Need simple example of "After" keyword used in Spotlight Vulnerability query #590
-
|
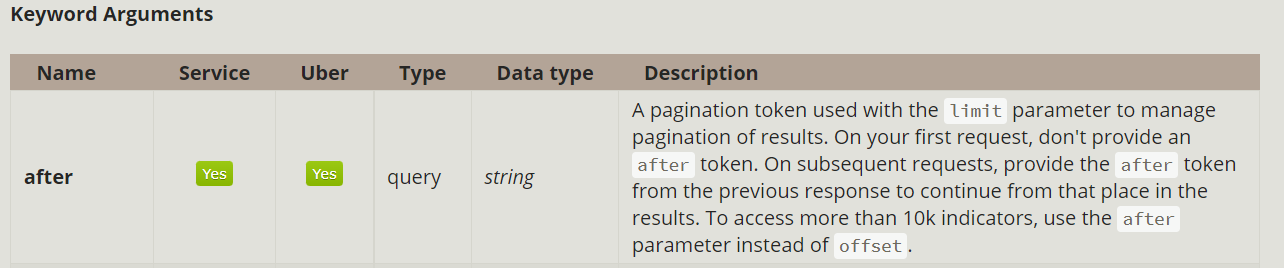
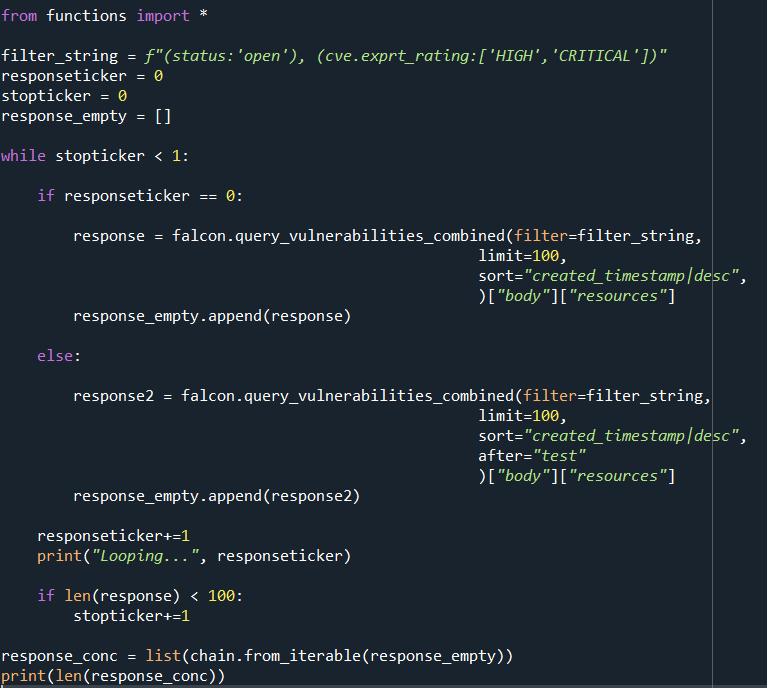
Hello, I'm new to CrowdStrike API and FalconPy. I'm trying to query some data from the Spotlight Vulnerabilities service. In CrowdStrike , we can see a number of vulnerabilities, in the tens of thousands, that are open and have an Expert rating of high or critical. Therefore, I'll need to loop through and make several requests as the limit is around 4000-5000 (although the documentation says 400). At least, I think the limit is much higher than what it says because I don't get an error while using a limit higher than 400. So, I know what I need to do in order to get our full list of vulnerabilities that meet those filtering criteria specified above. However, I can't figure out how to do it. This is what the documentation says: So, you have to use the "after" parameter in the request in order to pick up where you left off, otherwise you'll just get duplicated results. Unfortunately, it's not clear to me how this is supposed to be used. I tried to just use "test" as the After keyword, but this returns a NoneType object. Here's what my code looks like, to give you an idea of what I'm working with: If you need an explanation on my code, I can provide one. It probably looks a bit primitive, but I'm just getting back into Python coding, so my apologies in advance. In my mind, I'm doing as the documentation says below, but clearly I'm wrong as I'm getting an error: On your first request, don't provide an after token. On subsequent requests, provide the after token from the previous response to continue from that place in the results. If anyone could provide an example, that would be much appreciated!! Thank you! |
Beta Was this translation helpful? Give feedback.
Replies: 1 comment 1 reply
-
|
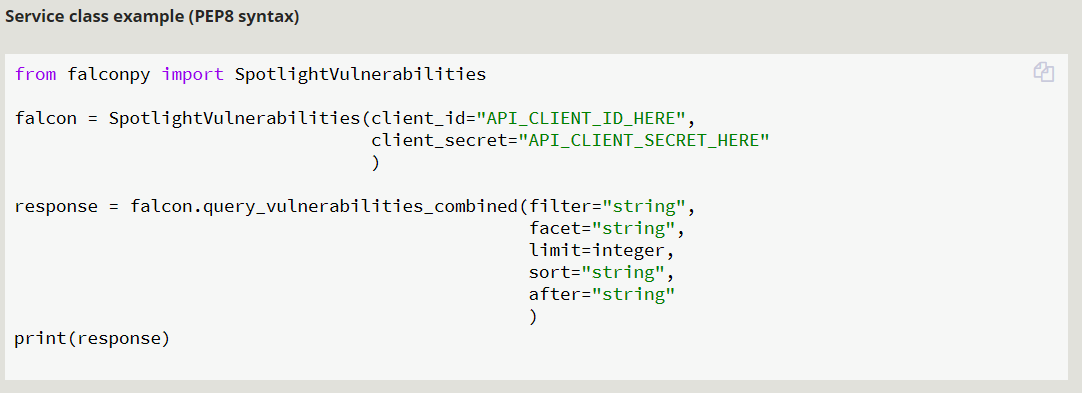
Hi There @lox2095 thanks for the question! I Figured I'd show you a bit of the response I get from the API itself here before I show some FalconPy Examples. For Spotlight we can use the combined endpoint to return up to 5000 records per API call with various facets these can be host details, remediation details etc. the full list is here. Here I'm making a call to the CrowdStrike API to get Vulnerabilities that have been updated (or created) since a certain timestamp
Here's the meta response I get back: "meta": {
"query_time": 0.10787364,
"pagination": {
"limit": 100,
"total": 13378,
"after": "WyJmZGFlOTc3NzBjOTg0NTU3ODM3ZmFkYjc0NjQ1YWNhZF85NjU3Y2MzMmM4NWQzNDFmYjI0MDA4NWQ1MGE3YWU2NyJd"
},In FalconPy this would be a command like: You can see the When using FalconPy you'll need to use the response to check two things: From above these are found in If Condition 1 and 2 are true, you can recursively call Something like this:
Let me know with any follow-up questions! |
Beta Was this translation helpful? Give feedback.
Hi There @lox2095 thanks for the question!
I Figured I'd show you a bit of the response I get from the API itself here before I show some FalconPy Examples.
For Spotlight we can use the combined endpoint to return up to 5000 records per API call with various facets these can be host details, remediation details etc. the full list is here.
Here I'm making a call to the CrowdStrike API to get Vulnerabilities that have been updated (or created) since a certain timestamp
2022-03-08T00:53:13Z'again, one of the many filter options this API has.https://api.crowdstrike.com/spotlight/combined/vulnerabilities/v1?filter=updated_timestamp%3A%3E'2022-03-08T00:53:13Z'Here's the meta response I get b…