC in question and update the threat details.
-**Values:** - -* high -* medium -* low -* unverified—This indicator has not been verified by a CrowdStrike Intelligence analyst or an automated system. -* null—Indicates that Sumo Logic has no information about the threat record. - ---- -#### `published_date` - -**Data Type:** Timestamp in standard Unix time, UTC.
-**Description:** This is the date the indicator was first published. - ---- -#### `last_updated` +## Viewing Threat Intel Quick Analysis dashboards -**Data Type**: Timestamp in standard Unix time, UTC.
-**Description**: This is the date the indicator was last updated in CrowdStrike internal database. - ---- -#### `malware_family` - -**Data Type**: string
-**Description**: Indicates the malware family an indicator has been associated with. An indicator may be associated with more than one malware family. The malware family list is also represented under the labels list in the JSON data structure. - ---- -#### `kill_chain` - -**Data Type:** string
-**Description:** The point in the kill chain at which an indicator is associated. The kill chain list is also represented under the labels list in the JSON data structure.
-**Values:** -* reconnaissance—This indicator is associated with the research, identification, and selection of targets by a malicious actor. -* weaponization—This indicator is associated with assisting a malicious actor create malicious content. -* delivery—This indicator is associated with the delivery of an exploit or malicious payload. -* exploitation—This indicator is associated with the exploitation of a target system or environment. -* installation—This indicator is associated with the installation or infection of a target system with a remote access tool or other tool allowing for persistence in the target environment. -* c2 (Command and Control)—This indicator is associated with malicious actor command and control. -* actionOnObjectives—This indicator is associated with a malicious actor's desired effects and goals. - ---- -#### `labels` - -**Data Type:** string
-**Description:** The Intel Indicators API provides additional context around an indicator via the labels list. Some of these labels, such as `malicious_confidence` are accessible via the top-level data structure. All labels, including their associated timestamps, will be accessible via the labels list. The url string will look like: `https://intelapi.crowdstrike.com/indicator/v1/search/labels?equal=DomainType/DynamicDNS`. - -| IOC Type | Values | -|:-------------------|:----------------------------------------| -| **DomainType** | - DomainType/ActorControlled: It is believed the malicious actor is still in control of this domain.
- DomainType/DGA: Domain is the result of malware utilizing a domain generation algorithm.
- DomainType/DynamicDNS: Domain is owned or used by a dynamic DNS service.
- DomainType/DynamicDNS/Afraid: Domain is owned or used by the Afraid.org dynamic DNS service.
- DomainType/DynamicDNS/DYN: Domain is owned or used by the DYN dynamic DNS service.
- DomainType/DynamicDNS/Hostinger: Domain is owned or used by the Hostinger dynamic DNS service.
- DomainType/DynamicDNS/noIP: Domain is owned or used by the NoIP dynamic DNS service.
- DomainType/DynamicDNS/Oray: Domain is owned or used by the Oray dynamic DNS service.
- DomainType/KnownGood: Domain itself (or the domain portion of a URL) is known to be legitimate, despite having been associated with malware or malicious activity.
- DomainType/LegitimateCompromised: Domain does not typically pose a threat but has been compromised by a malicious actor and may be serving malicious content.
- DomainType/PhishingDomain: Domain has been observed to be part of a phishing campaign.
- DomainType/Sinkholed: Domain is being sinkholed, likely by a security research team. This indicates that, while traffic to the domain likely has a malicious source, the IP address to which it is resolving is controlled by a legitimate third party.
- DomainType/StrategicWebCompromise: Indicates targeted activity, often compromising a legitimate domain used as a watering hole by targeted organizations.
- DomainType/Unregistered: Domain is not currently registered with any registrars. | -| **EmailAddressType** | - EmailAddressType/DomainRegistrant: Email address has been supplied in the registration information for known malicious domains.
- EmailAddressType/SpearphishSender: Email address has been used to send spearphishing emails. | -| | **IntelNews**: The Intel Flash Report ID an indicator is associated with (e.g., IntelNews/NEWS-060520151900). | -| **IPAddressType** | - IPAddressType/HtranDestinationNode: An IP address with this label is being used as a destination address with the HTran Proxy Tool.
- IPAddressType/HtranProxy: An IP address with this label is being used as a relay or proxy node with the HTran Proxy Tool.
- IPAddressType/LegitimateCompromised: It is suspected an IP address with this label is compromised by malicious actors.
- IPAddressType/Parking: IP address is likely being used as a parking IP address.
- IPAddressType/PopularSite: IP address could be utilized for a variety of purposes and may appear more frequently than other IPs.
- IPAddressType/SharedWebHost: IP address may be hosting more than one website.
- IPAddressType/Sinkhole: IP address is likely a sinkhole being operated by a security researcher or vendor.
- IPAddressType/TorProxy: IP address is acting as a TOR (The Onion Router) proxy. | -| **Status** | - Status/ConfirmedActive: Indicator is likely to be currently supporting malicious activity.
- Status/ConfirmedInactive: Indicator is no longer used for malicious purposes. | -| **Target** | The activity associated with this indicator is known to target the indicated vertical sector:
- Aerospace
- Agricultural
- Chemical
- Defense
- Dissident
- Energy
- Extractive
- Financial
- Government
- Healthcare
- Insurance
- InternationalOrganizations
- Legal
- Manufacturing
- Media
- NGO
- Pharmaceutical
- Research
- Retail
- Shipping
- Technology
- Telecom
- Transportation
- Universities | -| **ThreatType** | - ThreatType/ClickFraud: Indicator is used by actors engaging in click or ad fraud.
- ThreatType/Commodity: Indicator is used with commodity-type malware such as Zeus or Pony Downloader.
- ThreatType/PointOfSale: Indicator is associated with activity targeting point-of-sale machines such as AlinaPoS or BlackPoS.
- ThreatType/Ransomware: Indicator is associated with ransomware malware such as Cryptolocker or Cryptowall.
- ThreatType/Suspicious: Indicator is not currently associated with a known threat type but should be considered suspicious.
- ThreatType/Targeted: Indicator is associated with a known actor suspected to be associated with a nation-state such as DEEP PANDA or ENERGETIC BEAR.
- ThreatType/TargetedCrimeware: Indicator is associated with a known actor suspected to be engaging in criminal activity. | -| **Vulnerability** | The CVE-XXXX-XXX vulnerability the indicator is associated with (e.g., [CVE-2012-0158](https://intelapi.crowdstrike.com/indicator/v1/search/labels?equal=vulnerability/CVE-2012-0158)). | - - -## Viewing Threat Intel Quick Analysis Dashboards - -All Dashboards include filters that you can use in Interactive Mode for further analysis of your Threat Intel Quick Analysis data. Because the Threat Intel Quick Analysis has the most bearing on recent threats, most panels are set to the 15 minute time range. You can adjust time ranges as needed. +All dashboards include filters that you can use in Interactive Mode for further analysis of your Threat Intel Quick Analysis data. Because the Threat Intel Quick Analysis has the most bearing on recent threats, most panels are set to the 15 minute time range. You can adjust time ranges as needed. Live mode and real-time queries are not supported for dashboards at this time. @@ -452,15 +239,14 @@ See the frequency of Domain threats by Actor, Log Source, Malicious Confidence,
}) -* **Welcome to the Threat Intel Quick Analysis App.** Informational panel to help you find information on [optimization](#threat-intel-optimization) and [FAQs](#threat-intel-faq) on working with the Threat Intel database.
+* **Welcome to the Threat Intel Quick Analysis App.** Informational panel to help you find information on working with the threat intelligence database.
* **Number of Log Lines (Events) Scanned for Threats.** Count of log lines scanned across all selected sources for the last 15 minutes.
* **IP Threat Count.** Count of threats related to malicious IPs, for the last 15 minutes.
* **File Name Threat Count.** Count of threats related to malicious file names, for the last 15 minutes.
* **URL Threat Count.** Count of threats related to malicious URLs, for the last 15 minutes.
* **Email Threat Count.** Count of threats related to malicious email addresses, for the last 15 minutes.
* **Domain Threat Count.** Count of threats related to malicious domains, for the last 15 minutes.
-* **Threats by Malicious Confidence.** Qualifies all threats into High, Medium, Low, Unverified, according to CrowdStrike's machine learning engine.
-
+* **Threats by Malicious Confidence.** Qualifies all threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
### Domain
@@ -469,8 +255,8 @@ See the frequency of Domain threats by Actor, Log Source, Malicious Confidence,
-* **Welcome to the Threat Intel Quick Analysis App.** Informational panel to help you find information on [optimization](#threat-intel-optimization) and [FAQs](#threat-intel-faq) on working with the Threat Intel database.
+* **Welcome to the Threat Intel Quick Analysis App.** Informational panel to help you find information on working with the threat intelligence database.
* **Number of Log Lines (Events) Scanned for Threats.** Count of log lines scanned across all selected sources for the last 15 minutes.
* **IP Threat Count.** Count of threats related to malicious IPs, for the last 15 minutes.
* **File Name Threat Count.** Count of threats related to malicious file names, for the last 15 minutes.
* **URL Threat Count.** Count of threats related to malicious URLs, for the last 15 minutes.
* **Email Threat Count.** Count of threats related to malicious email addresses, for the last 15 minutes.
* **Domain Threat Count.** Count of threats related to malicious domains, for the last 15 minutes.
-* **Threats by Malicious Confidence.** Qualifies all threats into High, Medium, Low, Unverified, according to CrowdStrike's machine learning engine.
-
+* **Threats by Malicious Confidence.** Qualifies all threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
### Domain
@@ -469,8 +255,8 @@ See the frequency of Domain threats by Actor, Log Source, Malicious Confidence,
}) * **Threat Count.** Count of threats related to malicious domains, for the last 15 minutes.
-* **Threats by Malicious Confidence.** Qualifies domain threats into High, Medium, Low, Unverified, according to CrowdStrike's machine learning engine.
-* **Threats by Actor.** Count of threats related to malicious domains, broken by Actors, for the last 15 minutes. [Actors](https://www.crowdstrike.com/blog/meet-the-adversaries/) are identified individuals, groups or nation-states associated to threats.
+* **Threats by Malicious Confidence.** Qualifies domain threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
+* **Threats by Actor.** Count of threats related to malicious domains, broken down by Actors, for the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
* **Threats by Sources.** Count of threats related to malicious domains, broken by Sources, for the last 15 minutes.
* **Threats Over Time.** Trends of domain threats over time for the last 60 minutes.
* **Threats Over Time by Sources.** Trends of domain threats over time, broken by Sources for the last 60 minutes.
@@ -483,14 +269,13 @@ See the frequency of Email threats by Actor, Log Source, Malicious Confidence, a
* **Threat Count.** Count of threats related to malicious domains, for the last 15 minutes.
-* **Threats by Malicious Confidence.** Qualifies domain threats into High, Medium, Low, Unverified, according to CrowdStrike's machine learning engine.
-* **Threats by Actor.** Count of threats related to malicious domains, broken by Actors, for the last 15 minutes. [Actors](https://www.crowdstrike.com/blog/meet-the-adversaries/) are identified individuals, groups or nation-states associated to threats.
+* **Threats by Malicious Confidence.** Qualifies domain threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
+* **Threats by Actor.** Count of threats related to malicious domains, broken down by Actors, for the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
* **Threats by Sources.** Count of threats related to malicious domains, broken by Sources, for the last 15 minutes.
* **Threats Over Time.** Trends of domain threats over time for the last 60 minutes.
* **Threats Over Time by Sources.** Trends of domain threats over time, broken by Sources for the last 60 minutes.
@@ -483,14 +269,13 @@ See the frequency of Email threats by Actor, Log Source, Malicious Confidence, a
}) * **Threat Count.** Count of threats related to malicious emails addresses, for the last 15 minutes.
-* **Threats by Malicious Confidence.** Qualifies email address threats into High, Medium, Low, Unverified, according to CrowdStrike's machine learning engine.
+* **Threats by Malicious Confidence.** Qualifies email address threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
* **Threat Breakdown by Sources.** Count of threats related to malicious email addresses, broken by Sources, for the last 15 minutes.
* **Threats Over Time.** Trends of email address threats over time for the last 60 minutes.
* **Threats Over Time by Sources.** Trends of email address threats over time, broken by Sources for the last 60 minutes.
-* **Threats by Actor.** Count of threats related to malicious email addresses, broken by Actors, for the last 15 minutes. [Actors](https://www.crowdstrike.com/blog/meet-the-adversaries/) are identified individuals, groups or nation-states associated to threats.
+* **Threats by Actor.** Count of threats related to malicious email addresses, broken by Actors, for the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
* **Threats Table.** Listing of all domain threats, including Malicious Confidence, Actors and Sources.
-
### IP
See the frequency of IP threats by Actor, Log Source, Malicious Confidence, and view trends over time.
@@ -500,13 +285,12 @@ See the frequency of IP threats by Actor, Log Source, Malicious Confidence, and
* **Threat Count.** Count of threats related to malicious IPs, for the last 15 minutes.
* **Threats by Geo Location.** Count of threats related to malicious IPs, broken by geo location, for the last 15 minutes.
* **Threat Breakdown by Sources.** Count of threats related to malicious IPs, broken by Sources, for the last 15 minutes.
-* **Threats by Malicious Confidence.** Qualifies IP threats into High, Medium, Low, Unverified, according to CrowdStrike's machine learning engine.
-* **Threats by Actors.** Count of threats related to malicious IPs, broken by Actors, for the last 15 minutes. [Actors](https://www.crowdstrike.com/blog/meet-the-adversaries/) are identified individuals, groups or nation-states associated to threats.
+* **Threats by Malicious Confidence.** Qualifies IP threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
+* **Threats by Actors.** Count of threats related to malicious IPs, broken by Actors, for the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
* **Threats Over Time.** Trends of IP threats over time for the last 60 minutes.
* **Threats Table.** Listing of all IP threats, including Malicious Confidence, Actors and Sources.
* **Threats Over Time by Sources.** Trends of IP threats over time, broken by Sources for the last 60 minutes.
-
### URL
See the frequency of URL threats by Actor, Log Source, Malicious Confidence, and view trends over time.
@@ -515,23 +299,22 @@ See the frequency of URL threats by Actor, Log Source, Malicious Confidence, and
* **Threat Count.** Count of threats related to malicious URLs, for the last 15 minutes.
* **Threats by Sources.** Count of threats related to malicious URLs, broken by Sources, for the last 15 minutes.
-* **Threats by Actors.** Count of threats related to malicious URLs, broken by Actors, for the last 15 minutes. [Actors](https://www.crowdstrike.com/blog/meet-the-adversaries/) are identified individuals, groups or nation-states associated to threats.
-* **Threats by Malicious Confidence.** Qualifies URLP threats into High, Medium, Low, Unverified, according to CrowdStrike's machine learning engine.
+* **Threats by Actors.** Count of threats related to malicious URLs, broken by Actors, for the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
+* **Threats by Malicious Confidence.** Qualifies URLP threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
* **Threats Over Time.** Trends of URL threats over time for the last 60 minutes.
* **Threats Over Time by Sources.** Trends of URL threats over time, broken by Sources for the last 60 minutes.
* **Threat Table.** Listing of threats identified by URL, including information on Malicious Confidence, Actors, Source, and count.
-
### Hash 256
-See the frequency of Hash 256 threats by Actor, Log Source, Malicious Confidence, and view trends over time.
+See the frequency of SHA-256 threats by Actor, Log Source, Malicious Confidence, and view trends over time.
* **Threat Count.** Count of threats related to malicious emails addresses, for the last 15 minutes.
-* **Threats by Malicious Confidence.** Qualifies email address threats into High, Medium, Low, Unverified, according to CrowdStrike's machine learning engine.
+* **Threats by Malicious Confidence.** Qualifies email address threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
* **Threat Breakdown by Sources.** Count of threats related to malicious email addresses, broken by Sources, for the last 15 minutes.
* **Threats Over Time.** Trends of email address threats over time for the last 60 minutes.
* **Threats Over Time by Sources.** Trends of email address threats over time, broken by Sources for the last 60 minutes.
-* **Threats by Actor.** Count of threats related to malicious email addresses, broken by Actors, for the last 15 minutes. [Actors](https://www.crowdstrike.com/blog/meet-the-adversaries/) are identified individuals, groups or nation-states associated to threats.
+* **Threats by Actor.** Count of threats related to malicious email addresses, broken by Actors, for the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
* **Threats Table.** Listing of all domain threats, including Malicious Confidence, Actors and Sources.
-
### IP
See the frequency of IP threats by Actor, Log Source, Malicious Confidence, and view trends over time.
@@ -500,13 +285,12 @@ See the frequency of IP threats by Actor, Log Source, Malicious Confidence, and
* **Threat Count.** Count of threats related to malicious IPs, for the last 15 minutes.
* **Threats by Geo Location.** Count of threats related to malicious IPs, broken by geo location, for the last 15 minutes.
* **Threat Breakdown by Sources.** Count of threats related to malicious IPs, broken by Sources, for the last 15 minutes.
-* **Threats by Malicious Confidence.** Qualifies IP threats into High, Medium, Low, Unverified, according to CrowdStrike's machine learning engine.
-* **Threats by Actors.** Count of threats related to malicious IPs, broken by Actors, for the last 15 minutes. [Actors](https://www.crowdstrike.com/blog/meet-the-adversaries/) are identified individuals, groups or nation-states associated to threats.
+* **Threats by Malicious Confidence.** Qualifies IP threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
+* **Threats by Actors.** Count of threats related to malicious IPs, broken by Actors, for the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
* **Threats Over Time.** Trends of IP threats over time for the last 60 minutes.
* **Threats Table.** Listing of all IP threats, including Malicious Confidence, Actors and Sources.
* **Threats Over Time by Sources.** Trends of IP threats over time, broken by Sources for the last 60 minutes.
-
### URL
See the frequency of URL threats by Actor, Log Source, Malicious Confidence, and view trends over time.
@@ -515,23 +299,22 @@ See the frequency of URL threats by Actor, Log Source, Malicious Confidence, and
* **Threat Count.** Count of threats related to malicious URLs, for the last 15 minutes.
* **Threats by Sources.** Count of threats related to malicious URLs, broken by Sources, for the last 15 minutes.
-* **Threats by Actors.** Count of threats related to malicious URLs, broken by Actors, for the last 15 minutes. [Actors](https://www.crowdstrike.com/blog/meet-the-adversaries/) are identified individuals, groups or nation-states associated to threats.
-* **Threats by Malicious Confidence.** Qualifies URLP threats into High, Medium, Low, Unverified, according to CrowdStrike's machine learning engine.
+* **Threats by Actors.** Count of threats related to malicious URLs, broken by Actors, for the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
+* **Threats by Malicious Confidence.** Qualifies URLP threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
* **Threats Over Time.** Trends of URL threats over time for the last 60 minutes.
* **Threats Over Time by Sources.** Trends of URL threats over time, broken by Sources for the last 60 minutes.
* **Threat Table.** Listing of threats identified by URL, including information on Malicious Confidence, Actors, Source, and count.
-
### Hash 256
-See the frequency of Hash 256 threats by Actor, Log Source, Malicious Confidence, and view trends over time.
+See the frequency of SHA-256 threats by Actor, Log Source, Malicious Confidence, and view trends over time.
}) -* **Threat Count.** Count of total Hash 256 threats over the last 15 minutes.
-* **Threats by Malicious Confidence.** Qualifies Hash 256 threats for the last 60 minutes into High, Medium, Low, Unverified, according to CrowdStrike's machine learning engine and displayed as a pie chart.
-* **Threat Breakdown by Sources.** Pie chart of Hash 256 threats over the last 60 minutes broken down by source.
-* **Threats Over Time.** Line chart of the number of Hash 256 threats over the last 60 minutes.
-* **Threat Breakdown by Source.** Line chart of the number of Hash 256 threats over the last 60 minutes, broken down by source.
-* **Threats by Actor.** Identifies Actors, if any, that can be attributed to Hash 256 threats over the last 15 minutes. [Actors](https://www.crowdstrike.com/blog/meet-the-adversaries/) are identified individuals, groups or nation-states associated to threats.
-* **Threat Table.** Aggregation Table of Hash 256 threats over the last 15 minutes.
+* **Threat Count.** Count of total SHA-256 threats over the last 15 minutes.
+* **Threats by Malicious Confidence.** Qualifies SHA-256 threats for the last 60 minutes into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine and displayed as a pie chart.
+* **Threat Breakdown by Sources.** Pie chart of SHA-256 threats over the last 60 minutes broken down by source.
+* **Threats Over Time.** Line chart of the number of SHA-256 threats over the last 60 minutes.
+* **Threat Breakdown by Source.** Line chart of the number of SHA-256 threats over the last 60 minutes, broken down by source.
+* **Threats by Actor.** Identifies Actors, if any, that can be attributed to SHA-256 threats over the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
+* **Threat Table.** Aggregation Table of SHA-256 threats over the last 15 minutes.
diff --git a/docs/integrations/web-servers/apache-tomcat.md b/docs/integrations/web-servers/apache-tomcat.md
index 3e2ad004b5..8bc9ae38a5 100644
--- a/docs/integrations/web-servers/apache-tomcat.md
+++ b/docs/integrations/web-servers/apache-tomcat.md
@@ -692,7 +692,7 @@ The **Apache Tomcat - Garbage Collector** dashboard provides information on the
The **Apache Tomcat - Threat Intel** dashboard provides an at-a-glance view of threats to Apache Tomcat servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats.
Use this dashboard to:
-* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
-* **Threat Count.** Count of total Hash 256 threats over the last 15 minutes.
-* **Threats by Malicious Confidence.** Qualifies Hash 256 threats for the last 60 minutes into High, Medium, Low, Unverified, according to CrowdStrike's machine learning engine and displayed as a pie chart.
-* **Threat Breakdown by Sources.** Pie chart of Hash 256 threats over the last 60 minutes broken down by source.
-* **Threats Over Time.** Line chart of the number of Hash 256 threats over the last 60 minutes.
-* **Threat Breakdown by Source.** Line chart of the number of Hash 256 threats over the last 60 minutes, broken down by source.
-* **Threats by Actor.** Identifies Actors, if any, that can be attributed to Hash 256 threats over the last 15 minutes. [Actors](https://www.crowdstrike.com/blog/meet-the-adversaries/) are identified individuals, groups or nation-states associated to threats.
-* **Threat Table.** Aggregation Table of Hash 256 threats over the last 15 minutes.
+* **Threat Count.** Count of total SHA-256 threats over the last 15 minutes.
+* **Threats by Malicious Confidence.** Qualifies SHA-256 threats for the last 60 minutes into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine and displayed as a pie chart.
+* **Threat Breakdown by Sources.** Pie chart of SHA-256 threats over the last 60 minutes broken down by source.
+* **Threats Over Time.** Line chart of the number of SHA-256 threats over the last 60 minutes.
+* **Threat Breakdown by Source.** Line chart of the number of SHA-256 threats over the last 60 minutes, broken down by source.
+* **Threats by Actor.** Identifies Actors, if any, that can be attributed to SHA-256 threats over the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
+* **Threat Table.** Aggregation Table of SHA-256 threats over the last 15 minutes.
diff --git a/docs/integrations/web-servers/apache-tomcat.md b/docs/integrations/web-servers/apache-tomcat.md
index 3e2ad004b5..8bc9ae38a5 100644
--- a/docs/integrations/web-servers/apache-tomcat.md
+++ b/docs/integrations/web-servers/apache-tomcat.md
@@ -692,7 +692,7 @@ The **Apache Tomcat - Garbage Collector** dashboard provides information on the
The **Apache Tomcat - Threat Intel** dashboard provides an at-a-glance view of threats to Apache Tomcat servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats.
Use this dashboard to:
-* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
}) diff --git a/docs/integrations/web-servers/haproxy.md b/docs/integrations/web-servers/haproxy.md
index 74d85a78cf..520085a83e 100644
--- a/docs/integrations/web-servers/haproxy.md
+++ b/docs/integrations/web-servers/haproxy.md
@@ -456,7 +456,7 @@ Use this dashboard to:
The **HAProxy - Threat Inte**l dashboard provides an at-a-glance view of threats to HAProxy servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats.
Use this dashboard to:
-* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
diff --git a/docs/integrations/web-servers/haproxy.md b/docs/integrations/web-servers/haproxy.md
index 74d85a78cf..520085a83e 100644
--- a/docs/integrations/web-servers/haproxy.md
+++ b/docs/integrations/web-servers/haproxy.md
@@ -456,7 +456,7 @@ Use this dashboard to:
The **HAProxy - Threat Inte**l dashboard provides an at-a-glance view of threats to HAProxy servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats.
Use this dashboard to:
-* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
}) diff --git a/docs/integrations/web-servers/nginx-ingress.md b/docs/integrations/web-servers/nginx-ingress.md
index cf80660cf8..007c7a9477 100644
--- a/docs/integrations/web-servers/nginx-ingress.md
+++ b/docs/integrations/web-servers/nginx-ingress.md
@@ -156,7 +156,7 @@ You can use schedule searches to send alerts to yourself whenever there is an ou
The **Nginx Ingress - Threat Intel** dashboard provides an at-a-glance view of threats to Nginx servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats.
Use this dashboard to:
-* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
diff --git a/docs/integrations/web-servers/nginx-ingress.md b/docs/integrations/web-servers/nginx-ingress.md
index cf80660cf8..007c7a9477 100644
--- a/docs/integrations/web-servers/nginx-ingress.md
+++ b/docs/integrations/web-servers/nginx-ingress.md
@@ -156,7 +156,7 @@ You can use schedule searches to send alerts to yourself whenever there is an ou
The **Nginx Ingress - Threat Intel** dashboard provides an at-a-glance view of threats to Nginx servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats.
Use this dashboard to:
-* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
}) diff --git a/docs/integrations/web-servers/nginx-plus-ingress.md b/docs/integrations/web-servers/nginx-plus-ingress.md
index c9eead2d02..5df3dae669 100644
--- a/docs/integrations/web-servers/nginx-plus-ingress.md
+++ b/docs/integrations/web-servers/nginx-plus-ingress.md
@@ -176,7 +176,7 @@ You can use schedule searches to send alerts to yourself whenever there is an ou
The **Nginx Plus Ingress - Threat Inte**l dashboard provides an at-a-glance view of threats to Nginx servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats.
Use this dashboard to:
-* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the[ Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using theSumo Logic [threat intelligence](/docs/security/threat-intelligence/).
diff --git a/docs/integrations/web-servers/nginx-plus-ingress.md b/docs/integrations/web-servers/nginx-plus-ingress.md
index c9eead2d02..5df3dae669 100644
--- a/docs/integrations/web-servers/nginx-plus-ingress.md
+++ b/docs/integrations/web-servers/nginx-plus-ingress.md
@@ -176,7 +176,7 @@ You can use schedule searches to send alerts to yourself whenever there is an ou
The **Nginx Plus Ingress - Threat Inte**l dashboard provides an at-a-glance view of threats to Nginx servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats.
Use this dashboard to:
-* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the[ Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using theSumo Logic [threat intelligence](/docs/security/threat-intelligence/).
}) diff --git a/docs/integrations/web-servers/nginx-plus.md b/docs/integrations/web-servers/nginx-plus.md
index c6b62b7e31..7f9de9b775 100644
--- a/docs/integrations/web-servers/nginx-plus.md
+++ b/docs/integrations/web-servers/nginx-plus.md
@@ -358,7 +358,7 @@ You can use schedule searches to send alerts to yourself whenever there is an ou
The **Nginx Plus - Threat Inte**l dashboard provides an at-a-glance view of threats to Nginx servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats.
Use this dashboard to:
-* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the[ Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
diff --git a/docs/integrations/web-servers/nginx-plus.md b/docs/integrations/web-servers/nginx-plus.md
index c6b62b7e31..7f9de9b775 100644
--- a/docs/integrations/web-servers/nginx-plus.md
+++ b/docs/integrations/web-servers/nginx-plus.md
@@ -358,7 +358,7 @@ You can use schedule searches to send alerts to yourself whenever there is an ou
The **Nginx Plus - Threat Inte**l dashboard provides an at-a-glance view of threats to Nginx servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats.
Use this dashboard to:
-* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the[ Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
}) diff --git a/docs/integrations/web-servers/nginx.md b/docs/integrations/web-servers/nginx.md
index 0c4f07ef6e..a5500910ad 100644
--- a/docs/integrations/web-servers/nginx.md
+++ b/docs/integrations/web-servers/nginx.md
@@ -420,7 +420,7 @@ You can use schedule searches to send alerts to yourself whenever there is an ou
The **Nginx - Threat Intel** dashboard provides an at-a-glance view of threats to Nginx servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats.
Use this dashboard to:
-* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
diff --git a/docs/integrations/web-servers/nginx.md b/docs/integrations/web-servers/nginx.md
index 0c4f07ef6e..a5500910ad 100644
--- a/docs/integrations/web-servers/nginx.md
+++ b/docs/integrations/web-servers/nginx.md
@@ -420,7 +420,7 @@ You can use schedule searches to send alerts to yourself whenever there is an ou
The **Nginx - Threat Intel** dashboard provides an at-a-glance view of threats to Nginx servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats.
Use this dashboard to:
-* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
}) diff --git a/docs/integrations/web-servers/opentelemetry/apache-tomcat-opentelemetry.md b/docs/integrations/web-servers/opentelemetry/apache-tomcat-opentelemetry.md
index f47c32e5a0..d207108ed2 100644
--- a/docs/integrations/web-servers/opentelemetry/apache-tomcat-opentelemetry.md
+++ b/docs/integrations/web-servers/opentelemetry/apache-tomcat-opentelemetry.md
@@ -373,7 +373,7 @@ The **Apache Tomcat - Threat Intel** dashboard provides an at-a-glance view of t
Use this dashboard to:
-- To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo Logic - CrowdStrike](/docs/integrations/security-threat-detection/threat-intel-quick-analysis/#threat-intel-faq) threat feed.
+- To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
diff --git a/docs/integrations/web-servers/opentelemetry/apache-tomcat-opentelemetry.md b/docs/integrations/web-servers/opentelemetry/apache-tomcat-opentelemetry.md
index f47c32e5a0..d207108ed2 100644
--- a/docs/integrations/web-servers/opentelemetry/apache-tomcat-opentelemetry.md
+++ b/docs/integrations/web-servers/opentelemetry/apache-tomcat-opentelemetry.md
@@ -373,7 +373,7 @@ The **Apache Tomcat - Threat Intel** dashboard provides an at-a-glance view of t
Use this dashboard to:
-- To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo Logic - CrowdStrike](/docs/integrations/security-threat-detection/threat-intel-quick-analysis/#threat-intel-faq) threat feed.
+- To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
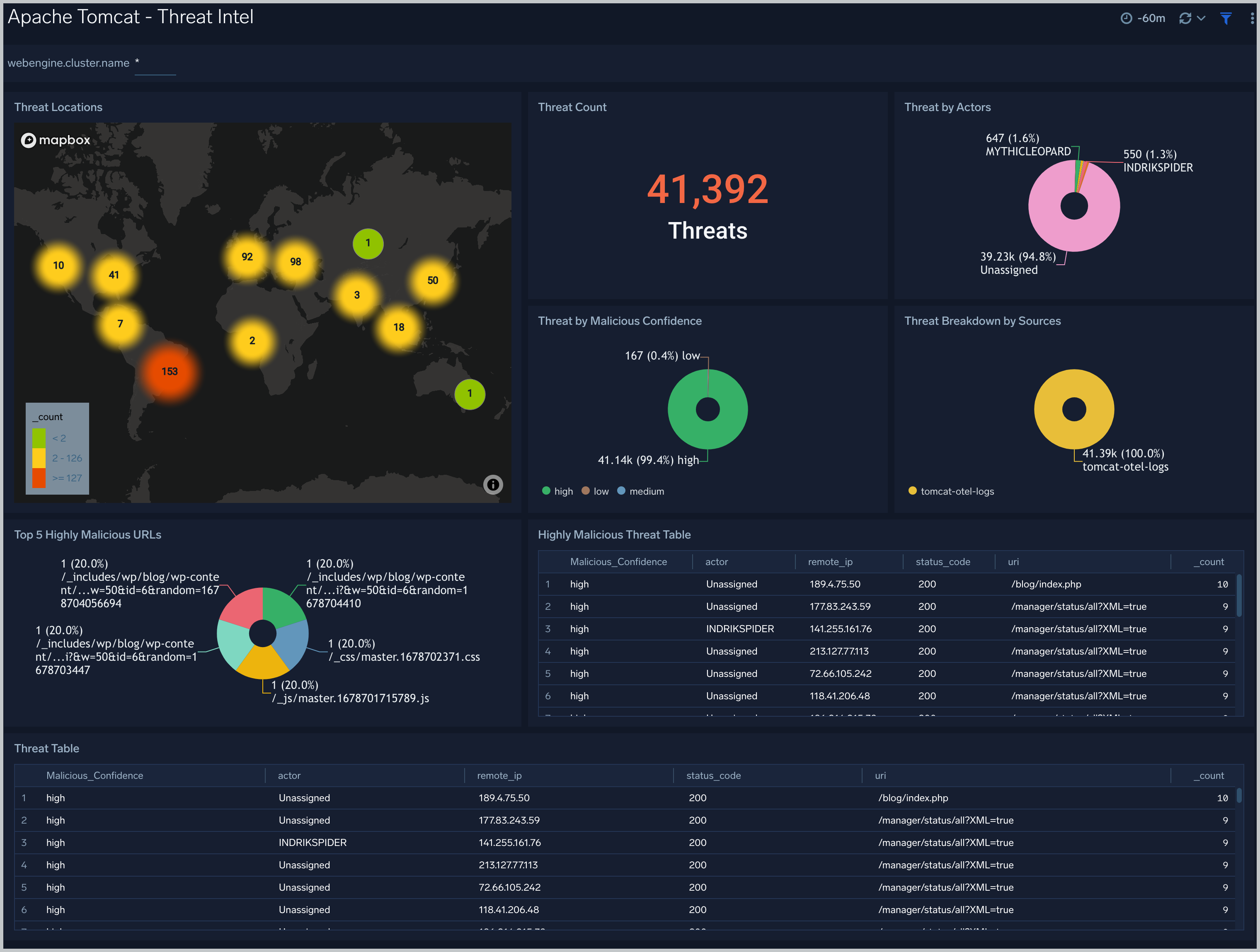 diff --git a/docs/integrations/web-servers/opentelemetry/haproxy-opentelemetry.md b/docs/integrations/web-servers/opentelemetry/haproxy-opentelemetry.md
index cba874ef1c..f4b273480e 100644
--- a/docs/integrations/web-servers/opentelemetry/haproxy-opentelemetry.md
+++ b/docs/integrations/web-servers/opentelemetry/haproxy-opentelemetry.md
@@ -302,7 +302,7 @@ The **HAProxy - Threat Analysis** dashboard provides an at-a-glance view of thre
Use this dashboard to:
-- To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis/#threat-intel-faq) threat feed.
+- To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
diff --git a/docs/integrations/web-servers/opentelemetry/haproxy-opentelemetry.md b/docs/integrations/web-servers/opentelemetry/haproxy-opentelemetry.md
index cba874ef1c..f4b273480e 100644
--- a/docs/integrations/web-servers/opentelemetry/haproxy-opentelemetry.md
+++ b/docs/integrations/web-servers/opentelemetry/haproxy-opentelemetry.md
@@ -302,7 +302,7 @@ The **HAProxy - Threat Analysis** dashboard provides an at-a-glance view of thre
Use this dashboard to:
-- To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis/#threat-intel-faq) threat feed.
+- To gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
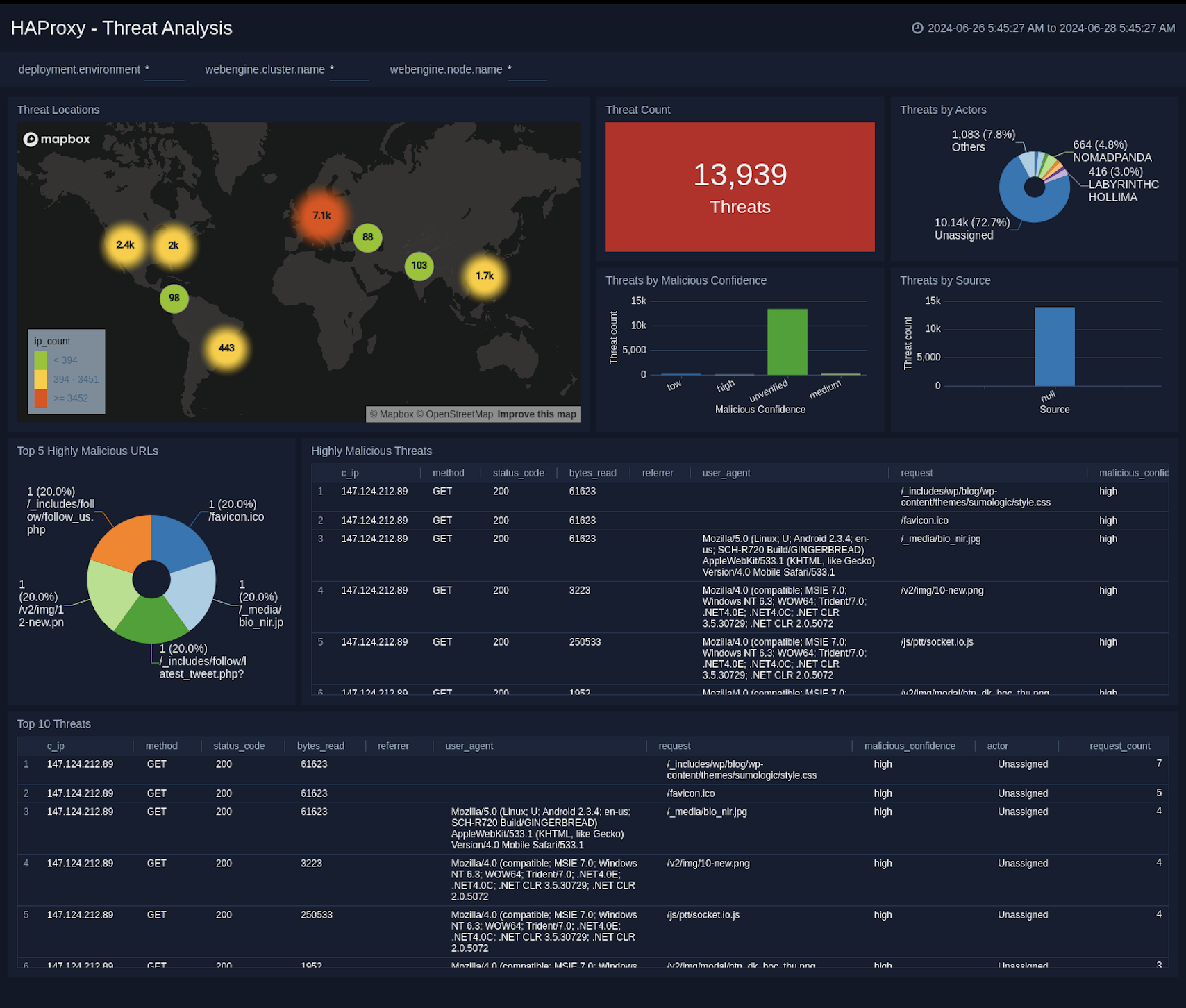 diff --git a/docs/integrations/web-servers/opentelemetry/nginx-opentelemetry.md b/docs/integrations/web-servers/opentelemetry/nginx-opentelemetry.md
index c8a141c10c..571a437c3b 100644
--- a/docs/integrations/web-servers/opentelemetry/nginx-opentelemetry.md
+++ b/docs/integrations/web-servers/opentelemetry/nginx-opentelemetry.md
@@ -238,7 +238,7 @@ You can use schedule searches to send alerts to yourself whenever there is an ou
### Threat Intel
-The **Nginx - Threat Intel** dashboard provides an at-a-glance view of threats to Nginx servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats. Use this dashboard to gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis/#threat-intel-faq) threat feed.
+The **Nginx - Threat Intel** dashboard provides an at-a-glance view of threats to Nginx servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats. Use this dashboard to gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
diff --git a/docs/integrations/web-servers/opentelemetry/nginx-opentelemetry.md b/docs/integrations/web-servers/opentelemetry/nginx-opentelemetry.md
index c8a141c10c..571a437c3b 100644
--- a/docs/integrations/web-servers/opentelemetry/nginx-opentelemetry.md
+++ b/docs/integrations/web-servers/opentelemetry/nginx-opentelemetry.md
@@ -238,7 +238,7 @@ You can use schedule searches to send alerts to yourself whenever there is an ou
### Threat Intel
-The **Nginx - Threat Intel** dashboard provides an at-a-glance view of threats to Nginx servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats. Use this dashboard to gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis/#threat-intel-faq) threat feed.
+The **Nginx - Threat Intel** dashboard provides an at-a-glance view of threats to Nginx servers on your network. Dashboard panels display the threat count over a selected time period, geographic locations where threats occurred, source breakdown, actors responsible for threats, severity, and a correlation of IP addresses, method, and status code of threats. Use this dashboard to gain insights and understand threats in incoming traffic and discover potential IOCs. Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
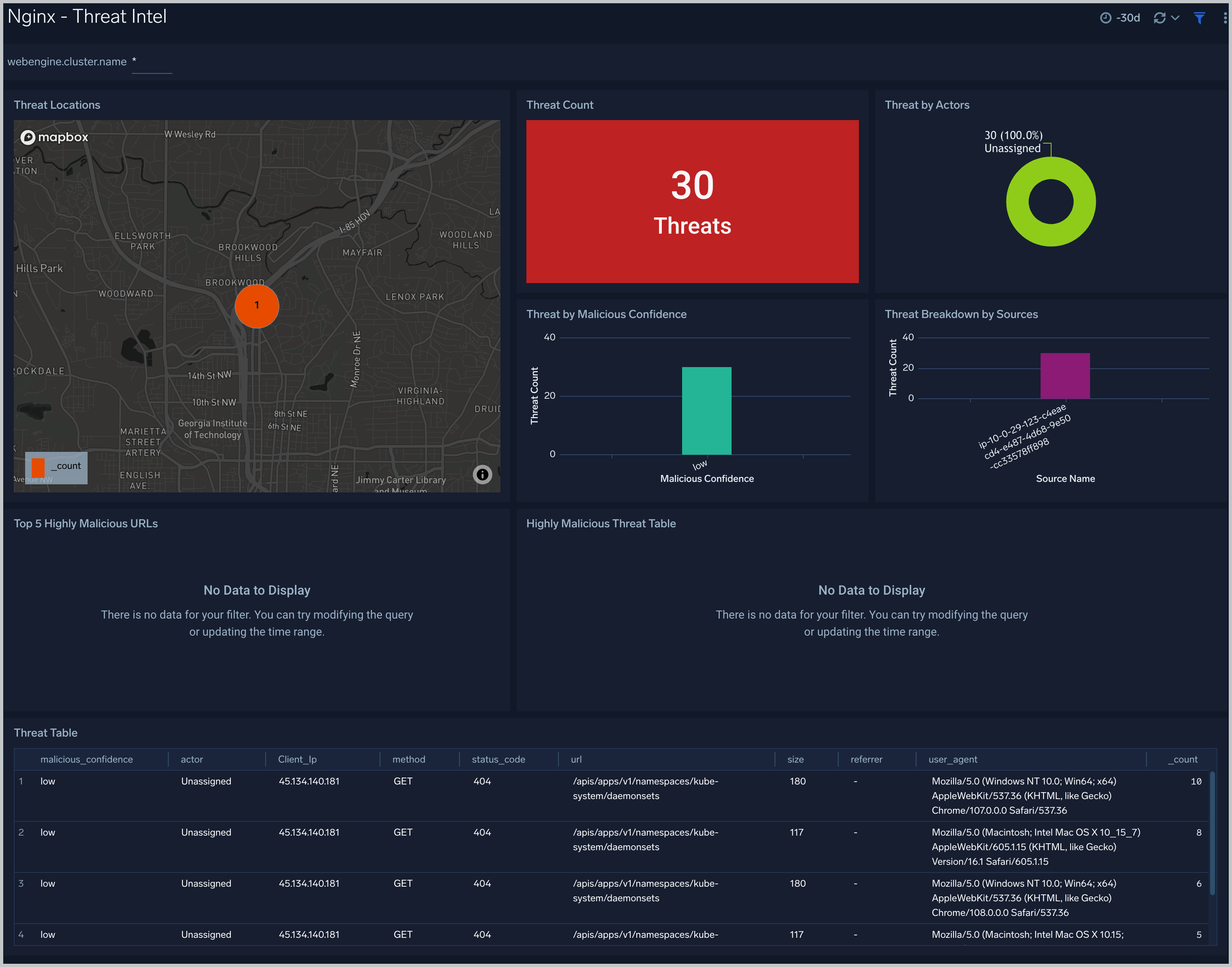 diff --git a/docs/integrations/web-servers/varnish.md b/docs/integrations/web-servers/varnish.md
index 35400aa597..83becc50a2 100644
--- a/docs/integrations/web-servers/varnish.md
+++ b/docs/integrations/web-servers/varnish.md
@@ -504,7 +504,7 @@ The **Varnish - Threat Intel** dashboard provides an at-a-glance view of threats
Use this dashboard to:
* To gain insights and understand threats in incoming traffic and discover potential IOCs.
-* Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
diff --git a/docs/integrations/web-servers/varnish.md b/docs/integrations/web-servers/varnish.md
index 35400aa597..83becc50a2 100644
--- a/docs/integrations/web-servers/varnish.md
+++ b/docs/integrations/web-servers/varnish.md
@@ -504,7 +504,7 @@ The **Varnish - Threat Intel** dashboard provides an at-a-glance view of threats
Use this dashboard to:
* To gain insights and understand threats in incoming traffic and discover potential IOCs.
-* Incoming traffic requests are analyzed using the [Sumo - Crowdstrikes](/docs/integrations/security-threat-detection/threat-intel-quick-analysis#threat-intel-faq) threat feed.
+* Incoming traffic requests are analyzed using Sumo Logic [threat intelligence](/docs/security/threat-intelligence/).
}) diff --git a/docs/manage/manage-subscription/sumo-logic-credits-accounts.md b/docs/manage/manage-subscription/sumo-logic-credits-accounts.md
index e734aff849..f1d9d8ccf3 100644
--- a/docs/manage/manage-subscription/sumo-logic-credits-accounts.md
+++ b/docs/manage/manage-subscription/sumo-logic-credits-accounts.md
@@ -86,7 +86,7 @@ The following table provides a summary list of key features by Credits package a
| Audit Event Index | |  | |  |  |  |
| Cloud SIEM | | | | | Activation required* | Activation required* |
| Cloud SOAR | | | | | | Activation required* |
-| CrowdStrike Threat Intel | |  |  |  |  |  |
+| Threat Intel | |  |  |  |  |  |
| Collector Management API |  |  |  |  |  |  |
| Data Forwarding | |  |  |  |  |  |
| Data Tiers | | | | | |  |
diff --git a/docs/manage/manage-subscription/sumo-logic-flex-accounts.md b/docs/manage/manage-subscription/sumo-logic-flex-accounts.md
index 4cd824860b..01fadd6e01 100644
--- a/docs/manage/manage-subscription/sumo-logic-flex-accounts.md
+++ b/docs/manage/manage-subscription/sumo-logic-flex-accounts.md
@@ -74,7 +74,7 @@ The following table provides a summary list of key features by Flex package acco
| Cloud SOAR | | | | Activation required* |
| Collector Management API |  |  |  | |
| Compliance and Audit Logging | |  | |  |
-| CrowdStrike Threat Intelligence | |  | |  |
+| Threat Intelligence | |  | |  |
| Customizable Dashboards |  |  | |  |
| Data Forwarding | |  |  | |
| Data Volume Index | |  |  | |
diff --git a/docs/manage/security/audit-indexes/audit-event-index.md b/docs/manage/security/audit-indexes/audit-event-index.md
index aa335d1764..ecfd7df565 100644
--- a/docs/manage/security/audit-indexes/audit-event-index.md
+++ b/docs/manage/security/audit-indexes/audit-event-index.md
@@ -66,6 +66,8 @@ _index=sumologic_audit_events _sourceCategory=accessKeys
| Security Policy: [Support Account Access](/docs/manage/security/enable-support-account) | `supportAccount` |
| [Service Allowlist](/docs/manage/security/create-allowlist-ip-cidr-addresses) | `serviceAllowlist` |
| [Support Account](/docs/manage/security/enable-support-account) | `supportAccount` |
+| [Threat Intelligence](/docs/security/threat-intelligence/) | `threatIntelligence` |
+| [Tracing Ingest](/docs/apm/traces/tracing-ingest) | `tracingIngest` |
| [Transformation Rules](/docs/metrics/metrics-transformation-rules) | `transformationRules` |
| [Users](/docs/manage/users-roles) | `users` |
| User Sessions | `userSessions` |
diff --git a/docs/manage/users-roles/roles/role-capabilities.md b/docs/manage/users-roles/roles/role-capabilities.md
index a3a31bf0d1..ea0708d55c 100644
--- a/docs/manage/users-roles/roles/role-capabilities.md
+++ b/docs/manage/users-roles/roles/role-capabilities.md
@@ -127,11 +127,10 @@ Folder-level permissions are available if your org has fine-grained Monitor perm
| Deactivate Organizations | Deactivate trial organizations. (For Sumo Logic Service Providers only.)|
## Threat Intel
-
| Capability | Description |
| :-- | :-- |
-| View Threat Intel Data Store | Search log data using threat intelligence indicators. |
-| Manage Threat Intel Data Store | Create, edit, and delete threat intelligence indicators. |
+| View Threat Intel Data Store | Search log data using [threat intelligence indicators](/docs/security/threat-intelligence/threat-intelligence-indicators/). |
+| Manage Threat Intel Data Store | Create, edit, and delete [threat intelligence indicators](/docs/security/threat-intelligence/threat-intelligence-indicators/). |
## Cloud SOAR
diff --git a/docs/observability/aws/integrations/aws-dynamodb.md b/docs/observability/aws/integrations/aws-dynamodb.md
index d98f78d310..43503d55a6 100644
--- a/docs/observability/aws/integrations/aws-dynamodb.md
+++ b/docs/observability/aws/integrations/aws-dynamodb.md
@@ -69,6 +69,20 @@ _sourceCategory=Labs/AWS/DynamoDB account=* namespace=* "\"eventSource\":\"dynam
| sum (ip_count) as threat_count
```
+
+
## Viewing AWS DynamoDB dashboards
We highly recommend you view these dashboards in the [AWS Observability view](/docs/dashboards/explore-view/#aws-observability) of our AWS Observability solution.
diff --git a/docs/platform-services/automation-service/app-central/integrations/zerofox.md b/docs/platform-services/automation-service/app-central/integrations/zerofox.md
index e6c54c9f32..6351bfa8c9 100644
--- a/docs/platform-services/automation-service/app-central/integrations/zerofox.md
+++ b/docs/platform-services/automation-service/app-central/integrations/zerofox.md
@@ -1,5 +1,5 @@
---
-title: ZeroFOX
+title: ZeroFox
description: ''
---
import useBaseUrl from '@docusaurus/useBaseUrl';
@@ -9,7 +9,7 @@ import useBaseUrl from '@docusaurus/useBaseUrl';
***Version: 1.1
Updated: Jul 11, 2023***
-Query data and utilize action in ZeroFOX Platform.
+Query data and utilize action in ZeroFox Platform.
## Actions
diff --git a/docs/platform-services/index.md b/docs/platform-services/index.md
index 4397b71264..2d5d453212 100644
--- a/docs/platform-services/index.md
+++ b/docs/platform-services/index.md
@@ -15,4 +15,10 @@ Platform services are services that are available to use across the entire Sumo
diff --git a/docs/manage/manage-subscription/sumo-logic-credits-accounts.md b/docs/manage/manage-subscription/sumo-logic-credits-accounts.md
index e734aff849..f1d9d8ccf3 100644
--- a/docs/manage/manage-subscription/sumo-logic-credits-accounts.md
+++ b/docs/manage/manage-subscription/sumo-logic-credits-accounts.md
@@ -86,7 +86,7 @@ The following table provides a summary list of key features by Credits package a
| Audit Event Index | |  | |  |  |  |
| Cloud SIEM | | | | | Activation required* | Activation required* |
| Cloud SOAR | | | | | | Activation required* |
-| CrowdStrike Threat Intel | |  |  |  |  |  |
+| Threat Intel | |  |  |  |  |  |
| Collector Management API |  |  |  |  |  |  |
| Data Forwarding | |  |  |  |  |  |
| Data Tiers | | | | | |  |
diff --git a/docs/manage/manage-subscription/sumo-logic-flex-accounts.md b/docs/manage/manage-subscription/sumo-logic-flex-accounts.md
index 4cd824860b..01fadd6e01 100644
--- a/docs/manage/manage-subscription/sumo-logic-flex-accounts.md
+++ b/docs/manage/manage-subscription/sumo-logic-flex-accounts.md
@@ -74,7 +74,7 @@ The following table provides a summary list of key features by Flex package acco
| Cloud SOAR | | | | Activation required* |
| Collector Management API |  |  |  | |
| Compliance and Audit Logging | |  | |  |
-| CrowdStrike Threat Intelligence | |  | |  |
+| Threat Intelligence | |  | |  |
| Customizable Dashboards |  |  | |  |
| Data Forwarding | |  |  | |
| Data Volume Index | |  |  | |
diff --git a/docs/manage/security/audit-indexes/audit-event-index.md b/docs/manage/security/audit-indexes/audit-event-index.md
index aa335d1764..ecfd7df565 100644
--- a/docs/manage/security/audit-indexes/audit-event-index.md
+++ b/docs/manage/security/audit-indexes/audit-event-index.md
@@ -66,6 +66,8 @@ _index=sumologic_audit_events _sourceCategory=accessKeys
| Security Policy: [Support Account Access](/docs/manage/security/enable-support-account) | `supportAccount` |
| [Service Allowlist](/docs/manage/security/create-allowlist-ip-cidr-addresses) | `serviceAllowlist` |
| [Support Account](/docs/manage/security/enable-support-account) | `supportAccount` |
+| [Threat Intelligence](/docs/security/threat-intelligence/) | `threatIntelligence` |
+| [Tracing Ingest](/docs/apm/traces/tracing-ingest) | `tracingIngest` |
| [Transformation Rules](/docs/metrics/metrics-transformation-rules) | `transformationRules` |
| [Users](/docs/manage/users-roles) | `users` |
| User Sessions | `userSessions` |
diff --git a/docs/manage/users-roles/roles/role-capabilities.md b/docs/manage/users-roles/roles/role-capabilities.md
index a3a31bf0d1..ea0708d55c 100644
--- a/docs/manage/users-roles/roles/role-capabilities.md
+++ b/docs/manage/users-roles/roles/role-capabilities.md
@@ -127,11 +127,10 @@ Folder-level permissions are available if your org has fine-grained Monitor perm
| Deactivate Organizations | Deactivate trial organizations. (For Sumo Logic Service Providers only.)|
## Threat Intel
-
| Capability | Description |
| :-- | :-- |
-| View Threat Intel Data Store | Search log data using threat intelligence indicators. |
-| Manage Threat Intel Data Store | Create, edit, and delete threat intelligence indicators. |
+| View Threat Intel Data Store | Search log data using [threat intelligence indicators](/docs/security/threat-intelligence/threat-intelligence-indicators/). |
+| Manage Threat Intel Data Store | Create, edit, and delete [threat intelligence indicators](/docs/security/threat-intelligence/threat-intelligence-indicators/). |
## Cloud SOAR
diff --git a/docs/observability/aws/integrations/aws-dynamodb.md b/docs/observability/aws/integrations/aws-dynamodb.md
index d98f78d310..43503d55a6 100644
--- a/docs/observability/aws/integrations/aws-dynamodb.md
+++ b/docs/observability/aws/integrations/aws-dynamodb.md
@@ -69,6 +69,20 @@ _sourceCategory=Labs/AWS/DynamoDB account=* namespace=* "\"eventSource\":\"dynam
| sum (ip_count) as threat_count
```
+
+
## Viewing AWS DynamoDB dashboards
We highly recommend you view these dashboards in the [AWS Observability view](/docs/dashboards/explore-view/#aws-observability) of our AWS Observability solution.
diff --git a/docs/platform-services/automation-service/app-central/integrations/zerofox.md b/docs/platform-services/automation-service/app-central/integrations/zerofox.md
index e6c54c9f32..6351bfa8c9 100644
--- a/docs/platform-services/automation-service/app-central/integrations/zerofox.md
+++ b/docs/platform-services/automation-service/app-central/integrations/zerofox.md
@@ -1,5 +1,5 @@
---
-title: ZeroFOX
+title: ZeroFox
description: ''
---
import useBaseUrl from '@docusaurus/useBaseUrl';
@@ -9,7 +9,7 @@ import useBaseUrl from '@docusaurus/useBaseUrl';
***Version: 1.1
Updated: Jul 11, 2023***
-Query data and utilize action in ZeroFOX Platform.
+Query data and utilize action in ZeroFox Platform.
## Actions
diff --git a/docs/platform-services/index.md b/docs/platform-services/index.md
index 4397b71264..2d5d453212 100644
--- a/docs/platform-services/index.md
+++ b/docs/platform-services/index.md
@@ -15,4 +15,10 @@ Platform services are services that are available to use across the entire Sumo
Learn how to use the Automation Service to automate actions.
+Threat Intelligence
+Learn about Sumo Logic's threat intelligence capabilities.
+threatip()
-The `threatip()` operator correlates CrowdStrike's threat intelligence data based on IP addresses from your log data, helping you detect threats in your environment.
+threatip
+Correlates CrowdStrike's threat intelligence data based on IP addresses from your log data, helping you detect threats in your environment.
timeslice()
@@ -462,4 +468,4 @@ In this section, we'll introduce the following concepts:The `where` operator allows you to filter results based on a boolean expression.
You can filter on the following indicator attributes: + * `actors` + * `confidence` + * `id` + * `indicator` + * `killChain` + * `source` + * `threatType` + * `type` + * `validFrom` + * `validUntil` + +### Response fields + +Query responses return the following fields: +* `confidence` +* `fields` +* `imported` +* `indicator` +* `valid_from` +* `valid_until` +* `source` +* `threat_type` +* `type` +* `updated` +* `num_match` (if `singleIndicator` is used) + +## Examples + +### Simple examples + +``` +_index=sec_record* +| threatlookup srcDevice_ip +| where _threatlookup.confidence > 50 +| timeslice 1h +| count by _timeslice +``` +``` +_index=sec_record* +| threatlookup singleIndicator srcDevice_ip +| where _threatlookup.confidence > 50 +| timeslice 1h +| count by _timeslice +``` +``` +_index=sec_record* +| threatlookup source="mysource" srcDevice_ip +| where _threatlookup.confidence > 50 +| timeslice 1h +| count by _timeslice +``` +``` +_index=sec_record* +| threatlookup dstDevice_ip, srcDevice_ip +| where _threatlookup.confidence > 50 +| timeslice 1h +| count by _timeslice +``` +``` +_index=sec_record* +| threatlookup source="mysource" dstDevice_ip, srcDevice_ip +| where _threatlookup.confidence > 50 +| timeslice 1h +| count by _timeslice +``` +``` +_index=sec_record* +| threatlookup source="mysource" include="active" dstDevice_ip, srcDevice_ip +| where _threatlookup.confidence > 50 +| timeslice 1h +| count by _timeslice +``` + +### Complex examples + +```sql title="Client IP threat info" +_sourceCategory=AWS/WAF {{client_ip}} +| parse "\"httpMethod\":\"*\"," as httpMethod,"\"httpVersion\":\"*\"," as httpVersion,"\"uri\":\"*\"," as uri, "{\"clientIp\":\"*\",\"country\":\"*\"" as clientIp,country, "\"action\":\"*\"" as action, "\"matchingNonTerminatingRules\":[*]" as matchingNonTerminatingRules, "\"rateBasedRuleList\":[*]" as rateBasedRuleList, "\"ruleGroupList\":[*]" as ruleGroupList, "\"httpSourceId\":\"*\"" as httpSourceId, "\"httpSourceName\":\"*\"" as httpSourceName, "\"terminatingRuleType\":\"*\"" as terminatingRuleType, "\"terminatingRuleId\":\"*\"" as terminatingRuleId, "\"webaclId\":\"*\"" as webaclId nodrop +| threatlookup singleIndicator clientip +| where (_threatlookup.type="ipv4-addr" or _threatlookup.type="ipv6-addr") and !isNull(_threatlookup.confidence) +``` + +```sql title="All IP threat count" +_sourceCategory=Labs/AWS/DynamoDB account=* namespace=* "\"eventSource\":\"dynamodb.amazonaws.com\"" +| json "eventName", "awsRegion", "requestParameters.tableName", "sourceIPAddress", "userIdentity.userName" as event_name, Region, entity, ip_address, user +| where Region matches "*" and tolowercase(entity) matches "*" +| where ip_address != "0.0.0.0" and ip_address != "127.0.0.1" +| count as ip_count by ip_address +| threatlookup singleIndicator ip_address +| where (_threatlookup.type="ipv4-addr" or _threatlookup.type="ipv6-addr") and !isNull(_threatlookup.confidence) +| if (isEmpty(_threatlookup.actors), "Unassigned", _threatlookup.actors) as Actor +| sum (ip_count) as threat_count +``` + +```sql title="Use threatlookup in a subquery" +_sourceCategory=weblogs +[subquery:_sourceCategory="Labs/SecDemo/guardduty" "EC2 Instance" "communicating on an unusual server port 22" +| json field=_raw "service.action.networkConnectionAction.remoteIpDetails" as remoteIpDetails +| json field=_raw "service.action.networkConnectionAction.connectionDirection" as connectionDirection +| where connectionDirection = "OUTBOUND" +| json field=remoteipdetails "ipAddressV4" as src_ip +| threatlookup singleIndicator threat| if (_threatlookup.confidence >= 85, "high", if (_threatlookup.confidence >= 50, "medium", if (_threatlookup.confidence >= 15, "low", if (_threatlookup.confidence >= 0, "unverified", "Unknown")))) as malicious_confidence +| where malicious_confidence = "high" +| compose src_ip] +``` + + + +## Format timestamp results + +Timestamps for the following response fields return results as an integer because they use Unix time (also known as *epoch time*): +* `_threatlookup.imported` +* `_threatlookup.valid_from` +* `_threatlookup.valid_until` +* `_threatlookup.updated` + +To convert the timestamp results to a readable output, you must format it in the search itself with [`formatDate`](/docs/search/search-query-language/search-operators/formatdate). For example: + +``` +_index=sec_record* +| threatlookup source="mysource" device_ip +| formatDate(_threatlookup.valid_until, "yyyy-MM-dd'T'HH:mm:ss.SSS'Z'") as valid_until +``` + + \ No newline at end of file diff --git a/docs/search/search-query-language/search-operators/tolowercase-touppercase.md b/docs/search/search-query-language/search-operators/tolowercase-touppercase.md index 71ad0497aa..c14f33fb6a 100644 --- a/docs/search/search-query-language/search-operators/tolowercase-touppercase.md +++ b/docs/search/search-query-language/search-operators/tolowercase-touppercase.md @@ -55,6 +55,17 @@ which provides results like: | lookup raw from sumo://threat/cs on threat = hash{code} ``` + + ### Using toUpperCase with the count operator This query also returns all matching `_sourceHost` values in upper case letters, using the count operator. diff --git a/docs/search/subqueries.md b/docs/search/subqueries.md index ebaec48b96..22bfbedbbb 100644 --- a/docs/search/subqueries.md +++ b/docs/search/subqueries.md @@ -376,7 +376,7 @@ _sourceCategory=search "error while retrying to deploy index" ### Check Malicious Activity with Subquery -The following search allows a security analyst how to track logs related to a malicious IP address that was flagged by Amazon GuardDuty and also by a CrowdStrike Threat feed. The subquery is returning the field `src_ip` with the IP addresses deemed as threats to the parent query, note that the keywords option was not used so the parent query will expect a field src_ip to exist. The results will include logs from the weblogs sourceCategory that have a `src_ip` value that was deemed a threat from the subquery. +The following search allows a security analyst to track logs related to a malicious IP address that was flagged by Amazon GuardDuty and also by a CrowdStrike Threat feed. The subquery is returning the field `src_ip` with the IP addresses deemed as threats to the parent query, note that the keywords option was not used so the parent query will expect a field src_ip to exist. The results will include logs from the weblogs sourceCategory that have a `src_ip` value that was deemed a threat from the subquery. ```sql _sourceCategory=weblogs @@ -389,6 +389,19 @@ _sourceCategory=weblogs | where threatlevel = "high" | compose src_ip] ``` + ### Reference data from child query using save and lookup diff --git a/docs/security/additional-security-features/threat-detection-and-investigation.md b/docs/security/additional-security-features/threat-detection-and-investigation.md index fbfd8790d7..bc8cc93d4a 100644 --- a/docs/security/additional-security-features/threat-detection-and-investigation.md +++ b/docs/security/additional-security-features/threat-detection-and-investigation.md @@ -13,7 +13,7 @@ To use Sumo Logic for threat detection and investigation, you can use [pre-built [Install](/docs/get-started/apps-integrations) the following apps to get dashboards, queries, and alerting for security monitoring and threat investigation. * [**Security Analytics**](/docs/integrations/sumo-apps/security-analytics/). App for alert analysis and Entity risk assessment. -* [**Security and threat detection**](/docs/integrations/security-threat-detection/). Apps for security products, such as firewall tools, endpoint protection applications, and security automation and orchestration programs. For ex ample, the [Threat Intel Quick Analysis](/docs/integrations/security-threat-detection/threat-intel-quick-analysis/) app comes preloaded with queries and dashboards that leverage CrowdStrike’s threat intelligence database. +* [**Security and threat detection**](/docs/integrations/security-threat-detection/). Apps for security products, such as firewall tools, endpoint protection applications, and security automation and orchestration programs. For ex ample, the [Threat Intel Quick Analysis](/docs/integrations/security-threat-detection/threat-intel-quick-analysis/) app comes preloaded with queries and dashboards that leverage Sumo Logic [threat intelligence](/docs/security/threat-intelligence/). * [**Cloud security monitoring and analytics**](/docs/integrations/cloud-security-monitoring-analytics/). Apps that provide security insights for data sources such as Windows, Linux, AWS CloudTrail, AWS VPC Flows, and Palo Alto Networks Firewalls. * [**Global Intelligence Service**](/docs/integrations/global-intelligence/). Apps that provide real-time security intelligence for detection, prioritization, investigation, and workflow. @@ -63,7 +63,7 @@ After you build the dashboard to find and monitor security events, we'll show yo * Detect brute force attempts by monitoring AWS CloudTrail data for a high number of failed login attempts within a period of time. Brute force attacks are when a hacker tries many different passwords to attempt to gain access. These attacks are a common cause of security breaches on governments, businesses, organizations, and private individuals. * Detect land speed violations by using geo lookup location data and combining it with timestamps and the Haversine formula. Land speed violations, also known as impossible travel, are a type of suspicious activity where a user logs in to an account in two different locations within a short period of time. If there are two logins to the same account on opposite sides of the globe in the same hour, at least one of those logins was probably illegitimate. -* Look up user information with CrowdStrike to see if any of the IP addresses you have logged are known threats or have been tied to malicious activity. +* Look up user information with Sumo Logic [threat intelligence](/docs/security/threat-intelligence/find-threats/) to see if any of the IP addresses you have logged are known threats or have been tied to malicious activity. ### Step 1: Monitor user activity with a dashboard @@ -278,29 +278,60 @@ A "landspeed violation" occurs when a user logs in from an IP address and then l 1. Rename this panel **Landspeed Violation**. 1. Click the **Add to Dashboard** button. -### Step 7: Look up user information with CrowdStrike +### Step 7: Look up user information with Sumo Logic threat intelligence -We need a way to see if any of the IP addresses we have logged are known threats or have been tied to malicious activity. Sumo Logic has a partnership with [CrowdStrike](https://www.crowdstrike.com), which allows us to look up IP addresses, email addresses, URLs, and other entities to see if they are known by CrowdStrike. +We need a way to see if any of the IP addresses we have logged are known threats or have been tied to malicious activity. Sumo Logic [threat intelligence](/docs/security/threat-intelligence/) allows us to look up IP addresses, email addresses, URLs, and other entities to see if they are known as threat vectors. 1. Click **Add Panel** and **Time Series**.
}) 1. Type or paste the following code into the query window. (Replace `Labs/AWS/CloudTrail` with a valid source category for AWS CloudTrail logs in your environment.)
- ```
- _sourceCategory=Labs/AWS/CloudTrail
- | parse regex "(?
1. Type or paste the following code into the query window. (Replace `Labs/AWS/CloudTrail` with a valid source category for AWS CloudTrail logs in your environment.)
- ```
- _sourceCategory=Labs/AWS/CloudTrail
- | parse regex "(?}) +
+The sources on the **Threat Intelligence** tab include:
+* **_sumo_global_feed_cs**. This is an out-of-the-box default source of threat indicators supplied by third party intel vendors and maintained by Sumo Logic. You cannot edit this source.
+* **Other sources**. The other sources on the tab are imported by Cloud SIEM administrators so that Cloud SIEM analysts can use them to find threats.
+
+Cloud SIEM analysts can use any of these sources to find threats (see [Threat Intelligence Indicators in Cloud SIEM](/docs/security/threat-intelligence/threat-indicators-in-cloud-siem/)). In addition, all Sumo Logic users can run queries against the indicators in the global feed to uncover threats (see [Find Threats with Log Queries](/docs/security/threat-intelligence/find-threats/)).
+
+
+
+The sources on the **Threat Intelligence** tab include:
+* **_sumo_global_feed_cs**. This is an out-of-the-box default source of threat indicators supplied by third party intel vendors and maintained by Sumo Logic. You cannot edit this source.
+* **Other sources**. The other sources on the tab are imported by Cloud SIEM administrators so that Cloud SIEM analysts can use them to find threats.
+
+Cloud SIEM analysts can use any of these sources to find threats (see [Threat Intelligence Indicators in Cloud SIEM](/docs/security/threat-intelligence/threat-indicators-in-cloud-siem/)). In addition, all Sumo Logic users can run queries against the indicators in the global feed to uncover threats (see [Find Threats with Log Queries](/docs/security/threat-intelligence/find-threats/)).
+
+[**New UI**](/docs/get-started/sumo-logic-ui/). In the top menu select **Administration**, and then under **Users and Roles** select **Roles**. You can also click the **Go To...** menu at the top of the screen and select **Roles**. +1. Click the **Roles** tab. +1. Click **Add Role** to create a new role. Alternatively, you can select an existing role in the **Roles** tab and click **Edit**. +Add the following capabilities: + * **Threat Intel** + * **View Threat Intel Data Store** + * **Manage Threat Intel Data Store** + +You do not need to be assigned these role capabilities to [find threats with log queries](/docs/security/threat-intelligence/find-threats/). + +### Ingest threat intelligence indicators + +A Cloud SIEM administrator must first ingest the indicators before they can be used to uncover threats. Indicators can be ingested using: +* **A collector**. See: + * [CrowdStrike Threat Intel Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-threat-intel-source) + * [Intel471 Threat Intel Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/intel471-threat-intel-source) + * [Mandiant Threat Intel Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/mandiant-threat-intel-source) + * [STIX/TAXII 1 Client Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-1-client-source) + * [STIX/TAXII 2 Client Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-2-client-source) + * [ZeroFox Threat Intel Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/zerofox-intel-source) +* **The API**. See the following APIs in the [Threat Intel Ingest Management](https://api.sumologic.com/docs/#tag/threatIntelIngest) API resource: + * [uploadNormalizedIndicators API](https://api.sumologic.com/docs/#operation/uploadNormalizedIndicators) + * [uploadStixIndicators API](https://api.sumologic.com/docs/#operation/uploadStixIndicators) +* **The Threat Intelligence tab**. Use this tab to upload your own indicators. See [Add indicators in the Threat Intelligence tab](/docs/security/threat-intelligence/threat-intelligence-indicators/#add-indicators-in-the-threat-intelligence-tab). See [Upload formats](/docs/security/threat-intelligence/upload-formats/) for the format to use when uploading indicators using this tab or APIs. + +After threat indicator sources are ingested, they appear on the **Threat Intelligence** tab and are ready to be used in [Cloud SIEM rules](/docs/security/threat-intelligence/threat-indicators-in-cloud-siem/#hasthreatmatch-cloud-siem-rules-language-function) or [manual searches](/docs/security/threat-intelligence/find-threats/). + +
}) +
+Any Sumo Logic user can use this global feed to search for potential threats. To search with the global feed, use `sumo://threat/cs` in log search queries. For example:
+
+```
+_sourceCategory=cylance "IP Address"
+| parse regex "(?
+
+Any Sumo Logic user can use this global feed to search for potential threats. To search with the global feed, use `sumo://threat/cs` in log search queries. For example:
+
+```
+_sourceCategory=cylance "IP Address"
+| parse regex "(?About Threat Intelligence
+Get an osverview of Sumo Logic's threat intelligence capabilities.
+Manage Threat Intelligence Indicators
+Learn how to add and manage indicators from threat intelligence sources.
+Find Threats with Log Queries
+Learn how to perform searches to find matches to data in threat intelligence indicators.
+Threat Indicators in Cloud SIEM
+Learn how to use threat indicators in Cloud SIEM.
+Upload Formats for Threat Intelligence Indicators
+Learn how to format upload files containing threat intelligence indicators.
+Threat Intelligence Mapping
+Learn about mapping of threat intelligence indicators to Sumo Logic.
+}) +
+
\ No newline at end of file
diff --git a/docs/security/threat-intelligence/threat-intelligence-indicators.md b/docs/security/threat-intelligence/threat-intelligence-indicators.md
new file mode 100644
index 0000000000..2395ff8edb
--- /dev/null
+++ b/docs/security/threat-intelligence/threat-intelligence-indicators.md
@@ -0,0 +1,87 @@
+---
+slug: /security/threat-intelligence/threat-intelligence-indicators
+title: Manage Threat Intelligence Indicators
+sidebar_label: Manage Indicators
+description: Learn how to add and manage indicators from threat intelligence sources.
+---
+
+import useBaseUrl from '@docusaurus/useBaseUrl';
+import CloudSIEMThreatIntelNote from '../../reuse/cloud-siem-threat-intelligence-note.md';
+
+The **Threat Intelligence** tab shows the indicators that have been added to your threat intelligence datastore. Use this tab to add and manage your threat intelligence indicators. You can add indicators from a number of sources. Threat intelligence indicators imported to Sumo Logic not only integrate with your existing core Sumo Logic deployment, but also Cloud SIEM and Cloud SOAR.
+
+:::tip
+You can also add threat intelligence indicators using a collector or the API. See [Ingest threat intelligence indicators](/docs/security/threat-intelligence/about-threat-intelligence/#ingest-threat-intelligence-indicators).
+:::
+
+## Threat Intelligence tab
+
+[**Classic UI**](/docs/get-started/sumo-logic-ui-classic/). To access the **Threat Intelligence** tab, in the main Sumo Logic menu, select **Manage Data > Logs > Threat Intelligence**.
+
+[**New UI**](/docs/get-started/sumo-logic-ui/). To access the **Threat Intelligence** tab, in the top menu select **Configuration**, and then under **Logs** select **Threat Intelligence**. You can also click the **Go To...** menu at the top of the screen and select **Threat Intelligence**.
+
+
+
+
\ No newline at end of file
diff --git a/docs/security/threat-intelligence/threat-intelligence-indicators.md b/docs/security/threat-intelligence/threat-intelligence-indicators.md
new file mode 100644
index 0000000000..2395ff8edb
--- /dev/null
+++ b/docs/security/threat-intelligence/threat-intelligence-indicators.md
@@ -0,0 +1,87 @@
+---
+slug: /security/threat-intelligence/threat-intelligence-indicators
+title: Manage Threat Intelligence Indicators
+sidebar_label: Manage Indicators
+description: Learn how to add and manage indicators from threat intelligence sources.
+---
+
+import useBaseUrl from '@docusaurus/useBaseUrl';
+import CloudSIEMThreatIntelNote from '../../reuse/cloud-siem-threat-intelligence-note.md';
+
+The **Threat Intelligence** tab shows the indicators that have been added to your threat intelligence datastore. Use this tab to add and manage your threat intelligence indicators. You can add indicators from a number of sources. Threat intelligence indicators imported to Sumo Logic not only integrate with your existing core Sumo Logic deployment, but also Cloud SIEM and Cloud SOAR.
+
+:::tip
+You can also add threat intelligence indicators using a collector or the API. See [Ingest threat intelligence indicators](/docs/security/threat-intelligence/about-threat-intelligence/#ingest-threat-intelligence-indicators).
+:::
+
+## Threat Intelligence tab
+
+[**Classic UI**](/docs/get-started/sumo-logic-ui-classic/). To access the **Threat Intelligence** tab, in the main Sumo Logic menu, select **Manage Data > Logs > Threat Intelligence**.
+
+[**New UI**](/docs/get-started/sumo-logic-ui/). To access the **Threat Intelligence** tab, in the top menu select **Configuration**, and then under **Logs** select **Threat Intelligence**. You can also click the **Go To...** menu at the top of the screen and select **Threat Intelligence**.
+
+}) +
+1. **+ Add Indicators**. Click to upload files that [add threat intelligence indicators](#add-indicators-in-the-threat-intelligence-tab).
+1. **Actions**. Select to perform additional actions:
+ * **Edit Retention Period**. Enter the length of time in days to retain expired threat intelligence indicator files. The maximum number of days is 180. See [Change the retention period for expired indicators](#change-the-retention-period-for-expired-indicators).
+1. **Status**. The current status of the indicator source (**Enabled** or **Disabled**).
+1. **Source Name**. The name of the threat intelligence indicator file. The name usually indicates the supplier of the indicators.
+1. **Storage Consumed**. The amount of storage consumed by the threat intelligence indicator file.
+1. **Indicators**. The number of threat intelligence indicators included in the file.
+
+:::note
+* The `_sumo_global_feed_cs` source is a default source and cannot be changed or deleted.
+* The default storage limit is 10 million total indicators (not including any indicators provided by Sumo Logic such as the `_sumo_global_feed_cs` source).
+:::
+
+## Add indicators in the Threat Intelligence tab
+
+You can add threat intelligence indicators using a collector, API, or the **Threat Intelligence** tab. This section describes how to add indicators in the **Threat Intelligence** tab. For information on the other methods, see [Ingest threat intelligence indicators](/docs/security/threat-intelligence/about-threat-intelligence/#ingest-threat-intelligence-indicators).
+
+
+
+1. **+ Add Indicators**. Click to upload files that [add threat intelligence indicators](#add-indicators-in-the-threat-intelligence-tab).
+1. **Actions**. Select to perform additional actions:
+ * **Edit Retention Period**. Enter the length of time in days to retain expired threat intelligence indicator files. The maximum number of days is 180. See [Change the retention period for expired indicators](#change-the-retention-period-for-expired-indicators).
+1. **Status**. The current status of the indicator source (**Enabled** or **Disabled**).
+1. **Source Name**. The name of the threat intelligence indicator file. The name usually indicates the supplier of the indicators.
+1. **Storage Consumed**. The amount of storage consumed by the threat intelligence indicator file.
+1. **Indicators**. The number of threat intelligence indicators included in the file.
+
+:::note
+* The `_sumo_global_feed_cs` source is a default source and cannot be changed or deleted.
+* The default storage limit is 10 million total indicators (not including any indicators provided by Sumo Logic such as the `_sumo_global_feed_cs` source).
+:::
+
+## Add indicators in the Threat Intelligence tab
+
+You can add threat intelligence indicators using a collector, API, or the **Threat Intelligence** tab. This section describes how to add indicators in the **Threat Intelligence** tab. For information on the other methods, see [Ingest threat intelligence indicators](/docs/security/threat-intelligence/about-threat-intelligence/#ingest-threat-intelligence-indicators).
+
+[**New UI**](/docs/get-started/sumo-logic-ui/). In the top menu select **Configuration**, and then under **Logs** select **Threat Intelligence**. You can also click the **Go To...** menu at the top of the screen and select **Threat Intelligence**. +1. Click **+ Add Indicators**. The dialog displays.
}) +1. Select the format of the file to be uploaded (see [Upload formats](/docs/security/threat-intelligence/upload-formats/) for the format to use in the file):
+ * **Normalized JSON**. A normalized JSON file.
+ * **CSV**. A comma-separated value (CSV) file.
+
+1. Click **Upload** to upload the file.
+1. Click **Import**.
+
+:::note
+When you add indicators, the event is recorded in the Audit Event Index. See [Audit logging for threat intelligence](/docs/security/threat-intelligence/about-threat-intelligence/#audit-logging-for-threat-intelligence).
+:::
+
+## Delete threat intelligence indicators
+
+1. [**Classic UI**](/docs/get-started/sumo-logic-ui-classic/).In the main Sumo Logic menu, select **Manage Data > Logs > Threat Intelligence**.
+1. Select the format of the file to be uploaded (see [Upload formats](/docs/security/threat-intelligence/upload-formats/) for the format to use in the file):
+ * **Normalized JSON**. A normalized JSON file.
+ * **CSV**. A comma-separated value (CSV) file.
+
+1. Click **Upload** to upload the file.
+1. Click **Import**.
+
+:::note
+When you add indicators, the event is recorded in the Audit Event Index. See [Audit logging for threat intelligence](/docs/security/threat-intelligence/about-threat-intelligence/#audit-logging-for-threat-intelligence).
+:::
+
+## Delete threat intelligence indicators
+
+1. [**Classic UI**](/docs/get-started/sumo-logic-ui-classic/).In the main Sumo Logic menu, select **Manage Data > Logs > Threat Intelligence**. [**New UI**](/docs/get-started/sumo-logic-ui/). In the top menu select **Configuration**, and then under **Logs** select **Threat Intelligence**. You can also click the **Go To...** menu at the top of the screen and select **Threat Intelligence**. +1. Select a source in the list of sources. Details of the source appear in a sidebar. +1. Click the **Delete Indicators** button. + +1. Click **Delete** on the **Delete Indicators** dialog. + +:::note +When you remove indicators, the event is recorded in the Audit Event Index. See [Audit logging for threat intelligence](/docs/security/threat-intelligence/about-threat-intelligence/#audit-logging-for-threat-intelligence). +::: + +## Change the retention period for expired indicators + +Indicators are deemed valid until they reach the date set by their "valid until" attribute (`validUntil` for [normalized JSON](/docs/security/threat-intelligence/upload-formats/#normalized-json-format) and [CSV](/docs/security/threat-intelligence/upload-formats/#csv-format), and `valid_until` for [STIX](/docs/security/threat-intelligence/upload-formats/#stix-2x-json-format)). After that date, they are considered expired. + +Expired indicators are retained until they reach the end of the retention period. At the end of the retention period, expired indicators are automatically deleted. Between the time they expire and are deleted, the indicators are still in the system, and you can search against them if you want. + +By default, expired indicators are retained for 180 days. To change the retention period: +1. [**Classic UI**](/docs/get-started/sumo-logic-ui-classic/).In the main Sumo Logic menu, select **Manage Data > Logs > Threat Intelligence**.
[**New UI**](/docs/get-started/sumo-logic-ui/). In the top menu select **Configuration**, and then under **Logs** select **Threat Intelligence**. You can also click the **Go To...** menu at the top of the screen and select **Threat Intelligence**. +1. Click the three-dot button in the upper-right corner of the page. +1. Click **Edit Retention Period**. +1. Enter the length of time in days to retain expired threat intelligence indicator files. The maximum number of days is 180. + +:::note +When you change the retention period, the event is recorded in the Audit Event Index. See [Audit logging for threat intelligence](/docs/security/threat-intelligence/about-threat-intelligence/#audit-logging-for-threat-intelligence). +::: + +You do not have to wait until indicators reach the end of their retention period in order to delete them. You can [use the **Threat Intelligence** tab to delete indicators](#delete-threat-intelligence-indicators), as well as use the APIs in the [Threat Intel Ingest Management](https://api.sumologic.com/docs/#tag/threatIntelIngest) API resource. diff --git a/docs/security/threat-intelligence/threat-intelligence-mapping.md b/docs/security/threat-intelligence/threat-intelligence-mapping.md new file mode 100644 index 0000000000..f3b09158be --- /dev/null +++ b/docs/security/threat-intelligence/threat-intelligence-mapping.md @@ -0,0 +1,95 @@ +--- +slug: /security/threat-intelligence/threat-intelligence-mapping +title: Threat Intelligence Mapping +sidebar_label: Mapping +description: Learn about mapping of threat intelligence indicators to Sumo Logic. +--- + +import useBaseUrl from '@docusaurus/useBaseUrl'; + +## Global feed mapping + +Sumo Logic provides an out-of-the-box a `_sumo_global_feed_cs` source of threat intelligence indicators supplied by Sumo Logic. You can see it in the [**Threat Intelligence** tab](/docs/security/threat-intelligence/threat-intelligence-indicators/#threat-intelligence-tab). This source is a default source and cannot be changed or deleted. + +In the threat intelligence datastore, the schema is mapped to normalized values to provide ease of interoperability with the schema from other threat intelligence sources: + +| Original schema | Normalized schema in the datastore | +|:--|:--| +| `actor` | `actors` | +| `id` | `id` | +| `indicator` | `indicator` | +| `kill_chain_phases` | `killChain` | +| `labels.ThreatType` | `threatType` | +| `last_updated` | `updated` | +| `malicious_confidence` | `confidence` (normalized to the 0-100 scale) | +| `published_date` | `validFrom` and `imported` | +| `type` | `type` | + +(All other fields will be kept in the `fields{}` object.) + +The `type` object is mapped to the following normalized type values: + +| Type | Normalized type in the datastore | +|:--|:--| +| `binary_string` | `artifact:payload_bin` | +| `bitcoin_address` | `url` | +| `ip_address` | `ipv4-addr` / `ipv6-addr` | +| `domain` | `domain-name` | +| `email_address` | `email-add` | +| `file_path` | `file:name` | +| `file_name` | `file:name` | +| `hash_md5` | `file:hashes.'MD5'` | +| `hash_sha1` | `file:hashes.'SHA-1'` | +| `hash_sha256` | `file:hashes.'SHA-256'` | +| `mutex_name` | `mutex:name` | +| `service_name` | `process:name` | +| `url` | `url` | +| `username` | `user-account:user_id` | +| `user_agent` | `http-request-ext:request_header.'User-Agent'` | +| `x509_subject` | `x509-certificate:serial_number` | + + + + diff --git a/docs/security/threat-intelligence/upload-formats.md b/docs/security/threat-intelligence/upload-formats.md new file mode 100644 index 0000000000..eb1a254cbd --- /dev/null +++ b/docs/security/threat-intelligence/upload-formats.md @@ -0,0 +1,265 @@ +--- +slug: /security/threat-intelligence/upload-formats +title: Upload Formats for Threat Intelligence Indicators +sidebar_label: Upload Formats +description: Learn how to format upload files containing threat intelligence indicators. +--- + +import useBaseUrl from '@docusaurus/useBaseUrl'; + +Use the following formats for threat intelligence indicator files when you [add indicators in the **Threat Intelligence** tab](/docs/security/threat-intelligence/threat-intelligence-indicators/#add-indicators-in-the-threat-intelligence-tab) or when you use the upload APIs in the [Threat Intel Ingest Management](https://api.sumologic.com/docs/#tag/threatIntelIngest) API resource: + +* [Normalized JSON format](#normalized-json-format) +* [CSV format](#csv-format) +* [STIX 2.x JSON format](#stix-2x-json-format) + +## Normalized JSON format + +Normalized JSON format is a standardized method to present JSON data. You can use this format to load indicators from multiple sources. + +### Example file + +Following is an example threat indicator file in normalized JSON format. (For another example, see the [uploadNormalizedIndicators API](https://api.sumologic.com/docs/#operation/uploadNormalizedIndicators)). + +```json +{ + "indicators": [ + { + "id": "0001", + "indicator": "192.0.2.0", + "type": "ipv4-addr", + "source": "TAXII2Source", + "validFrom": "2023-03-21T12:00:00.000Z", + "validUntil": "2025-03-21T12:00:00.000Z", + "confidence": 30, + "threatType": "malicious-activity", + "actors": "actor1,actor2", + "killChain": "reconnaissance", + "fields": { + "kill_chain_name": "lockheed-martin-cyber-kill-chain", + "kill_chain_phase": "reconnaissance" + } + }, + { + "id": "0002", + "indicator": "192.0.2.1", + "type": "ipv4-addr", + "source": "TAXII2Source", + "validFrom": "2023-03-21T12:00:00.000Z", + "validUntil": "2025-03-21T12:00:00.000Z", + "confidence": 30, + "threatType": "malicious-activity", + "actors": "actor3,actor4", + "killChain": "reconnaissance", + "fields": { + "kill_chain_name": "lockheed-martin-cyber-kill-chain", + "kill_chain_phase": "reconnaissance" + } + } + ] +} +``` + +### Required attributes + +For information about the attributes to use, see ["Indicator" in the STIX 2.1 specification](https://docs.oasis-open.org/cti/stix/v2.1/os/stix-v2.1-os.html#_muftrcpnf89v), and the [uploadNormalizedIndicators API](https://api.sumologic.com/docs/#operation/uploadNormalizedIndicators) in the [Threat Intel Ingest Management](https://api.sumologic.com/docs/#tag/threatIntelIngest) API resource. + +The following attributes are required: + * **id** (string). ID of the indicator. For example, `indicator--d81f86b9-975b-4c0b-875e-810c5ad45a4f`. + * **indicator** (string). Value of the indicator, such as an IP address, file name, email address, etc. For example, `192.0.2.0`. + * **type** (string). Type of the indicator. Following are valid values: + * `domain-name`. Domain name. (Entity type in Cloud SIEM is `_domain`.) + * `email-addr`. Email address. (Entity type in Cloud SIEM is `_email`.) + * `file`. File name. (Entity type in Cloud SIEM is `_file`.) + * `file:hashes`. File hash. (Entity type in Cloud SIEM is `_hash`.)
If you want to add the hash algorithm, enter `file:hashes.
Following are valid values: + * `anomalous-activity`. Unexpected or unusual activity that may not necessarily be malicious or indicate compromise. + * `anonymization`. Suspected anonymization tools or infrastructure (proxy, TOR, VPN, etc.). + * `benign`. Activity that is not suspicious or malicious in and of itself, but when combined with other activity may indicate suspicious or malicious behavior. + * `compromised`. Assets that are suspected to be compromised. + * `malicious-activity`. Patterns of suspected malicious objects and/or activity. + * `attribution`. Patterns of behavior that indicate attribution to a particular threat actor or campaign. + * `unknown` (or not set). There is not enough information available to determine the threat type. + + The following attributes are optional: + * **actors** (string list). An identified threat actor such as an individual, organization, or group. For example, `actor1`. + * **killChain** (string list). The various phases an attacker may undertake to achieve their objectives (as [defined by kill_chain_phase in STIX 2.1](https://docs.oasis-open.org/cti/stix/v2.1/os/stix-v2.1-os.html#_i4tjv75ce50h)). For example, `reconnaissance`. Although you can use any kill chain definition and values you want, following are example values based on the standard stages in a kill chain: + * `reconnaissance`. Researching potential targets. + * `weaponization`. Creation of malware to be used against an identified target. + * `delivery`. Infiltration of a target’s network and users. + * `exploitation`. Taking advantage of the vulnerabilities discovered in previous stages to further infiltrate a target’s network and achieve objectives. + * `installation`. Install malware and other artifacts onto the target network to take control of its systems and exfiltrate valuable data. + * `command-and-control`. Communication with the installed malware. + * `actions-on-objectives`. Carrying out cyberattack objectives. + +## CSV format + +Comma-separated value (CSV) is a standard format for data upload. + +### Example file + +When uploading a CSV file with the UI, the format should be the same as used for a standard CSV file: + +``` +0001,192.0.2.0,ipv4-addr,TAXII2Source,2023-02-21T12:00:00.00Z,2025-05-21T12:00:00.00Z,30,malicious-activity,, +0002,192.0.2.1,ipv4-addr,TAXII2Source,2023-02-21T12:00:00.00Z,2025-05-21T12:00:00.00Z,30,malicious-activity,actor3,reconnaissance +``` + +### Required attributes + +For information about the attributes to use, see ["Indicator" in the STIX 2.1 specification](https://docs.oasis-open.org/cti/stix/v2.1/os/stix-v2.1-os.html#_muftrcpnf89v). + +Columns for the following attributes are required in the upload file: + * **id** (string). ID of the indicator. For example, `indicator--d81f86b9-975b-4c0b-875e-810c5ad45a4f`. + * **indicator** (string). Value of the indicator, such as an IP address, file name, email address, etc. For example, `192.0.2.0`. + * **type** (string). Type of the indicator. Following are valid values: + * `domain-name`. Domain name. (Entity type in Cloud SIEM is `_domain`.) + * `email-addr`. Email address. (Entity type in Cloud SIEM is `_email`.) + * `file`. File name. (Entity type in Cloud SIEM is `_file`.) + * `file:hashes`. File hash. (Entity type in Cloud SIEM is `_hash`.)
If you want to add the hash algorithm, enter `file:hashes.
Following are valid values: + * `anomalous-activity`. Unexpected or unusual activity that may not necessarily be malicious or indicate compromise. + * `anonymization`. Suspected anonymization tools or infrastructure (proxy, TOR, VPN, etc.). + * `benign`. Activity that is not suspicious or malicious in and of itself, but when combined with other activity may indicate suspicious or malicious behavior. + * `compromised`. Assets that are suspected to be compromised. + * `malicious-activity`. Patterns of suspected malicious objects and/or activity. + * `attribution`. Patterns of behavior that indicate attribution to a particular threat actor or campaign. + * `unknown` (or not set). There is not enough information available to determine the threat type. + + The following attributes are optional: + * **actors** (string list). An identified threat actor such as an individual, organization, or group. For example, `actor3`. Note if you don’t provide a value for `actors`, you still must provide the empty column at the end of the row with an extra comma, as shown in the examples above. + * **killChain** (string list). The various phases an attacker may undertake to achieve their objectives (as [defined by kill_chain_phase in STIX 2.1](https://docs.oasis-open.org/cti/stix/v2.1/os/stix-v2.1-os.html#_i4tjv75ce50h)). For example, `reconnaissance`. Although you can use any kill chain definition and values you want, following are example values based on the standard stages in a kill chain: + * `reconnaissance`. Researching potential targets. + * `weaponization`. Creation of malware to be used against an identified target. + * `delivery`. Infiltration of a target’s network and users. + * `exploitation`. Taking advantage of the vulnerabilities discovered in previous stages to further infiltrate a target’s network and achieve objectives. + * `installation`. Install malware and other artifacts onto the target network to take control of its systems and exfiltrate valuable data. + * `command-and-control`. Communication with the installed malware. + * `actions-on-objectives`. Carrying out cyberattack objectives. + +## STIX 2.x JSON format + +STIX 2.x JSON format is a method to present JSON data according to the STIX 2.x specification. + +Note that if you want to upload indicators from multiple sources, you cannot use this format but instead should use the [Normalized JSON format](#normalized-json-format). + +Also note that if your STIX file includes lines like these at the top... + +``` +{ + "type": "bundle", + "id": "bundle--cf20f99b-3ed2-4a9f-b4f1-d660a7fc8241", + "objects": [ + { + "type": "indicator", +``` + +...you should remove them before uploading the file, and leave only the objects array like this: + +``` +[ + { + "type": "indicator", +``` + + +### Example file + +Following is an example threat indicator file in STIX 2.1 JSON format when you're uploading a file with the API. + +As shown in the following example, if uploading via the API you must add the `source` attribute outside of the indicators object, since the source is not part of the STIX standard. You must also include an `indicators` array field. (For another example for uploading via the API, see the [uploadStixIndicators API](https://api.sumologic.com/docs/#operation/uploadStixIndicators)). + +```json +{ + "source": "TAXII2Source", + "indicators": [ + { + "type": "indicator", + "spec_version": "2.1", + "id": "0001", + "created": "2023-03-21T12:00:00.000Z", + "modified": "2023-03-21T12:00:00.000Z", + "confidence": 30, + "pattern": "[ipv4-addr = '192.0.2.0']", + "pattern_type": "stix", + "pattern_version": "string", + "valid_from": "2023-03-21T12:00:00.000Z", + "valid_until": "2025-03-21T12:00:00.000Z", + "indicator_types": [ + "malicious-activity" + ], + "kill_chain_phases": [ + { + "kill_chain_name": "lockheed-martin-cyber-kill-chain", + "phase_name": "reconnaissance" + } + ] + }, + { + "type": "indicator", + "spec_version": "2.1", + "id": "0002", + "created": "2023-03-21T12:00:00.000Z", + "modified": "2023-03-21T12:00:00.000Z", + "confidence": 30, + "pattern": "[ipv4-addr = '192.0.2.1']", + "pattern_type": "stix", + "pattern_version": "string", + "valid_from": "2023-03-21T12:00:00.000Z", + "valid_until": "2025-03-21T12:00:00.000Z", + "indicator_types": [ + "malicious-activity" + ], + "kill_chain_phases": [ + { + "kill_chain_name": "lockheed-martin-cyber-kill-chain", + "phase_name": "reconnaissance" + } + ] + } + ] +} +``` + +### Required attributes + +For information about the attributes to use, see ["Indicator" in the STIX 2.1 specification](https://docs.oasis-open.org/cti/stix/v2.1/os/stix-v2.1-os.html#_muftrcpnf89v), and the [uploadStixIndicators API](https://api.sumologic.com/docs/#operation/uploadStixIndicators) in the [Threat Intel Ingest Management](https://api.sumologic.com/docs/#tag/threatIntelIngest) API resource. + +The following attributes are required: + * **type** (string). The type of STIX object. For example, `indicator`. The value must be the name of one of the types of STIX objects defined in the STIX 2.x specification. + * **spec_version** (string). The version of the STIX specification used to represent this object. For example, the value of this property must be `2.1` for STIX objects defined according to the STIX 2.1 specification. + * **id** (string). ID of the indicator. For example, `indicator--d81f86b9-975b-4c0b-875e-810c5ad45a4f`. + * **created** (string [date-time]). The time at which the object was originally created. Timestamp in UTC in RFC3339 format. For example, `2016-05-01T06:13:14.000Z`. + * **modified** (string [date-time]). When the object is modified. Timestamp in UTC in RFC3339 format. For example, `2023-05-01T06:13:14.000Z`. This property is only used by STIX Objects that support versioning and represents the time that this particular version of the object was last modified. + * **pattern** (string). The pattern of this indicator (as defined by [pattern in STIX 2.1](https://docs.oasis-open.org/cti/stix/v2.1/os/stix-v2.1-os.html#_me3pzm77qfnf)). Following are valid values: + * `domain-name`. Domain name. (Entity type in Cloud SIEM is `_domain`.) + * `email-addr`. Email address. (Entity type in Cloud SIEM is `_email`.) + * `file:hashes`. File hash. (Entity type in Cloud SIEM is `_hash`.)
If you want to add the hash algorithm, enter `file:hashes.
Learn how to collect combined endpoint vulnerabilities data from the CrowdStrike Spotlight platform.
-})
CyberArk EPM
@@ -315,14 +313,12 @@ In this section, we'll introduce the following concepts:Collects a list of users from the Google Workspace Users API.
})
Jamf
@@ -371,6 +367,12 @@ In this section, we'll introduce the following concepts:Collects user and device data from the Microsoft Graph API Security endpoint.
})
Mandiant Threat Intel
+Learn to collect threat indicators from the Mandiant platform.
+Microsoft Exchange Trace Logs
@@ -491,6 +493,18 @@ In this section, we'll introduce the following concepts:Learn to receive authentication logs from the Sophos Central APIs.
})
STIX/TAXII 1 Client
+Learn how to set up a STIX/TAXII 1.x client to collect threat intelligence indicators into the Sumo Logic environment.
+})
STIX/TAXII 2 Client
+Learn how to set up a STIX/TAXII 2.x client to collect threat intelligence indicators into the Sumo Logic environment.
+Symantec Endpoint Security Source
@@ -563,6 +577,12 @@ In this section, we'll introduce the following concepts:Learn to collect audit logs from the Zendesk platform.
ZeroFox
+Learn to collect threat indicators using the ZeroFox API and send them to Sumo Logic for analysis.
+Zero Networks Segment
diff --git a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/intel-471-threat-intel-source.md b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/intel-471-threat-intel-source.md index ff0439b1fb..acaa589d0c 100644 --- a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/intel-471-threat-intel-source.md +++ b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/intel-471-threat-intel-source.md @@ -13,17 +13,11 @@ import MyComponentSource from '!!raw-loader!/files/c2c/intel471-threat-intel/exa import TerraformExample from '!!raw-loader!/files/c2c/intel471-threat-intel/example.tf'; import useBaseUrl from '@docusaurus/useBaseUrl'; - - - - - -}) -Intel471 is a cybersecurity firm specializing in providing cyber threat intelligence services. Their focus is primarily on delivering information about threats originating from the criminal underground, including malware, malicious actors, and their tactics, techniques, and procedures (TTPs). Intel471 provides these insights to help organizations protect themselves against cyber threats. Their intelligence-gathering efforts often involve monitoring and analyzing underground marketplaces, forums, and other communication channels used by cyber criminals.
+The Intel471 Threat Intel source collects threat intelligence indicators using the [Intel471 Stream API](https://titan.intel471.com/api/docs-openapi/#tag/Indicators/paths/~1indicators~1stream/get) and sends them to Sumo Logic as normalized threat indicators for analysis. For more information about Sumo Logic threat intelligence, see [About Threat Intelligence](/docs/security/threat-intelligence/about-threat-intelligence/).
-The Intel471 source collects threat indicators using the [Intel471 Stream API](https://titan.intel471.com/api/docs-openapi/#tag/Indicators/paths/~1indicators~1stream/get) and sends them to Sumo Logic as normalized threat indicators for analysis.
+Intel471 is a cybersecurity firm specializing in providing cyber threat intelligence services. Their focus is primarily on delivering information about threats originating from the criminal underground, including malware, malicious actors, and their tactics, techniques, and procedures (TTPs). Intel471 provides these insights to help organizations protect themselves against cyber threats. Their intelligence-gathering efforts often involve monitoring and analyzing underground marketplaces, forums, and other communication channels used by cyber criminals.
## Data collected
diff --git a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/mandiant-threat-intel-source.md b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/mandiant-threat-intel-source.md
index 3e25c1c14f..789e19f5f9 100644
--- a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/mandiant-threat-intel-source.md
+++ b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/mandiant-threat-intel-source.md
@@ -1,7 +1,7 @@
---
id: mandiant-threat-intel-source
-title: Mandiant Threat Intel Source (Beta)
-sidebar_label: Mandiant Threat Intel (Beta)
+title: Mandiant Threat Intel Source
+sidebar_label: Mandiant Threat Intel
tags:
- cloud-to-cloud
- mandiant-threat-intel
@@ -13,15 +13,11 @@ import MyComponentSource from '!!raw-loader!/files/c2c/mandiant-threat-intel/exa
import TerraformExample from '!!raw-loader!/files/c2c/mandiant-threat-intel/example.tf';
import useBaseUrl from '@docusaurus/useBaseUrl';
-
-
-
-
-
-
-Intel471 is a cybersecurity firm specializing in providing cyber threat intelligence services. Their focus is primarily on delivering information about threats originating from the criminal underground, including malware, malicious actors, and their tactics, techniques, and procedures (TTPs). Intel471 provides these insights to help organizations protect themselves against cyber threats. Their intelligence-gathering efforts often involve monitoring and analyzing underground marketplaces, forums, and other communication channels used by cyber criminals.
+The Intel471 Threat Intel source collects threat intelligence indicators using the [Intel471 Stream API](https://titan.intel471.com/api/docs-openapi/#tag/Indicators/paths/~1indicators~1stream/get) and sends them to Sumo Logic as normalized threat indicators for analysis. For more information about Sumo Logic threat intelligence, see [About Threat Intelligence](/docs/security/threat-intelligence/about-threat-intelligence/).
-The Intel471 source collects threat indicators using the [Intel471 Stream API](https://titan.intel471.com/api/docs-openapi/#tag/Indicators/paths/~1indicators~1stream/get) and sends them to Sumo Logic as normalized threat indicators for analysis.
+Intel471 is a cybersecurity firm specializing in providing cyber threat intelligence services. Their focus is primarily on delivering information about threats originating from the criminal underground, including malware, malicious actors, and their tactics, techniques, and procedures (TTPs). Intel471 provides these insights to help organizations protect themselves against cyber threats. Their intelligence-gathering efforts often involve monitoring and analyzing underground marketplaces, forums, and other communication channels used by cyber criminals.
## Data collected
diff --git a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/mandiant-threat-intel-source.md b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/mandiant-threat-intel-source.md
index 3e25c1c14f..789e19f5f9 100644
--- a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/mandiant-threat-intel-source.md
+++ b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/mandiant-threat-intel-source.md
@@ -1,7 +1,7 @@
---
id: mandiant-threat-intel-source
-title: Mandiant Threat Intel Source (Beta)
-sidebar_label: Mandiant Threat Intel (Beta)
+title: Mandiant Threat Intel Source
+sidebar_label: Mandiant Threat Intel
tags:
- cloud-to-cloud
- mandiant-threat-intel
@@ -13,15 +13,11 @@ import MyComponentSource from '!!raw-loader!/files/c2c/mandiant-threat-intel/exa
import TerraformExample from '!!raw-loader!/files/c2c/mandiant-threat-intel/example.tf';
import useBaseUrl from '@docusaurus/useBaseUrl';
-
-
-
-
-
-
}) -Mandiant is a recognized leader in dynamic cyber defense, threat intelligence, and incident response services. By scaling decades of frontline experience, Mandiant helps organizations to be confident in their readiness to defend against and respond to cyber threats. Mandiant is part of Google Cloud. The Mandiant Threat Intel integration ingests the indicators data from Mandiant API and sends it to Sumo Logic as normalized threat indicators.
+The Mandiant Threat Intel source ingests threat intelligence indicators using the Mandiant API and sends them to Sumo Logic as normalized threat indicators. For more information about Sumo Logic threat intelligence, see [About Threat Intelligence](/docs/security/threat-intelligence/about-threat-intelligence/).
+
+Mandiant is a recognized leader in dynamic cyber defense, threat intelligence, and incident response services. By scaling decades of frontline experience, Mandiant helps organizations to be confident in their readiness to defend against and respond to cyber threats. Mandiant is part of Google Cloud.
## Data collected
diff --git a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-1-client-source.md b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-1-client-source.md
index 0ef8c78f1c..190d07a5f4 100644
--- a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-1-client-source.md
+++ b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-1-client-source.md
@@ -15,13 +15,9 @@ import MyComponentSource from '!!raw-loader!/files/c2c/taxii-1/example.json';
import TerraformExample from '!!raw-loader!/files/c2c/taxii-1/example.tf';
import useBaseUrl from '@docusaurus/useBaseUrl';
-
-
-
+The STIX/TAXII 1 Client source supports collecting threat intelligence indicators from STIX/TAXII 1.x and sending them to Sumo Logic as normalized threat indicators. For more information about Sumo Logic threat intelligence, see [About Threat Intelligence](/docs/security/threat-intelligence/about-threat-intelligence/).
-
-
-[STIX/TAXII](https://oasis-open.github.io/cti-documentation/) are two standards used together to exchange threat intelligence information between systems. STIX defines the format and structure of the data. TAXII defines how the API endpoints are served and accessed by clients. This Sumo Logic source supports collecting indicators from STIX/TAXII 1.x.
+[STIX/TAXII](https://oasis-open.github.io/cti-documentation/) are two standards used together to exchange threat intelligence information between systems. STIX defines the format and structure of the data. TAXII defines how the API endpoints are served and accessed by clients.
:::sumo[Best Practice]
This source only supports STIX/TAXII 1.x. Sumo Logic recommends using our [STIX/TAXII 2.x source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-2-client-source/) instead as it is the current version of STIX/TAXII.
@@ -29,7 +25,7 @@ This source only supports STIX/TAXII 1.x. Sumo Logic recommends using our [STIX/
## Data collected
-This source collects [threat intelligence indicators](/docs/platform-services/threat-intelligence-indicators/) from a vendor's STIX/TAXII 1.x endpoints. This means the specific endpoints we collect data from are the endpoints defined in the [TAXII standard](https://oasis-open.github.io/cti-documentation/taxii/intro). Vendor APIs must follow the standard. The source will collect all indicators from the TAXII server when it runs for the first time and it will check for updates once an hour. This one-hour polling interval can be adjusted in the source configuration.
+This source collects threat intelligence indicators from a vendor's STIX/TAXII 1.x endpoints. This means the specific endpoints we collect data from are the endpoints defined in the [TAXII standard](https://oasis-open.github.io/cti-documentation/taxii/intro). Vendor APIs must follow the standard. The source will collect all indicators from the TAXII server when it runs for the first time and it will check for updates once an hour. This one-hour polling interval can be adjusted in the source configuration.
## Setup
diff --git a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-2-client-source.md b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-2-client-source.md
index 1ab0ddfdc4..1e7e868c66 100644
--- a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-2-client-source.md
+++ b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-2-client-source.md
@@ -15,17 +15,15 @@ import MyComponentSource from '!!raw-loader!/files/c2c/taxii-2/example.json';
import TerraformExample from '!!raw-loader!/files/c2c/taxii-2/example.tf';
import useBaseUrl from '@docusaurus/useBaseUrl';
-
-
-
+The STIX/TAXII 2 Client source supports collecting threat intelligence indicators from STIX/TAXII 2.0 and 2.1 versions. For more information about Sumo Logic threat intelligence, see [About Threat Intelligence](/docs/security/threat-intelligence/about-threat-intelligence/).
-
+The legacy STIX/TAXII 1.x versions are not supported with this source. Use [STIX/TAXII 1 Client Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-1-client-source/) for version 1.x versions.
-[STIX/TAXII](https://oasis-open.github.io/cti-documentation/) are two standards used together to exchange threat intelligence information between systems. STIX defines the format and structure of the data. TAXII defines how the API endpoints are served and accessed by clients. This Sumo Logic source supports collecting indicators from STIX/TAXII 2.0 and 2.1 versions. The legacy STIX/TAXII 1.x versions are not supported with this source.
+[STIX/TAXII](https://oasis-open.github.io/cti-documentation/) are two standards used together to exchange threat intelligence information between systems. STIX defines the format and structure of the data. TAXII defines how the API endpoints are served and accessed by clients.
## Data collected
-This source collects [threat intelligence indicators](/docs/platform-services/threat-intelligence-indicators/) from a vendor's STIX/TAXII 2.x endpoints. This means the specific endpoints we collect data from are the endpoints defined in the [TAXII standard](https://oasis-open.github.io/cti-documentation/taxii/intro). Vendor APIs must follow the standard. The source will collect all indicators from the TAXII server when it runs for the first time and it will check for updates once an hour. This one-hour polling interval can be adjusted in the source configuration.
+This source collects threat intelligence indicators from a vendor's STIX/TAXII 2.x endpoints. This means the specific endpoints we collect data from are the endpoints defined in the [TAXII standard](https://oasis-open.github.io/cti-documentation/taxii/intro). Vendor APIs must follow the standard. The source will collect all indicators from the TAXII server when it runs for the first time and it will check for updates once an hour. This one-hour polling interval can be adjusted in the source configuration.
## Setup
diff --git a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/zerofox-intel-source.md b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/zerofox-intel-source.md
index e6cd76b003..6ba50629cc 100644
--- a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/zerofox-intel-source.md
+++ b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/zerofox-intel-source.md
@@ -13,13 +13,7 @@ import MyComponentSource from '!!raw-loader!/files/c2c/zerofox/example.json';
import TerraformExample from '!!raw-loader!/files/c2c/zerofox/example.tf';
import useBaseUrl from '@docusaurus/useBaseUrl';
-
-
-
-
-
-
-
-Mandiant is a recognized leader in dynamic cyber defense, threat intelligence, and incident response services. By scaling decades of frontline experience, Mandiant helps organizations to be confident in their readiness to defend against and respond to cyber threats. Mandiant is part of Google Cloud. The Mandiant Threat Intel integration ingests the indicators data from Mandiant API and sends it to Sumo Logic as normalized threat indicators.
+The Mandiant Threat Intel source ingests threat intelligence indicators using the Mandiant API and sends them to Sumo Logic as normalized threat indicators. For more information about Sumo Logic threat intelligence, see [About Threat Intelligence](/docs/security/threat-intelligence/about-threat-intelligence/).
+
+Mandiant is a recognized leader in dynamic cyber defense, threat intelligence, and incident response services. By scaling decades of frontline experience, Mandiant helps organizations to be confident in their readiness to defend against and respond to cyber threats. Mandiant is part of Google Cloud.
## Data collected
diff --git a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-1-client-source.md b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-1-client-source.md
index 0ef8c78f1c..190d07a5f4 100644
--- a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-1-client-source.md
+++ b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-1-client-source.md
@@ -15,13 +15,9 @@ import MyComponentSource from '!!raw-loader!/files/c2c/taxii-1/example.json';
import TerraformExample from '!!raw-loader!/files/c2c/taxii-1/example.tf';
import useBaseUrl from '@docusaurus/useBaseUrl';
-
-
-
+The STIX/TAXII 1 Client source supports collecting threat intelligence indicators from STIX/TAXII 1.x and sending them to Sumo Logic as normalized threat indicators. For more information about Sumo Logic threat intelligence, see [About Threat Intelligence](/docs/security/threat-intelligence/about-threat-intelligence/).
-
-
-[STIX/TAXII](https://oasis-open.github.io/cti-documentation/) are two standards used together to exchange threat intelligence information between systems. STIX defines the format and structure of the data. TAXII defines how the API endpoints are served and accessed by clients. This Sumo Logic source supports collecting indicators from STIX/TAXII 1.x.
+[STIX/TAXII](https://oasis-open.github.io/cti-documentation/) are two standards used together to exchange threat intelligence information between systems. STIX defines the format and structure of the data. TAXII defines how the API endpoints are served and accessed by clients.
:::sumo[Best Practice]
This source only supports STIX/TAXII 1.x. Sumo Logic recommends using our [STIX/TAXII 2.x source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-2-client-source/) instead as it is the current version of STIX/TAXII.
@@ -29,7 +25,7 @@ This source only supports STIX/TAXII 1.x. Sumo Logic recommends using our [STIX/
## Data collected
-This source collects [threat intelligence indicators](/docs/platform-services/threat-intelligence-indicators/) from a vendor's STIX/TAXII 1.x endpoints. This means the specific endpoints we collect data from are the endpoints defined in the [TAXII standard](https://oasis-open.github.io/cti-documentation/taxii/intro). Vendor APIs must follow the standard. The source will collect all indicators from the TAXII server when it runs for the first time and it will check for updates once an hour. This one-hour polling interval can be adjusted in the source configuration.
+This source collects threat intelligence indicators from a vendor's STIX/TAXII 1.x endpoints. This means the specific endpoints we collect data from are the endpoints defined in the [TAXII standard](https://oasis-open.github.io/cti-documentation/taxii/intro). Vendor APIs must follow the standard. The source will collect all indicators from the TAXII server when it runs for the first time and it will check for updates once an hour. This one-hour polling interval can be adjusted in the source configuration.
## Setup
diff --git a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-2-client-source.md b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-2-client-source.md
index 1ab0ddfdc4..1e7e868c66 100644
--- a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-2-client-source.md
+++ b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-2-client-source.md
@@ -15,17 +15,15 @@ import MyComponentSource from '!!raw-loader!/files/c2c/taxii-2/example.json';
import TerraformExample from '!!raw-loader!/files/c2c/taxii-2/example.tf';
import useBaseUrl from '@docusaurus/useBaseUrl';
-
-
-
+The STIX/TAXII 2 Client source supports collecting threat intelligence indicators from STIX/TAXII 2.0 and 2.1 versions. For more information about Sumo Logic threat intelligence, see [About Threat Intelligence](/docs/security/threat-intelligence/about-threat-intelligence/).
-
+The legacy STIX/TAXII 1.x versions are not supported with this source. Use [STIX/TAXII 1 Client Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-1-client-source/) for version 1.x versions.
-[STIX/TAXII](https://oasis-open.github.io/cti-documentation/) are two standards used together to exchange threat intelligence information between systems. STIX defines the format and structure of the data. TAXII defines how the API endpoints are served and accessed by clients. This Sumo Logic source supports collecting indicators from STIX/TAXII 2.0 and 2.1 versions. The legacy STIX/TAXII 1.x versions are not supported with this source.
+[STIX/TAXII](https://oasis-open.github.io/cti-documentation/) are two standards used together to exchange threat intelligence information between systems. STIX defines the format and structure of the data. TAXII defines how the API endpoints are served and accessed by clients.
## Data collected
-This source collects [threat intelligence indicators](/docs/platform-services/threat-intelligence-indicators/) from a vendor's STIX/TAXII 2.x endpoints. This means the specific endpoints we collect data from are the endpoints defined in the [TAXII standard](https://oasis-open.github.io/cti-documentation/taxii/intro). Vendor APIs must follow the standard. The source will collect all indicators from the TAXII server when it runs for the first time and it will check for updates once an hour. This one-hour polling interval can be adjusted in the source configuration.
+This source collects threat intelligence indicators from a vendor's STIX/TAXII 2.x endpoints. This means the specific endpoints we collect data from are the endpoints defined in the [TAXII standard](https://oasis-open.github.io/cti-documentation/taxii/intro). Vendor APIs must follow the standard. The source will collect all indicators from the TAXII server when it runs for the first time and it will check for updates once an hour. This one-hour polling interval can be adjusted in the source configuration.
## Setup
diff --git a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/zerofox-intel-source.md b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/zerofox-intel-source.md
index e6cd76b003..6ba50629cc 100644
--- a/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/zerofox-intel-source.md
+++ b/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/zerofox-intel-source.md
@@ -13,13 +13,7 @@ import MyComponentSource from '!!raw-loader!/files/c2c/zerofox/example.json';
import TerraformExample from '!!raw-loader!/files/c2c/zerofox/example.tf';
import useBaseUrl from '@docusaurus/useBaseUrl';
-
-
-
-
-
-
-}) +
+}) ZeroFox is a cybersecurity firm specializing in providing cyber threat intelligence services.
diff --git a/docusaurus.config.js b/docusaurus.config.js
index b70d457cd4..f3493f318a 100644
--- a/docusaurus.config.js
+++ b/docusaurus.config.js
@@ -264,6 +264,12 @@ module.exports = {
background: 'rgba(0, 0, 0, 0.6)',
},
},
+ announcementBar: {
+ id: 'support_us',
+ content: '
ZeroFox is a cybersecurity firm specializing in providing cyber threat intelligence services.
diff --git a/docusaurus.config.js b/docusaurus.config.js
index b70d457cd4..f3493f318a 100644
--- a/docusaurus.config.js
+++ b/docusaurus.config.js
@@ -264,6 +264,12 @@ module.exports = {
background: 'rgba(0, 0, 0, 0.6)',
},
},
+ announcementBar: {
+ id: 'support_us',
+ content: 'We are aware of the recent CrowdStrike and Microsoft outages. Our operations remain unaffected, and service continues uninterrupted. Thank you for your continued trust in Sumo Logic.
', + backgroundColor: '#fafbfc', + textColor: '#091E42', + }, colorMode: { defaultMode: 'light', }, diff --git a/sidebars.ts b/sidebars.ts index 5601485269..0ba338c922 100644 --- a/sidebars.ts +++ b/sidebars.ts @@ -453,7 +453,7 @@ module.exports = { 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-fdr-host-inventory-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-filevantage-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-spotlight-source', - //'send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-threat-intel-source', + 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/crowdstrike-threat-intel-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/cyberark-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/cyberark-audit-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/cybereason-source', @@ -468,7 +468,7 @@ module.exports = { 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/google-bigquery-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/google-workspace-alertcenter', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/google-workspace-source', - // 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/intel471-threat-intel-source', + 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/intel471-threat-intel-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/jamf-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/jfrog-xray-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/jumpcloud-directory-insights-source', @@ -476,7 +476,7 @@ module.exports = { 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/kandji-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/knowbe4-api-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/lastpass-source', - //'send-data/hosted-collectors/cloud-to-cloud-integration-framework/mandiant-threat-intel-source', + 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/mandiant-threat-intel-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/microsoft-azure-ad-inventory-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/microsoft-exchange-trace-logs', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/microsoft-graph-azure-ad-reporting-source', @@ -499,6 +499,8 @@ module.exports = { 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/smartsheet-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/snowflake-sql-api-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/sophos-central-source', + 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-1-client-source', + 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/stix-taxii-2-client-source', //'send-data/hosted-collectors/cloud-to-cloud-integration-framework/sumo-logic-kickstart-data-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/symantec-endpoint-security-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/symantec-web-security-service-source', @@ -512,6 +514,7 @@ module.exports = { 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/webex-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/workday-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/zendesk-source', + 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/zerofox-intel-source', 'send-data/hosted-collectors/cloud-to-cloud-integration-framework/zero-networks-segment-source', ], }, @@ -1456,6 +1459,7 @@ module.exports = { 'search/search-query-language/search-operators/sort', 'search/search-query-language/search-operators/substring', 'search/search-query-language/search-operators/threatip', + // 'search/search-query-language/search-operators/threatlookup', 'search/search-query-language/search-operators/timeslice', 'search/search-query-language/search-operators/timeslice-join', 'search/search-query-language/search-operators/tolowercase-touppercase', @@ -3010,6 +3014,21 @@ integrations: [ }, ], }, + { + type: 'category', + label: 'Threat Intelligence', + collapsible: true, + collapsed: true, + link: {type: 'doc', id: 'security/threat-intelligence/index'}, + items: [ + 'security/threat-intelligence/about-threat-intelligence', + 'security/threat-intelligence/threat-intelligence-indicators', + 'security/threat-intelligence/find-threats', + 'security/threat-intelligence/threat-indicators-in-cloud-siem', + 'security/threat-intelligence/upload-formats', + 'security/threat-intelligence/threat-intelligence-mapping', + ], + }, ], api: [ { diff --git a/static/img/platform-services/threat-intelligence-tab.png b/static/img/platform-services/threat-intelligence-tab.png deleted file mode 100644 index bd6e559406..0000000000 Binary files a/static/img/platform-services/threat-intelligence-tab.png and /dev/null differ diff --git a/static/img/security/global-feed-threat-intelligence-tab-example.png b/static/img/security/global-feed-threat-intelligence-tab-example.png new file mode 100644 index 0000000000..0f005981b0 Binary files /dev/null and b/static/img/security/global-feed-threat-intelligence-tab-example.png differ diff --git a/static/img/platform-services/threat-indicators-in-cloud-siem-ui.png b/static/img/security/threat-indicators-in-cloud-siem-ui.png similarity index 100% rename from static/img/platform-services/threat-indicators-in-cloud-siem-ui.png rename to static/img/security/threat-indicators-in-cloud-siem-ui.png diff --git a/static/img/security/threat-intelligence-add-indicators.png b/static/img/security/threat-intelligence-add-indicators.png new file mode 100644 index 0000000000..f7515d0e62 Binary files /dev/null and b/static/img/security/threat-intelligence-add-indicators.png differ diff --git a/static/img/security/threat-intelligence-delete-indicators.png b/static/img/security/threat-intelligence-delete-indicators.png new file mode 100644 index 0000000000..6ed756637f Binary files /dev/null and b/static/img/security/threat-intelligence-delete-indicators.png differ diff --git a/static/img/security/threat-intelligence-tab-example.png b/static/img/security/threat-intelligence-tab-example.png new file mode 100644 index 0000000000..edbc992261 Binary files /dev/null and b/static/img/security/threat-intelligence-tab-example.png differ diff --git a/static/img/security/threat-intelligence-tab.png b/static/img/security/threat-intelligence-tab.png new file mode 100644 index 0000000000..41d647259a Binary files /dev/null and b/static/img/security/threat-intelligence-tab.png differ diff --git a/static/img/send-data/stix-logo.png b/static/img/send-data/stix-logo.png new file mode 100644 index 0000000000..876399ca42 Binary files /dev/null and b/static/img/send-data/stix-logo.png differ}) +
+We’re excited to introduce Sumo Logic Threat Intelligence, a powerful feature set that enables Cloud SIEM administrators to seamlessly import indicators of Compromise (IoC) files and feeds directly into Sumo Logic to aid in security analysis. IoCs are individual data points about threats that are gathered from external sources about various entities such as host names, file hashes, IP addresses, and other known targets for compromise.
+
+Once indicators are ingested and appear on the **Threat Intelligence** tab, Cloud SIEM analysts can use the `hasThreatMatch` function in Cloud SIEM rules to analyze incoming records for matches to the threat intelligence indicators.
+
+Sumo Logic Threat Intelligence will help you stay ahead of emerging threats and enhance your security posture.
+
+:::note
+Only Cloud SIEM administrators can add threat intelligence indicators to the datastore.
+:::
+
+[Learn more](/docs/security/threat-intelligence/about-threat-intelligence).
+
+
+
+We’re excited to introduce Sumo Logic Threat Intelligence, a powerful feature set that enables Cloud SIEM administrators to seamlessly import indicators of Compromise (IoC) files and feeds directly into Sumo Logic to aid in security analysis. IoCs are individual data points about threats that are gathered from external sources about various entities such as host names, file hashes, IP addresses, and other known targets for compromise.
+
+Once indicators are ingested and appear on the **Threat Intelligence** tab, Cloud SIEM analysts can use the `hasThreatMatch` function in Cloud SIEM rules to analyze incoming records for matches to the threat intelligence indicators.
+
+Sumo Logic Threat Intelligence will help you stay ahead of emerging threats and enhance your security posture.
+
+:::note
+Only Cloud SIEM administrators can add threat intelligence indicators to the datastore.
+:::
+
+[Learn more](/docs/security/threat-intelligence/about-threat-intelligence).
+
+}) -
-Like match lists, Threat Intelligence lists are used at the time of record ingestion. When a record is ingested, Cloud SIEM determines whether any of the fields in the record exist in any of your configured Threat Intelligence lists.
-
-When a record contains a value that matches an entry in one or more Threat Intelligence lists, just like with match list data, two fields in the record get populated: a `listMatches` field that contains the names of Threat Intelligence lists that the record matched, and a `matchedItems` field that contains the actual key-value pairs that were matched. In addition, the string “threat” is added to the `listMatches` field.
-
-For example, given a record whose `SourceIp` column matches a entry in My Threat Intelligence List, the `listMatches` field added to the record would look like this:
-
-```sql
-listMatches: \['threat_Ip_My_Threat_Intel_List', 'source:My_Threat_Intel_List', 'column:Ip', 'column:SrcIp' 'threat'\]
-```
-where:
-
-* `threat_Ip_My_Threat_Intel_List` is formed by concatenating the following, separated by underscore characters (_):
- * the string `threat`
- * the type of the column–Ip Domain, FileHash, and so on–in the record that matched an Indicator from the threat intelligence source
-* The name of the threat intelligence source, with embedded spaces replaced by underscore characters (_).
-* `source:My_Threat_Intel_List` identifies the threat intelligence list.
-* `column:Ip` identifies the type of the field where the match was found.
-* `column:SrcIp` identifies the name of the field where the match was found.
-* `threat `is a string that Cloud SIEM uses to indicate that the record field matched a threat source, rather than another type of list.
-
-Because the threat intelligence information is persisted within records, you can reference it downstream in both rules and search. To leverage the information in a rule, you extend your rule expression with the `array_contains` function. The syntax is:
-
-```sql
-array_contains(listMatches, "threat-intel-list-name")
-```
-
-where
-
-`threat-intel-list` is the name of the Threat Intelligence list.
-
-:::note
-If your `array_contains` statement refers to a threat intelligence source whose name contains embedded spaces, be sure to replace the spaces with underscores.
-:::
diff --git a/docs/cse/rules/cse-rules-syntax.md b/docs/cse/rules/cse-rules-syntax.md
index 2748005ee5..ea89e7c44f 100644
--- a/docs/cse/rules/cse-rules-syntax.md
+++ b/docs/cse/rules/cse-rules-syntax.md
@@ -624,6 +624,68 @@ The following expression returns "10.10.1.0":
`getCIDRPrefix("10.10.1.35", "24")`
+### hasThreatMatch
+
+The `hasThreatMatch` Cloud SIEM rules function matches incoming records in Cloud SIEM to [threat intelligence indicators](/docs/security/threat-intelligence/threat-indicators-in-cloud-siem/#hasthreatmatch-cloud-siem-rules-language-function). It can also match values in [Custom threat intelligence sources in Cloud SIEM](/docs/cse/administration/create-custom-threat-intel-source/).
+
+**Syntax**
+
+`hasThreatMatch([
-
-Like match lists, Threat Intelligence lists are used at the time of record ingestion. When a record is ingested, Cloud SIEM determines whether any of the fields in the record exist in any of your configured Threat Intelligence lists.
-
-When a record contains a value that matches an entry in one or more Threat Intelligence lists, just like with match list data, two fields in the record get populated: a `listMatches` field that contains the names of Threat Intelligence lists that the record matched, and a `matchedItems` field that contains the actual key-value pairs that were matched. In addition, the string “threat” is added to the `listMatches` field.
-
-For example, given a record whose `SourceIp` column matches a entry in My Threat Intelligence List, the `listMatches` field added to the record would look like this:
-
-```sql
-listMatches: \['threat_Ip_My_Threat_Intel_List', 'source:My_Threat_Intel_List', 'column:Ip', 'column:SrcIp' 'threat'\]
-```
-where:
-
-* `threat_Ip_My_Threat_Intel_List` is formed by concatenating the following, separated by underscore characters (_):
- * the string `threat`
- * the type of the column–Ip Domain, FileHash, and so on–in the record that matched an Indicator from the threat intelligence source
-* The name of the threat intelligence source, with embedded spaces replaced by underscore characters (_).
-* `source:My_Threat_Intel_List` identifies the threat intelligence list.
-* `column:Ip` identifies the type of the field where the match was found.
-* `column:SrcIp` identifies the name of the field where the match was found.
-* `threat `is a string that Cloud SIEM uses to indicate that the record field matched a threat source, rather than another type of list.
-
-Because the threat intelligence information is persisted within records, you can reference it downstream in both rules and search. To leverage the information in a rule, you extend your rule expression with the `array_contains` function. The syntax is:
-
-```sql
-array_contains(listMatches, "threat-intel-list-name")
-```
-
-where
-
-`threat-intel-list` is the name of the Threat Intelligence list.
-
-:::note
-If your `array_contains` statement refers to a threat intelligence source whose name contains embedded spaces, be sure to replace the spaces with underscores.
-:::
diff --git a/docs/cse/rules/cse-rules-syntax.md b/docs/cse/rules/cse-rules-syntax.md
index 2748005ee5..ea89e7c44f 100644
--- a/docs/cse/rules/cse-rules-syntax.md
+++ b/docs/cse/rules/cse-rules-syntax.md
@@ -624,6 +624,68 @@ The following expression returns "10.10.1.0":
`getCIDRPrefix("10.10.1.35", "24")`
+### hasThreatMatch
+
+The `hasThreatMatch` Cloud SIEM rules function matches incoming records in Cloud SIEM to [threat intelligence indicators](/docs/security/threat-intelligence/threat-indicators-in-cloud-siem/#hasthreatmatch-cloud-siem-rules-language-function). It can also match values in [Custom threat intelligence sources in Cloud SIEM](/docs/cse/administration/create-custom-threat-intel-source/).
+
+**Syntax**
+
+`hasThreatMatch([