Unable to conect to host #686
-
|
Hi team, Hope you are doing well. I got this method to execute scan: def execut_scan(device_id,incident_id, event_type, hostname):
target_aid = get_host_aid(device_id) # Retrieve our test instance's AID
session_id = init_session(target_aid)
response = falcon_rtra.execute_admin_command(base_command="runscript",
command_string=f"runscript -Raw=```Start-MpScan -ScanType QuickScan ```",
session_id=session_id,
timeout=80
)
print(response) the response is: 500onnecting to target When i try to execute the command direct in the web console: I got the below error: Thanks in advance |
Beta Was this translation helpful? Give feedback.
Replies: 3 comments 4 replies
-
|
Hi @hermanmaleiane - A couple of follow up questions:
|
Beta Was this translation helpful? Give feedback.
-
|
Hi @jshcodes Question 1: Yes it's working for other rtr commands. For example when i want to retrieve windows events. `command= "Get-WinEvent -LogName 'Microsoft-Windows-Windows Defender/Operational' | Select-Object -First 2 -ExpandProperty Message | Select" then i get the cloud_request_id and `response = falcon_rtra.check_admin_command_status( I got the response [{'session_id': '3c582a71-87b6-4e47-b041-0d806bf6e8be', 'task_id': '48a77c0b-1cc2-46ff-8de8-9f715c4de7e0', 'complete': True, 'stdout': 'Endpoint Protection client health report (time in UTC):\r\n \tPlatform version: 4.18.2203.5\r\n \tEngine version: 1.1.19200.6\r\n \tNetwork Realtime Inspection engine version: 1.1.19200.6\r\n \tAntivirus security intelligence version: 1.367.1279.0\r\n \tAntispyware security intelligence version: 1.367.1279.0\r\n \tNetwork Realtime Inspection security intelligence version: 1.367.1279.0\r\n \tRTP state: Disabled\r\n \tOA state: Disabled\r\n \tIOAV state: Disabled\r\n \tBM state: Disabled\r\n \tAntivirus security intelligence age: 1\r\n \tAntispyware security intelligence age: 1\r\n \tLast quick scan age: 2\r\n \tLast full scan age: 4294967295\r\n \tAntivirus security Question 3: Retrieves the AID for a given device_id: def get_host_aid(device_id): |
Beta Was this translation helpful? Give feedback.
-
|
Hi @hermanmaleiane! I was able to execute this command against a Windows host using the bulk execute sample we maintain in the Samples library. I had to run the command a couple of times before I got the "A scan is already in progress on this device" message. (I was returned timeouts for the default 30 seconds on the first two tries. We could increase this to probably get around this issue.) Could you try executing the command against a host using this sample? From what I remember of our previous discussion about your code, they should be pretty similar, so I'm curious if this helps us identify a potential syntax issue. Here's the syntax of my command line: python3 bulk_execute.py -k CLIENT_ID -s CLIENT_SECRET -f TARGET-HOSTNAME -c "Start-MpScan -ScanType QuickScan" |
Beta Was this translation helpful? Give feedback.
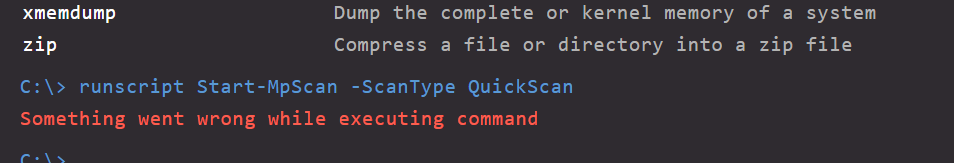
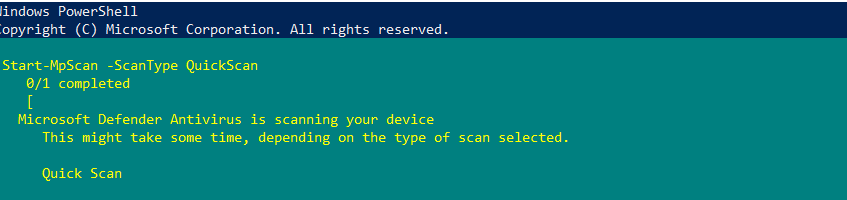
Hi @hermanmaleiane!
I was able to execute this command against a Windows host using the bulk execute sample we maintain in the Samples library. I had to run the command a couple of times before I got the "A scan is already in progress on this device" message. (I was returned timeouts for the default 30 seconds on the first two tries. We could increase this to probably get around this issue.)
Could you try executing the command against a host using this sample? From what I remember of our previous discussion about your code, they should be pretty similar, so I'm curious if this helps us identify a potential syntax issue.
Here's the syntax of my command line: