|
| 1 | +# OPTIGA™ Trust X |
| 2 | + |
| 3 | + |
| 4 | +Infineon's [OPTIGA™ Trust X](https://www.infineon.com/cms/en/product/security-smart-card-solutions/optiga-embedded-security-solutions/optiga-trust/optiga-trust-x-sls-32aia/) security solution library for Arduino |
| 5 | + |
| 6 | +## Summary |
| 7 | +[OPTIGA™ Trust X](https://www.infineon.com/dgdl/Infineon-OPTIGA%20TRUST%20X%20SLS%2032AIA-DS-v02_18-EN.pdf) is a security solution based on a secure micrcontroller. |
| 8 | +Each device is shipped with a unique elliptic-curve keypair and a corresponding X.509 certificate. OPTIGA™ Trust X enables easy integration into existing PKI infrastructure. |
| 9 | + |
| 10 | + |
| 11 | +## Key Features and Benefits |
| 12 | +* High-end security controller |
| 13 | +* Turnkey solution |
| 14 | +* One-way authentication using ECDSA |
| 15 | +* Mutual authentication using DTLS client (IETF standard RFC 6347) |
| 16 | +* Secure communication using DTLS |
| 17 | +* Compliant with the USB Type-C™ Authentication standard |
| 18 | +* I2C interface |
| 19 | +* Up to 10 KB user memory |
| 20 | +* Cryptographic support: ECC256, AES128, SHA-256, TRNG, DRNG |
| 21 | +* PG-USON-10-2 package (3 x 3 mm) |
| 22 | +* Standard & extended temperature ranges |
| 23 | +* Full system integration support |
| 24 | +* Common Criteria Certified EAL6+ (high) hardware |
| 25 | +* Cryptographic Tool Box based on ECC NIST P256, P384 and SHA256 (sign, verify, key generation, ECDH, session key derivation) |
| 26 | + |
| 27 | +## Hardware |
| 28 | +The wiring to your arduino board depends on the [evaluation board](https://www.infineon.com/cms/en/product/evaluation-boards/optiga-trust-x-eval-kit/) or the |
| 29 | +Shield2GO (link pending) you are using. |
| 30 | + |
| 31 | +## Installation |
| 32 | + |
| 33 | +### Integration of Library |
| 34 | +Please download this repository from GitHub either from the latest [release](https://github.com/Infineon/OPTIGA-Trust-X-Security-Controller/releases) of directly [here](https://github.com/Infineon/OPTIGA-Trust-X-Security-Controller/archive/V1.0.0.zip): |
| 35 | + |
| 36 | + |
| 37 | + |
| 38 | +To install the OPTIGA™ Trust X library in the Arduino IDE, please go to **Sketch** > **Include Library** > **Add .ZIP Library...** in the Arduino IDE and navigate to the downloaded .ZIP file of this repository. The library will be installed in your Arduino sketch folder in libraries and you can select as well as include this one to your project under **Sketch** > **Include Library** > **OPTIGATrustX**. |
| 39 | + |
| 40 | +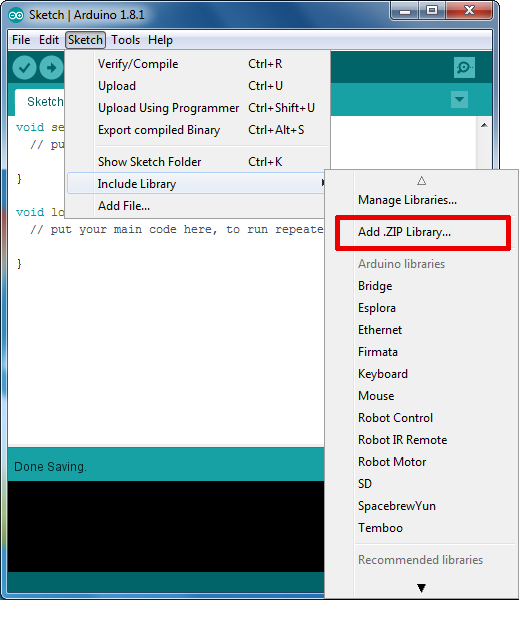 |
| 41 | + |
| 42 | +## Supported Devices |
| 43 | +In general, the library should be compatible with any Arduino board, however it has been tested for the following platforms: |
| 44 | +* Sparkfun ESP32 Thing (Espressif Systems, ESP32, Xtensa) |
| 45 | +* Adafruit Feather M0 (Atmel, SAMD21, Cortex M0) |
| 46 | +* STM32 Nucleo (ST Microelectronics, STM32F0, Cortex M0) |
| 47 | +* XMC1100 2Go (Infineon Technologies, XMC1100, Cortex M0) |
| 48 | +* XMC4700 Relax Kit (Infineon Technologies, XMC4700, Cortex M4) |
| 49 | +* WEMOS D1 mini (Espressif Systems, ESP8266, Xtensa) |
| 50 | + |
| 51 | +## Usage |
| 52 | +The library is equiped with eight groups of examples which can be found on the following path: File->Examples>OPTIGATrustX |
| 53 | +The following sections describe all the examples in more detail. |
| 54 | + |
| 55 | +### selfTest |
| 56 | +selfTest example demonstrates a trustX.checkChip() method usage, which authenticates the OPTIGA™ Trust X on the host MCU. |
| 57 | +This method implements a simple challenge-response authentication scheme, in which the host side authenticates the OPTIGA™ Trust X security chip. |
| 58 | + |
| 59 | +### calculateHash |
| 60 | +calculateHash demonstrates example usage of the SHA256 hash, as well as a simple benchamarking for your microcontroller. |
| 61 | +The performance of this benchmark test greatly depends on I2C bus frame size (it affects mainly big blocks of data transmitted to the OPTIGA™ Trust X chip for hashing), |
| 62 | +which was limited by default down to 32 bytes (in case of 32 bytes the library will perfrom fragmentation). |
| 63 | + |
| 64 | +Please check settings for your specific platform, if you want to improve the performance of the hashing function. |
| 65 | + |
| 66 | +### calculateSignVerifySign |
| 67 | +calculateSignVerifySign demonstrates signature generation and signature verification methods of the library. |
| 68 | +This example shows two modes of operation: |
| 69 | +1) Calculate a signature using manufacturer private key, the result value is then verified against the public key |
| 70 | +2) Generate a public-private keypair and store the latter inside one of Object IDs of the OPTIGA™ Trust X, |
| 71 | +then sign the digest giving only the latter Object ID, the result value is then verified against the public key. |
| 72 | + |
| 73 | +For the verification three methods are available: |
| 74 | +1) with a given raw public key |
| 75 | +2) with Object ID pointing to the memory slot where the public key is located, |
| 76 | +3) if neither Object ID nor raw public key were specified, the function will use a default Object ID with manufacturer public key certificate. |
| 77 | + |
| 78 | +### generateKeypair |
| 79 | +calculateSignVerifySign demonstrates methods for keypair generation, either with a private key export, or without. |
| 80 | +In the latter case the developer should specify the Object ID of the private key. |
| 81 | + |
| 82 | +### getCertificate, getUniqueID |
| 83 | +getCertificate and getUniqueID demonstrate examples of retrievieng various properties of the OPTIGA™ Trust X Chip. |
| 84 | +As well as these examples the developer can also call getCurrentLimit/setCurrentLimit in order to get or modify the |
| 85 | +current limitation of the chip (varies from 5mA by default to maximum 15mA) |
| 86 | + |
| 87 | +### getRandom |
| 88 | +getRandom demonstrates random number generator capabilities. This example outputs random numbers of various sizes (16, 32, 64, 128, 256) |
| 89 | + |
| 90 | +### testFullAPI |
| 91 | +testFullAPI is used to briefly test major API calls to the library. The expected output of this function can be found in Figure below. |
| 92 | +*Certificate output might be different |
| 93 | + |
| 94 | + |
| 95 | + |
| 96 | +## Available functions |
| 97 | +Available API is discribed in Wiki of the repository |
| 98 | + |
| 99 | +## Contributing |
| 100 | + |
| 101 | +Please read [CONTRIBUTING.md](CONTRIBUTING.md) for details on our code of conduct and the process of submitting pull requests to us. |
| 102 | + |
| 103 | +## License |
| 104 | +This project is licensed under the MIT License - see the [LICENSE](LICENSE) file for details |
0 commit comments